Author: Mrigank Gupta
The IoT Threat Vector That Should Be on Your Radar, But Isn’t
The Internet of Things (IoT) represents truly world-changing technology. But it also introduces significant cyber risk for security operations everywhere. In this post, we will explore one threat pathway that you likely are not aware of and three common forms of attack that exploit it.
There is no more potent launch vehicle for Industrial revolution 4.0 than IoT. The telemetry data transmitted by IoT’s billions upon billions of Internet-connected sensors and devices make possible radical improvements in the way we deliver better, more personalized healthcare, manage urban infrastructure, run factories, drive cars, keep homes secure and lower the costs for heating and cooling residences and businesses. Increasingly, embedded IoT sensors are being incorporated into jumbo jets, medical diagnostic equipment, industrial robots, drones, CCTV cameras, lighting systems, washing machines, smart watches, fitness bands, baby monitors and thousands of other products. Billions more IoT devices are on the way.
But for cyber security organizations, IoT’s transformational benefits come with one enormous catch: the vast majority of those billions of IoT devices are fundamentally insecure. For many security professionals, this may not be news. It is well known in security circles that most IoT devices ship without traditional security controls. Many “devices” consist of little more than smart microchips. There are no standardized security protocols for IoT products. Most also lack operating systems that can be secured or patched.
As IoT becomes more entrenched in industry and in our homes, cybercriminals are paying close attention. They have skillfully shifted their focus to exploiting IoT’s insecurities. “We observe that as consumers’ interest in smart devices increased, so did attacks,” notes Dan Demeter, a security specialist at Kaspersky. In the first half of 2021 alone, attackers launched 1.5 billion assaults against smart devices to steal data, mine bitcoin or set up botnets, an increase of more than 100 percent over the previous half-year.
IoT’s Hidden Vulnerability: DNS, DHCP and IP Address Management
It is general knowledge among security professionals that IoT devices can be susceptible to physical tampering and brute force attacks. What is far less well known is how the most insidious IoT attacks unfold—and what specific vectors they target. Those vectors include the Domain Name System (DNS), Dynamic Host Configuration Protocol (DHCP) and IP address management. Every IoT-connected sensor has an IP address and invokes DNS and DHCP continuously when transmitting telemetry data. Some of today’s most urgent IoT-based attacks make use of these core network services in their execution.
How IoT Attacks Use Network Services
Most security organizations are unaware that the network services they are tasked with securing have in a few short years become the vectors of choice for malicious hackers and rogue state actors intent on capitalizing on IoT’s vulnerabilities. To understand how threat actors leverage essential network services in IoT attacks, let’s consider a server room used by a large global enterprise.
The room consists of computer servers of various form factors, such as rack-mounted or in tower or blade enclosures. Each server incorporates sensors that communicate the server’s temperature status continuously over the Internet. That temperature data is conveyed over DNS. Server temperatures increase when under full load. Cybercriminals who know how to hack into DNS traffic can monitor those temperature changes. They can then time their attacks against those servers to coincide with when the servers are operating at full capacity, hence maximizing the damage from attacks.
Three Common IoT Attacks That Exploit Essential Network Services
Three of the most common IoT-based cyber threats that target essential network services include distributed denial-of-service (DDoS), man-in-the-middle (MITM) and ransomware attacks. Here’s a quick look at each and how they work.
IoT DDoS Attacks
A common form of IoT-based DDoS attack targets the DHCP protocol. DHCP is used to automatically assign IP addresses to endpoints. For our purposes, that would be any IoT device on a network. To assign IP addresses, DHCP uses packets of data consisting of various messages, including a category called Discover messages.
In an IoT-based DDoS attack, threat actors use what are known as DHCP starvation tactics. An attacker floods fake or spoofed DHCP Discover messages with spoofed MAC addresses. In an attempt to assign IP addresses, the DHCP server will in turn try to respond to all of these bogus Discover messages. In the process, the DHCP server’s pool of IP addresses is exhausted by the spoofed requests. As a consequence, no legitimate user can get an IP address assigned through DHCP. The end result is a DDoS attack that essentially takes the network down.
