As 2025 comes to an end, we’re taking a three-month lookback at the DNS threat landscape. How many threat-related domains were discovered, which new actors emerged and how is the actor toolset evolving during the season?
For newcomers: Domain Name System (DNS) is far more than the telephone book of the internet. It is the backbone that precedes every click, connection and transaction. Without DNS, the internet would simply not function—a fact highlighted clearly during a major cloud provider outage in October.1
View From the Top
Infoblox analyzes over 70 billion DNS queries per day across 13,000 customers worldwide. A significant portion of these customers use our protective security platform, Infoblox Threat Defense™.
Between August and November 2025, this preemptive security offering protected more than 12 million devices per day globally. On average, 648 million response policy zones (RPZs) were applied per day. RPZs act as a powerful defense mechanism—blocking or redirecting DNS traffic tied to malware, phishing or command-and-control (C2) activity.
Between August and November 2025, over 7.6 million new threat-related domains were discovered—a 20 percent increase compared to the previous quarter. More importantly, 85.4 percent of these domains were identified before any user interaction.
This 20 percent growth reflects both the expanding threat landscape and the increasing adoption of our preemptive security capabilities.
Threat actors rely on numerous techniques when generating domains to their advantage. Domain generation algorithms (DGAs) accounted for most of the activity, but we also observed extensive use of lookalike domains, traffic distribution systems (TDSs) and domains configured for tunneling traffic.
Zero-Day DNS Detection
The Infoblox data science team detects in real time newly observed domains not seen across our customer base in the previous 60 days and flagged for high-risk activities such as malicious spam, phishing, lookalike characteristics, DNS tunneling and more.
The daily rate of discovered Zero-Day detections remained steady, averaging between 3,000 and 10,000 domains per day, and none of these domains persist longer than 72 hours. This rapid turnover demonstrates how easily threat actors can replenish and weaponize new infrastructure. For organizations beginning their journey with preemptive DNS security, Zero-Day DNS detections offer an excellent low-regret blocking opportunity—they pose minimal risk of business disruption while significantly reducing exposure.
Threat Actors
Infoblox identifies patterns and commonalities across suspicious or malicious domains. If sufficient evidence across a cluster is found, a threat actor name will be assigned. As of November 15, Infoblox Threat Intel identified more than 258,000 suspicious or malicious domain clusters and over 910 named actors. Three new threat actors were made public this quarter. The most impactful are Detour Dog2 and Vault Viper.3
Detour Dog: Powering Strela Stealer
Detour Dog compromised tens of thousands of websites globally using DNS-based malware. Their attacks operate server-side, meaning visitors see a normal website while the infected site secretly issues DNS queries that allow attackers to redirect visitors or deliver malware. The campaign shifted from simple redirect-to-scam tactics to full malware distribution but only to a very small percentage of victims visiting the infected websites.
Key DNS characteristics:
- The actor abused DNS TXT records as a covert C2 and payload delivery channel.
- Compromised sites make structured DNS TXT requests embedding visitor info.
- In some responses, the DNS server sends back Base64-encoded instructions that trigger the site to fetch and execute malicious code from attacker-controlled servers.
- The DNS-orchestrated malware includes a backdoor (StarFish) and the infostealer Strela Stealer.
Detour Dog’s infrastructure is resilient and stealthy — even after takedown attempts, they recover quickly. In August 2025, attempts to sinkhole their C2 domain briefly interrupted operations, but Detour Dog restored control within hours; analysis of sinkhole traffic revealed ~30,000 infected hosts, with spikes to over 2 million DNS TXT requests in an hour.
Vault Viper: High Stakes, Hidden Threats
Vault Viper represents a large-scale cybercrime operation intertwined with illegal gambling platforms and organized crime in Southeast Asia. What began as an investigation into gambling websites in Cambodia uncovered an extensive ecosystem tied to a major iGaming “white-label” provider.
At the center is the Universe Browser, promoted as a censorship-bypassing “privacy” tool but functioning like malware:
- Routes all traffic through attacker-controlled infrastructure
- Silently installs persistent background programs
- Alters network configurations
- Exhibits behaviors similar to remote access trojans (RATs)
The Windows installer employs anti-VM checks, code injection, persistence mechanisms and keylogging—supporting credential theft and surveillance.
Vault Viper maintains tens of thousands of domains in its DNS infrastructure, enabling global resilience. Researchers used a distinct DNS signature to trace a sprawling network of companies, hosting providers, registrars and servers. The operation intersects with major organized-crime activities including money laundering, fraud, human trafficking and iGaming.
Vault Viper is not just a cyberthreat—it is a convergence point for digital and traditional criminal enterprises.
ClickFix: Tricking Users, Evading Endpoints
While not tied directly to the above actors, ClickFix remains a persistent and high-impact threat. ClickFix is a social engineering technique, not a single campaign or actor. Its purpose is to push victims into a malicious “call to action,” often through fake CAPTCHAs or interaction prompts. Because these elements seem familiar, users click without hesitation—which is exactly what attackers want.
