Using external DNS providers has always been a questionable idea for an enterprise. The Internet Domain Name System (DNS) helps end-user applications acquire the IP address of their destinations. Enterprises want to enforce policy controls regarding Internet access that align with their business needs, and the associated policy controls are most effectively implemented using authorized, internal corporate DNS servers.
Firefox and Chrome have recently begun supporting external DNS resolvers in the cloud. The use of these DNS services bypasses controls that enterprise IT organizations put in place to prevent end users from visiting unauthorized Internet destinations. Compounding the issue is that certain operating systems and browsers use new encryption technologies—DNS over TLS (DoT) and DNS over HTTPS (DoH)—in the query response handshake with these unauthorized DNS services that make them harder to block.
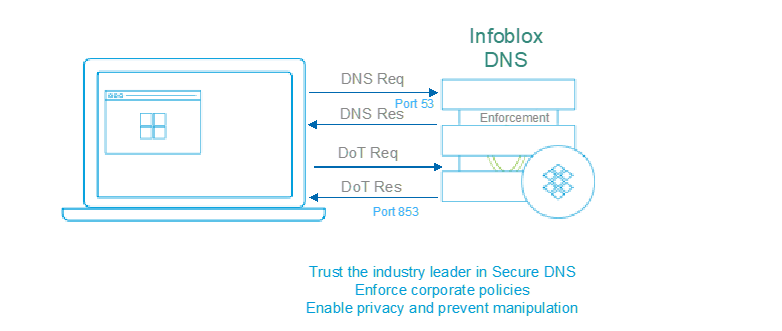
Figure 1: Use Infoblox DoT today
As the industry leader in commercial DNS, Infoblox has the solution to the problem. Organizations can use Infoblox’s recommended best practices to block encrypted DNS queries from end-user devices to unauthorized public DNS services, forcing the devices to fall back to their original and controlled DNS behavior. This approach consistently enforces corporate policy and reduces business risk.
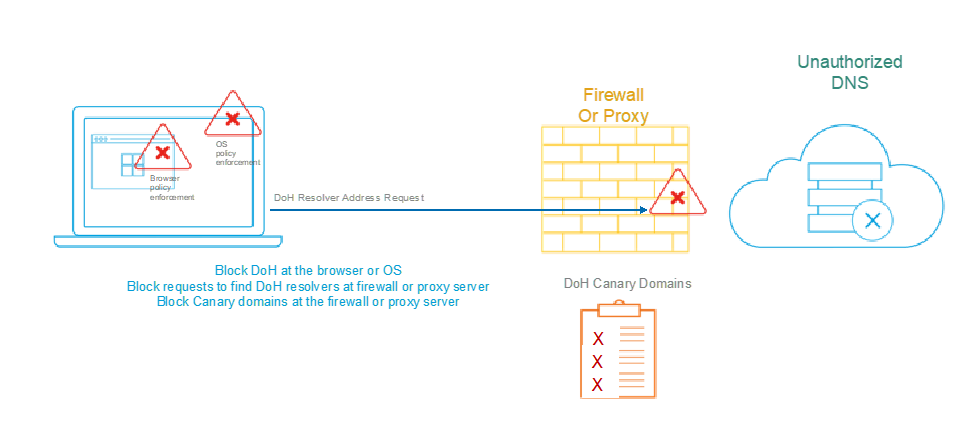
Figure 2: Block DoH today
You can enforce corporate policies blocking access to unauthorized DoH resolvers in several ways: at the application or browser, at the stub resolver in the operating system, at the firewall or at the proxy server in your network. Please refer to Infoblox’s Solution Note on blocking access to unauthorized cloud DNS services to ensure that your corporate security policies are being consistently enforced.
Reference: Solution Note: DoT and DoH Present New Challenges