IoT Man-in-the-Middle Attacks
A man-in-the-middle (MITM) attack is a general term for when an attacker disrupts the conversation between a user and an application. Information is on the way. The purpose of the attack is to steal personal information such as login credentials, account information, and credit card numbers. Targets are most often users of financial applications, SaaS companies, e-commerce websites, and any other website that requires a login. Information captured during an attack can be used for a variety of purposes, including identity theft, unauthorized money transfers, and unauthorized password changes. MITM can gain a foothold within a secure perimeter during the intrusion stage of an Advanced Persistent Threat (APT) attack.
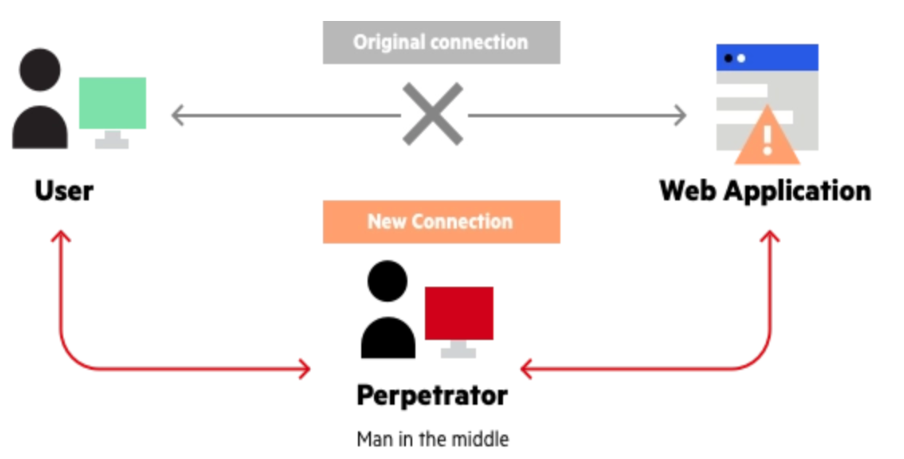
IoT gives threat actors endless avenues to perpetuate MITM attacks. For instance, in the DDoS example above, imagine if an attacker were to set up a rogue DHCP server to assign IP addresses to legitimate users. This bogus server can also provide users with gateway routers and DNS servers. All network traffic can then be routed through the attacker’s machine, placing the attacker squarely in the middle of all communications between devices and destinations, free to insert APTs or other forms of attack.
A type of IoT attack closely related to MITM is data eavesdropping. Let’s say eavesdropper, E, taps into the messages and commands in the network during communication (via DNS and DHCP traffic) and obtains confidential messages. A server at E sends fake commands that a server, S, assumes are from legitimate devices or applications. S issues responses for the device operations in response to requests from E. E listens to these responses. A fake device at E can then be used to send the device data, such as sensor data, requests, and commands from E for disrupting, say, a control system.
IoT Ransomware Attacks
Ransomware is among the most notorious IoT cyber threats. In this attack, hackers use malware to hold an organization’s critical data hostage through encryption or to adversely affect assets on the network. Threat actors agree to decrypt the data or to stop manipulating assets only after receiving ransom money.
To imagine how such an attack works, we need only look at the server room example we talked about earlier. Researchers have revealed the potential impact of ransomware using an IoT-connected smart thermostat. In one demonstration, researchers showed how attackers can gain remote control of the thermostat (by way of network services communications) and raise the temperature of the server room, putting server functionality at risk, until a ransom is paid.
Similar ransomware attacks can target smart home devices. In this scenario, attackers send notifications to homeowners to pay ransom to regain control of their IoT-connected systems.
Defending Networks against IoT Attacks
With IoT, security operations face a daunting challenge. They have to find ways to protect thousands of inherently insecure IoT devices, devices that in many instances inadvertently provide attackers with an opening into the network. While it is impossible to adequately secure IoT devices themselves, security teams can harden their networks against IoT threats by simply securing the essential network services, including DNS, DHCP and IP address management, that attacks require in order to execute. The right security solutions make these services inherently secure and stop IoT attacks in their tracks.








