The widespread IT outages caused by the Crowdstrike updates to Windows machine was a timely wake up call to the fragility of the complex IT systems the world economy relies on. The impact was demonstrable and very real to businesses and their customers. This jolt to the system created a crisis as business users struggled to know how to react as their systems ground to a halt. With limited information to hand, it was inevitable that some turned to online sources to get their systems back up and running.
Sadly, what was also inevitable was that this crisis would be turned into an opportunity by the cybercriminal economy. Within hours domains with tempting names such as crowdstrike-apocalypse[.]com and crowdstrikefix[.]in were registered in an attempt to exploit the panic and users’ desperation to get their systems fixed. In some cases, these sites were not quite ready to provide a convincing façade to fool users but enough of them did.
Infoblox Threat Intel quickly identified several lookalike domains related to Crowdstrike and included them in our feeds to protect customers:
- 194 crowdstrike lookalike domains were detected between 2024-07-19 and 2024-07-23.
- By July 24th, Infoblox customers had access to 94 unique crowdstrike lookalike domains across four RPZ feed categories: antimalware, suspicious-lookalikes, suspicious-noed, and suspicious
- 60 lookalikes that are likely used in phishing were discovered and submitted to our threat intel platform
- 27 domains likely used in malicious activities were discovered and submitted to our threat intel platform
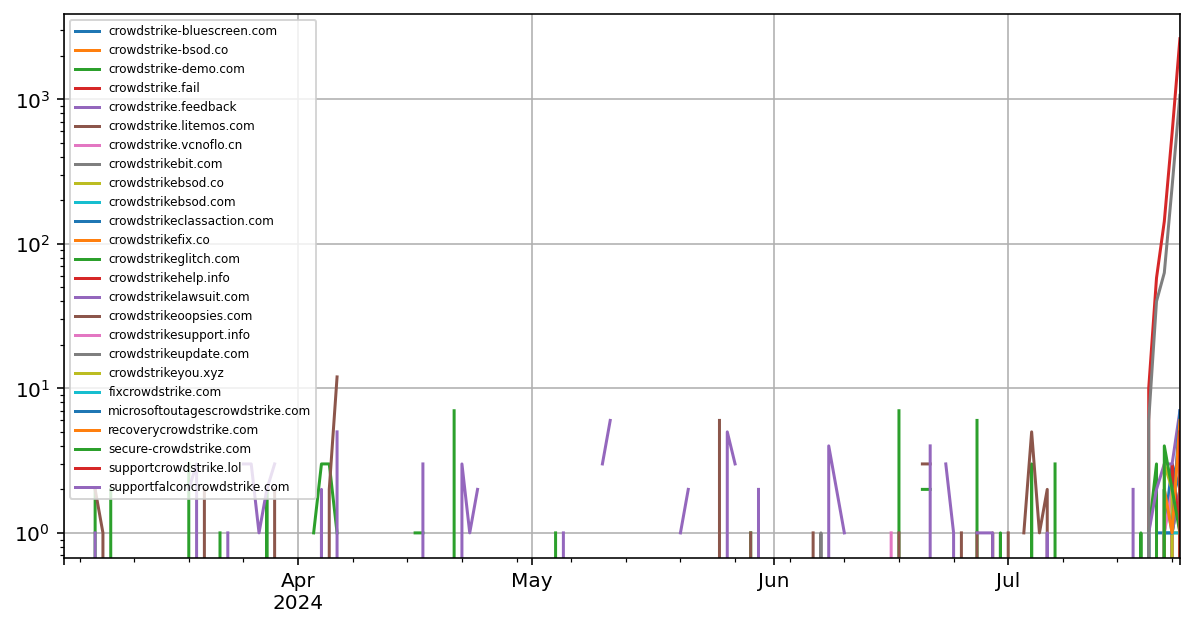
|
| Figure 1: Activity of domains that have high risk score and have been active in the past few days |
Important Takeaways
The key takeaways from this are twofold. The first is the speed by which cyber criminals can exploit a crisis with a simple and fast registration of lookalike domains. With no time to warn or educate users, it highlights the need for proactive action against these threats. Users simply cannot be expected to be on their guard 100% alof the time. Fortunately, Lookalike domain monitoring is a service that allows organizations to identify new domain registrations that seek to impersonate or associate themselves with an unrelated organization or brand. By registering for these services, IT organizations can quickly detect opportunistic attacks and the domains used to target their users.
The second takeaway is the need to marry those lookalike domains to threat validation and mitigation. Lookalikes alone will identify domains similar to the target under threat, but how can you be sure that these new domains are not the target organization trying to respond to the crisis? This is where an understanding of the underlying DNS infrastructure can come into play.
Staying Protected with DNS Threat Intel
At Infoblox, we monitor for target lookalike domains. Once identified, they are matched against our extensive set of threat intelligence. That intelligence includes high risk domains that are considered suspicious based on domain characteristics and behavior that suggests malicious activity is imminent. These high-risk domains could have only recently become active and share one or more characteristics with other known malicious domains and hence raise concerns. They also include lookalike domains that appear to mimic other familiar domains but have exhibited enough anomalous behavior to cause concern.
These domains may not have been used in malware campaigns yet but are associated with known threat actor infrastructure. With many of these opportunistic attacks, the threat actor will use some well-established threat actor infrastructure or register the domains on less than wholesome DNS registrars. By marrying up the lookalike domains and the underlying DNS threat actor infrastructure it allows Infoblox to add these suspicious lookalike domains to a threat feed that can be automatically applied to DNS infrastructure. Any user who tries to reach these domains will have their DNS requests denied, preventing them from accessing the fraudulent site.
This threat intelligence is used in Infoblox Threat Defense to protect customers against attacks such as lookalike domains, ransomware, phishing and more. The threat intelligence can also be automatically shared with other control points in an organization’s security ecosystem such as firewalls and gateways, to empower them to block these threats, making the ecosystem tools more effective and providing organizations with consistent policy enforcement.
The Crowdstrike outage is unlikely to be the last, providing cyber criminals with ample opportunities to exploit these crises. With a proactive approach, organizations can help protect their users in times of crisis by leveraging DNS and DNS based threat intelligence.
To get a flavor of the Lookalike landscape in the aftermath of the Crowdstrike outage check out this blog “Let’s Be Careful Out There” from Cricket Liu








