The MITRE ATT&CK™ framework, developed by The MITRE Corporation, is a comprehensive knowledge base of cyber attacker tactics and techniques gathered from actual observation of attacker behavior. The MITRE Corporation is a nonprofit organization which was founded in 1958. MITRE does work for U.S. Government agencies in a wide variety of areas. MITRE ATT&CK (Adversarial Tactics, Techniques, And Common Knowledge) was developed and released by Mitre Corp. in 2015.
As an important knowledge base, MITRE ATT&CK enables anyone on the cyber defense team to review and contrast attacker activity, and then understand the best options for defense. So you know, there is also MITRE PRE-ATT&CK, which helps cyber defenders prevent an attack before the attacker can gain access to the network. The 15 top-level tactic categories for PRE-ATT&CK correlate to the first two stages of the Lockheed Martin Cyber Kill Chain®. PRE-ATT&CK presents the tactics, underlying techniques, and procedures that a cyber attacker will use to define targets, gather information, and then launch an attack.
Given the greatly increased porosity of the perimeter, the movement to the cloud and mobile devices, and the greater ability of attackers to morph and change tools that were previously found by static signatures, it is likely that at some point an attacker will successfully penetrate your network. Given this assumption, a detailed focus on attacker behavior, such as provided by MITRE ATT&CK, is the best way to find and stop an ongoing attack before data exfiltration or destructive behavior can be achieved.
MITRE ATT&CK brings a common lexicon to describe the activities of cyber attackers, and the step-by-step tactics and techniques which they will use. This enables you to communicate clearly with others in the cyber defense community on the exact details of the threat. ATT&CK also provides a strong framework for describing your current security controls and processes. At a very basic level, MITRE ATT&CK allows the security operations defenders to clearly identify the nature of a threat, map that threat back to the controls that should protect against it, and then ultimately determine whether or not that control is effective.
Sources of reliable data used by MITRE to develop the knowledge base included malware samples, security conference presentations, threat intelligence reporting, and a variety of other public and private sources including social media, blogs, and webinars.
Red teams and the techniques that they use have also been an excellent source of data.
The MITRE ATT&CK framework provides a comprehensive taxonomy to post-exploitation cyber attacker behavior. A detailed focus on attacker behavior, such as provided by MITRE ATT&CK, is the best way to find and stop an ongoing attack before data exfiltration or destructive behavior can be achieved. This helps you balance your defensive measures against the steps an attacker will take. The end goal in using MITRE ATT&CK is to make better decisions about assessing risks, deploying new security controls, and better defending your network. MITRE ATT&CK has segmented attacks in a very consistent way that makes it easy to compare them and to determine how an attacker might have exploited your network. Most attacker analysis focuses on their activities in terms of perimeter defense. MITRE ATT&CK takes a much closer look at them once they get in.
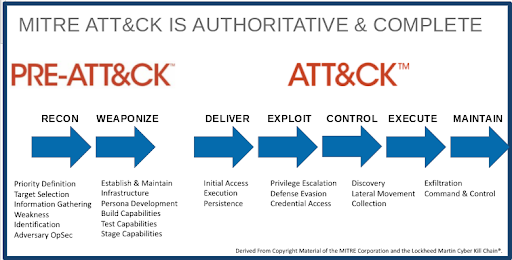
MITRE ATT&CK is presented as a series of easily navigable matrices that contain critical information about attacker behavior. This information includes attacker Tactics, Techniques (& Sub-techniques) and Procedures.
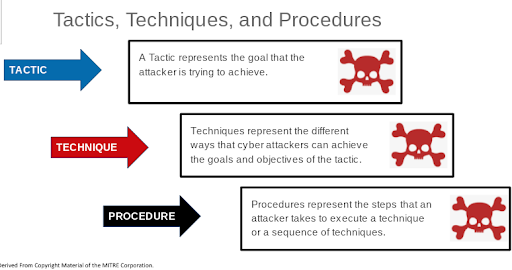
This can be logically represented in the MITRE ATT&CK matrix with column headings (Tactics), row entries under each column (Techniques), and the steps the attacker takes to execute one technique, or perhaps to string together a bunch of techniques. These steps are called the Procedures. Together these represent the Tactics, Techniques, and Procedures (TTP’s) of the attacker.
