Many DNS-as-a-Service (DNSaaS) providers were initially impacted by a vulnerability that may be allowing threat actors to access sensitive information from within corporate networks. Initially this flaw was presented at the recent BlackHat security conference by security researchers Shir Tamari and Ami Luttwak of Wiz.io. The good news is that Infoblox was not vulnerable to this type of attack.
The Wiz.io team presented a vulnerability that allowed them to intercept a portion of the worldwide Dynamic DNS (DDNS) traffic going through managed DNS providers like Amazon and Google. DDNS is a process that automatically updates a name server in the Domain Name System (DNS), typically in real time, with the active DDNS configuration of the configured hostnames, addresses or other information. DDNS updates are DNS messages that workstations send to DNS servers when their IP address inside the internal network, or other details, have changed.
In essence, the loophole vulnerability allowed the threat researchers to intercept or “wiretap” the DNS traffic from over 15,000 organizations, including Fortune 500 companies, 45 U.S. government agencies, and 85 international government agencies.” The information gathered includes a lot of high value data including computer names, employee names, employee locations, web domain information including entry points that are exposed to the internet.
The Wiz.io team was able to add the managed DNS provider’s name server itself inside the backend and point it to their internal network. This allowed the Wiz.io team to effectively hijack DNS traffic hitting the hijacked managed DNS provider’s server. They did not receive all DNS traffic going through that server – only the dynamic DNS updates. The Wiz.io team noted that they could not get the data from a company’s real-time DNS traffic, the DDNS updates did allow them to essentially map the companies and their internal networks that were using the same managed DNS server.
This vulnerability allowed Wiz.io to collect a massive amount of data in a short period of time. Some of the data also could allow threat actors to improve the precision of targeted attacks. This was done by determining the structure of the high-value targets, identifying domain controllers, which in turn could enable the launch of cyberattacks with improved precision.
Wiz.io provides a free DDNS leak tester which can help alert you to the vulnerabilities that might exist within your architecture here: https://dynamic-dns-checker.tools.wiz.io/
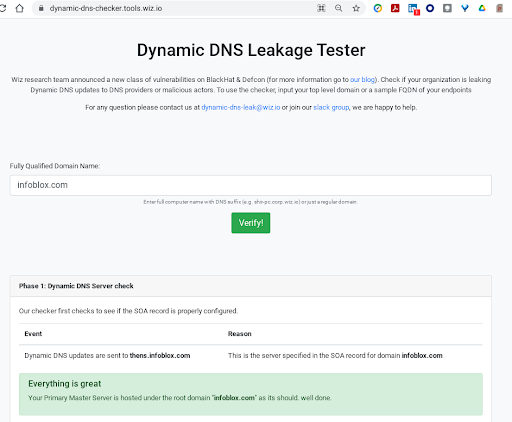
Regaining Visibility and Control of Your Primary Name Server
In this particular scenario, threat researchers registered domains they did not own inside of the cloud provider, and were able to create any zone inside of the hosted cloud provider. The researchers were able to register a host with the exact name of the cloud provider’s name servers. This shows that organizations need to control the domain of their primary name server to avoid hijacking of those servers. It also highlighted that cloud service providers need to ensure that certain domains could never be created.
Moreover, when endpoints (in this situation, Windows machines) are allowed to send Dynamic DNS requests to a DNS server not controlled by the organization, you lose visibility of where they are going and what they are doing. Best practice is to leverage an endpoint agent that routes DNS traffic to a company owned DNS service for better visibility, security and control, on and off-premises.
Talk to us about your DNS infrastructure – reach out to https://info.infoblox.com/contact-form.








