Current measures won’t work for the long-term
A global survey by Osterman Research, conducted almost a year into the pandemic, asked security leaders about their long-term plans for endpoint security in the wake of the lessons learned from their initial response. The results were often surprising.
First, it was great to see that security leaders around the world proved worthy of their pay as COVID-19 emerged, forcing an almost over-night shift to a massive ‘work-from-home’ posture. Respondents overwhelming reported that, while some productivity and IT functions suffered, they were able to maintain a significant level of security despite facing new challenges with near-zero warning. Almost half of respondents reported that the effectiveness of their endpoint security changes delivered a significant if not major improvement in security, to the extent that many believe their remote workers are more security today than they were pre-pandemic.
It was interesting that, while most survey results were reasonably consistent globally, there were some regional differences regarding the early impact the pandemic had on key areas of their organizations. Here is one of the charts from the report showing this regional disparity.
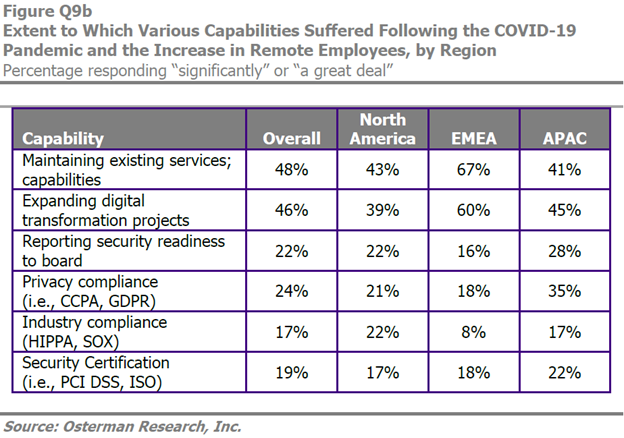
To minimize risks overall, security leaders relied on well-known technologies even thought they were never designed, deployed, or configured for the scale of the situation, such as VPN. Many respondents reported performance, stability and other core challenges that are driving them to consider other options. As a result, security personnel found themselves spending more time simply maintaining these systems. Again, VPN showed most prominently as creating a ‘hassle’ for users as well those responsible for setup and maintenance (32% of respondents).
So, despite having performed a miracle securing their organization under unprecedented situation, respondents have determined that the current measures are not sustainable for the long-term and are looking at alternatives.
Respondents considered 18 different areas of technology they felt could help them reduce their reliance on VPN, identifying which ones they used today as well as those they are looking to acquire, deploy, or expand to support the work-from-anywhere reality they have accepted as the future for their organization. Osterman noted in this section of the report that:
“Among the solutions that will be acquired or deployed by the fourth quarter of 2021, the leading solutions are Cloud Application Security Brokers (32 percent), DNS security (26 percent), and next-generation firewalls (22 percent).”
I was obviously please that, among these three, the only one that also appeared in the top three on the other lists was DNS Security. Regardless of their location, endpoints require DNS to connect to any application, service, or data source, and malware needs DNS at multiple stages of an attack. With the proper tools, DNS can provide the visibility necessary to block attacks other defenses do not see, improve breach detection, and drive faster and more effective incident response.
Now no one expects a single solution to solve the problem. Each organization needs to review this entire list and evaluate their current investment and use of the technologies noted by their peers in this survey. For example, while IAM didn’t make the top 3, it was a close #4 to NGFW, and it is clear that stolen credentials remains one of the most common early stages of an attack making that a critical technology adoption. But DNS security is likely in the top three because it is an established, foundational technology. Tapping it for a greater role in security is a low-risk investment with high-potential.
If you would like to know more about how others are looking at a more sustainable endpoint security strategy, you can access the full survey report, or watch the webinar with Michael Osterman, founder and president of Osterman Research.