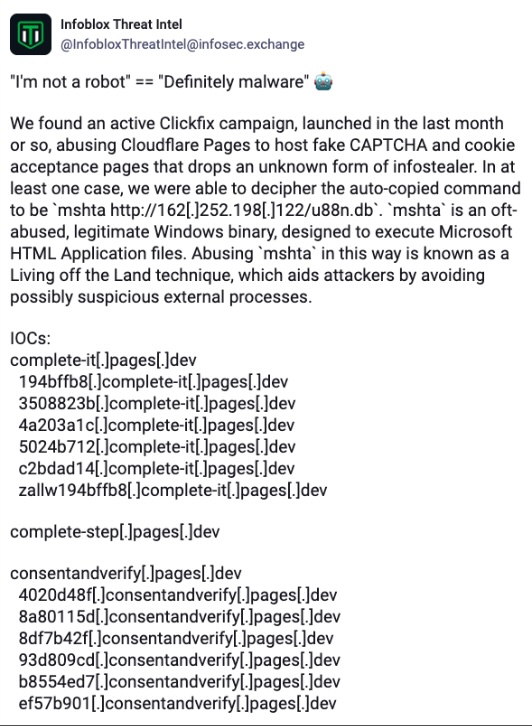
Figure 1. IoCs from Mastodon Channel (@InfobloxThreatIntel)4
ClickFix is particularly dangerous because it is a living-off-the-land technique. Instead of introducing new binaries that endpoint detection and response (EDR) tools can easily detect, the threat actor abuses via ClickFix built-in system tools like MSHTA.
In a recent observed campaign, attackers leveraged the legitimate Windows tool MSHTA to execute commands. To their advantage, most open-source scanning tools (e.g., VirusTotal) did not flag associated domains as malicious and allowed them to continue their malicious operation. As a result, Fake CAPTCHA and ClickFix-style attacks are here to stay.
Holiday Lures and Seasonal Risks
Cybercriminals take advantage of every opportunity to lure victims into their traps, and the holidays are no exception. Every holiday season Infoblox Threat Intel sees a wide range of criminal threats emerging, from fake shops to malware. Domains are registered to look like well-known brands, kits allow scammers to quickly build thousands of fake shops, links in email lead to malware downloads. Easy access to AI to build images and create compelling text content makes it even easier to run these campaigns at scale.
Use of AI Images in Spam Campaigns
We’re also seeing the use of AI images to bolster spam campaigns like using a legitimate email marketing firm and impersonating Amazon. The account has subsequently been suspended (target domains unobtainable).
This demonstrates the use of AI image generation, e.g., the use of the Amazon Smile logo but malformed text (see Figure 2).

Figure 2. Holiday lures
Another holiday theme frequently exploited by threat actors is travel. Those planning to get away over the holidays should stay vigilant for suspicious attachments. Recently, Infoblox Threat Intel has observed high volumes of booking-related phishing emails that prey on travel-minded users.
Subjects:
|
Figure 3. Travel-related subjects used by threat actors
Holidays and vacations can lead to reduced security staffing and delayed countermeasures. With fewer people available, alert queues grow, resulting in slower triage or missed indicators altogether—and attackers often exploit these gaps deliberately. The average dwell time (the period between compromise and detection) increases when teams are understaffed, giving attackers more time for lateral movement and data exfiltration.
Reduced IT and security staffing also means that patch rollouts and testing slow significantly. Many organizations implement a change freeze or adopt a more cautious posture during the holiday period (or fiscal year-end) to avoid operational disruptions. This delays security-critical updates and leaves systems exposed.
The Need for Preemptive Security and DNS-Based Controls
Threat actors have access to an almost unlimited supply of domains and use them to their advantage. Because most threat-related domains are configured days or weeks before an attack, they present an excellent opportunity to proactively block high-risk connections—enabling preemptive security that is especially valuable during periods of increased seasonal risk.
As actors continuously find new ways to deceive both victims and threat researchers, security teams need reliable methods to uncover emerging threats. Identifying malicious infrastructure using DNS intelligence, rather than relying solely on payload analysis, provides significant opportunities for more effective protection and reduces the strain on existing security tools.
Review our End-of-Year Threat Briefing.
Download the Infoblox DNS Threat Landscape Report.
Footnotes
- Amazon reveals cause of AWS outage that took everything from banks to smart beds offline, Taylor, Josh, The Guardian, October 24, 2025. https://www.theguardian.com/technology/2025/oct/24/amazon-reveals-cause-of-aws-outage
- Detour Dog: DNS Malware Powers Strela Stealer Campaigns, Infoblox Threat Intel, September 30, 2025. https://blogs.infoblox.com/threat-intelligence/detour-dog-dns-malware-powers-strela-stealer-campaigns/
- Vault Viper: High Stakes, Hidden Threats, Infoblox Threat Intel, October 23, 2025. https://blogs.infoblox.com/threat-intelligence/vault-viper-high-stakes-hidden-threats/
- https://mastodon.social/@InfobloxThreatIntel@infosec.exchange/115447549140669903









