Last week the tech IPO scene was hot, with the FireEye and Rocket Fuel IPO fueling the fire (pun intended).
It was a spectacular show and hardly anyone was surprised. The only differences of opinion were around what led to the spectacular success. Beyond the obvious leadership, timing, and being at right place at right time, the one that caught my attention involved the partner strategy.
At a dinner with one of a prominent security VARs, someone pointed out that partnerships were critical from the stickiness perspective that led to the growth and market capture for FireEye over the last two years. In our earnings call for FY2013, Infoblox announced a similar partnership with FireEye (an extension of our DNS Firewall use case, which we discussed in an earlier blog). This was a classic example of customer-driven partnership and product development.
The need for this kind of partnership is illustrated by the diagram below, which shows how, at every stage of the APT propagation, there is a DNS query to a malicious destination.
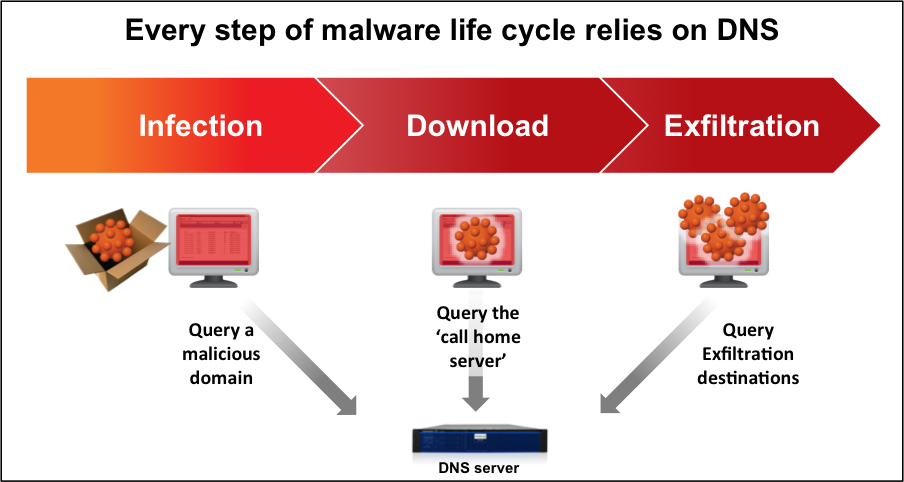
There may be several different stages and steps, but at the core there is a dropper download, calling home to get instructions or to exfiltrate data to an Internet destination. In every query, the way the malware client finds its destination is by looking for the domain name. It can obviously have an IP address in there to reach out directly, but most bad domains use techniques like fast fluxing at the backend that allow the domain names to be hosted and brought down at very high speed. Using IP addresses makes that hard to do and in addition takes away the flexibility to use infected grandma’s PC that uses DHCP.
We provide malware data feed service to our customers by identifying malware hosting destinations on the Internet. This works well for the known threats and botnets that are out there. However, APTs are different and unique in terms of how they operate. An APT is a targeted and tailored attack on a specific organization. As a result, the activity around it looks like a perfectly normal connection that is being made to a server on the Internet. Normal malware detection systems and research don’t get triggered because the activity appears fairly benign.
This is where FireEye’s Virtual emulation technology and APT detection capabilities play a critical role. As FireEye identifies these organization-specific threats, a notification is sent to the DNS Firewall with the details on the domain. Any effort to reach to that destination is blocked from that point onward, containing the APT and preventing other clients from getting infected.
The Infoblox IPAM solution with DHCP fingerprinting capability takes this to the next level by helping IT teams to quickly identify the infected source so that necessary remediation can be provided.
So we’re looking forward to releasing this integration between Infoblox and FireEye, and congratulations to our partner in (mitigating) crime, FireEye, for the great Wall Street score!





