Google recently asked one of its portfolio companies, VirusTotal, to sift through global ransomware data collected from the samples submitted to their portal over the last few years to uncover data points and trends that traditional threat reports simply don’t reveal. While there is some interesting information to be gained from this report, we should start with a warning:
The “Ransomware in a Global Context” report from VirusTotal is based on samples submitted to VirusTotal by analysts and other security professionals. But ‘submissions’ do not equate to detections, infections, investigations, or even breaches. In many ways, this is a ‘usage’ report of VirusTotal services and not a threat report.
Keep a few things in mind, and you’ll do fine
With that said, this blog is not intended to disparage the report. In fact, many of the report’s findings are truly interesting and may guide security teams in both general and specific areas. But in a world with so many threat reports it is easy to develop an automated response about how to interpret certain kinds of charts and tables. For example, look at this chart from the report labeled as “Geographic distribution of ransomware-related submissions”.
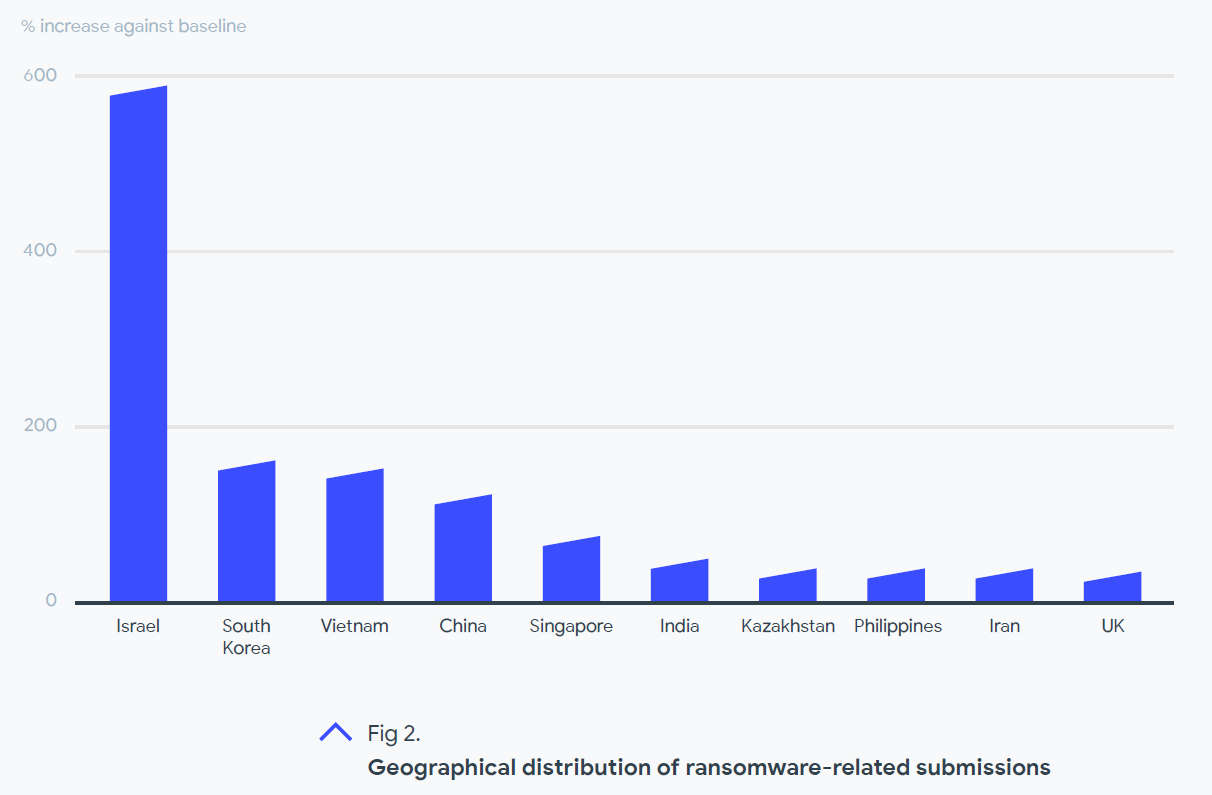
A magazine article based on this chart claimed that “Israel has submitted the largest amount of ransomware samples since the start of 2020.” But that is not what this chart is showing. This is about which countries have ‘increased’ their use of VirusTotal the most since 2020. It is measuring a delta, not total usage. So, if I was working for VirusTotal, this would tell me I could reduce my marketing budget in Israel because VirusTotal is already growing strong there. But it tells me little about ransomware activity or what I can do to improve my security.
Readers note: This is the last chart I plan to include here. If I post all the pretty pictures here, you’ll miss some of the context I’m unable to include due to time, space, and typing endurance limitations. So read the full report.
Death, Disaster, and Drama Rule!
It is apparent from figure 1 in the report that about half of all the ransomware submissions over this 21 month period took place in the first 6 months of 2020. This means recent data is diluted and the report has little to offer about how ransomware has changed recently. But the early 2020 spike aligned with the start of the global pandemic when cyber criminals were creating many COVID-19 themed attacks using both old and new techniques and methods. SecOps were erring on the side of caution due to work-from-home and other shifts in business processes, resulting in submissions of anything suspicious. So it would make sense that VirusTotal would see many more submissions than usual.
And this underscores the role of “death, disaster, and drama” in driving threat actor activity. Global or regional events around these themes are big drivers for cybercriminals who have an attack ready to go and are just waiting for the right opportunity. They want a theme that will cause stress in victims where they are proven to be more susceptible to social engineering. For example, about 10 years ago a Tsunami hit Japan with devastating consequences which cyber criminals used to attack both victims and those trying to help. This approach worked so well that, a few years ago, one cybercriminal group faked a tsunami in an effort to target Japanese citizens. And there are plenty of other examples of attacks using the death of a celebrity, drama around anything raging in social media, and so on.
Watch the news because it might just tip you off to a new wave of threats.
Exploits are not as common as you think
The VirusTotal report says only 5% of the submitted samples contained an exploit, or code designed to take advantage of an application or system vulnerability. While it is generally understood that social engineering remains the most successful tool for bypassing security, this 5% number appears deceivingly low. This is because the VirusTotal data includes a lot of known threats (see figure 5 in the report), and there is no sample breakdown into ‘successful’ and ‘unsuccessful’. So we must look at other threat reports where many security vendors conclude that ‘exploits’ are a common element of successful ransomware attacks. So, while 5% of overall samples may involve an exploit, it is more likely that more than 5% of ‘successful’ ransomware samples involved exploits.
Regardless of how bad the problem may be, there are plenty of options to consider to address exploits. And, while security professionals know that you cannot simply match up a threat category with a security solution category, here are a few thoughts to keep in mind as you consider how your current defenses address this area of risk.
- Both patching and vulnerability scanning should remain top priorities. And scheduling scans as well as automating scans on incident detection, just to ensure analysts have as much current data about an affected system as possible to speed triage and investigation.
- Social Engineering isn’t all about phishing. While it is a general understanding that around 90% of all attacks involve email phishing, make sure users are aware of other ways it is used against them. Fake websites, links on waterhole sites, and malvertising continue as top risks. And Lookalike URL usage in all of these attack vehicles is growing to counter users who are being better trained on how to check the true destination of links in email and in a browser.
Actors are not families
Due to the long period covered by the VirusTotal report, it is hard to make out some details from this data alone. However, combined with other data on specific threats, the VirusTotal report helps to shed additional perspective. We’ll drill into the Gandcrab ransomware family which saw more sample submissions than any other.
Additional research into Gandcrab’s history and the chain of attack behaviors reveals that it was first seen in 2018, and saw a great deal of success in the first half of 2019. But, in June of 2019, the threat actors behind Gandcrab announced that they would be shutting down their operations. So why would a piece of ransomware that essentially ‘shut down’ 6 months before the beginning of this report period be of such interest to security analysts and researchers using VirusTotal?
It is because the actors only shifted their focus to a sister family of threats that became known as Sodinokibi and, later that year, officially reemerged with a name you may be more familiar with, REvil, which achieved fame through their Kaseya attack. All 3 families are listed independently in the report in figure 5 since VirusTotal broke the data down by malware family, which has nothing to do with the ‘actors’ behind them. Unfortunately, you wouldn’t know this if you didn’t do additional research.
But looking at these three ransomware families on the figure 5 bar chart reflects how experienced security analysts and researchers do their homework. If a researcher recently had to deal with a REvil launched attack, or were simply concerned about the possibility, they also looked at both Sodinokibi and Gandcrab to understand as much about the actors as they can. And with so many samples available for Gandcrab and its variants, it makes sense that there would be many more ‘submissions’ for the Gandcrab family as part of this research. They do this because, in this case, past behavior is an indication of future performance.
Also of note, just as they disappeared after achieving too much success with Gandcrab, they have pulled the same disappearing trick this year with REvil as well, twice! The US government shut them down the last time. And we saw the same thing with the DarkSide shutdown after their Colonial Pipeline breach. Overall, threat actors are getting better at knowing when to run and hide.
A final lesson: Don’t let the headlines distract you
There have been many ransomware threats that have made the headlines over the last two years. But the VirusTotal report shows that researchers submitted samples from 130 different ransomware families during the report period. That means there are a lot of existing threats beyond the handful that make the headlines. It is vital that leadership be aware of this disparity to give them pause the next time they read an article about some new threat and have an urge to have everyone focus on it.
Knowing what to focus on in security isn’t easy. Maintaining a comprehensive view of the threat landscape and your security options will require reading more than a report. Listen to podcasts, attend events, seek out analyst reports on security strategies and technology, threat intelligence, and short-term threat reports to give you a sense of what is happening now. Find a blend of sources that fit your need, subscribe, and stay on top of them to keep your skills and security profile as strong as possible.