Now we can look at all of the Tactics, one at a time, and determine which techniques & sub-techniques utilize or rely on DNS to move the attacker closer to their goals. Here is the full list of MITRE ATT&CK enterprise tactics in this graphic:
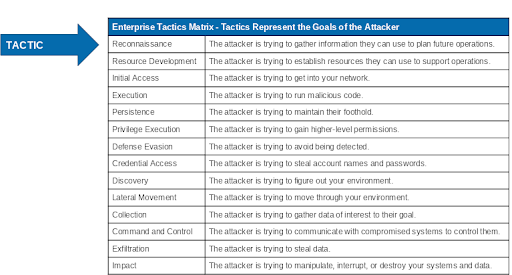
Now lets focus in on those that impact or touch DNS in any way.
Here is just the Reconnaissance Tactic:
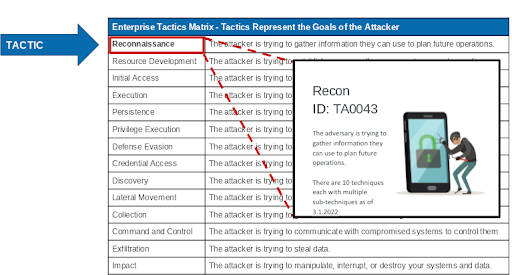
And here you can see which techniques under Reconnaissance utilize DNS.
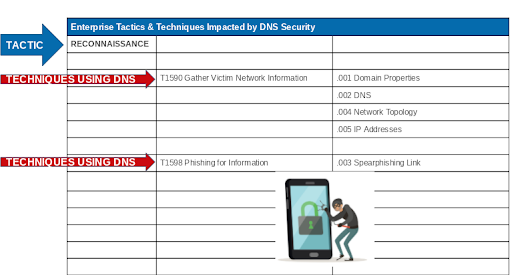
This is the specific detail of these techniques & sub-techniques provided by MITRE. You can see why you need a modernized DDI environment and why using DNS security is so important:
T1590. Gathering Victim Network Information. Adversaries may gather information about the victim’s networks that can be used during targeting. Information about networks may include a variety of details, including administrative data (ex: IP ranges, domain names, etc.) as well as specifics regarding its topology and operations.
- .001 Domain Properties. Adversaries may gather information about the victim’s network domain(s) that can be used during targeting. Information about domains and their properties may include a variety of details, including what domain(s) the victim owns as well as administrative data (ex: name, registrar, etc.) and more directly actionable information such as contacts (email addresses and phone numbers), business addresses, and name servers.
- .002 DNS. Adversaries may gather information about the victim’s DNS that can be used during targeting. DNS information may include a variety of details, including registered name servers as well as records that outline addressing for a target’s subdomains, mail servers, and other hosts.
- .004 Network Topology. Adversaries may gather information about the victim’s network topology that can be used during targeting. Information about network topologies may include a variety of details, including the physical and/or logical arrangement of both external-facing and internal network environments. This information may also include specifics regarding network devices (gateways, routers, etc.) and other infrastructure.
- .005 IP Addresses. Adversaries may gather the victim’s IP addresses that can be used during targeting. Public IP addresses may be allocated to organizations by block, or a range of sequential addresses. Information about assigned IP addresses may include a variety of details, such as which IP addresses are in use. IP addresses may also enable an adversary to derive other details about a victim, such as organizational size, physical location(s), Internet service provider, and or where/how their publicly-facing infrastructure is hosted.
T1598. Phishing for Information. Adversaries may send phishing messages to elicit sensitive information that can be used during targeting. Phishing for information is an attempt to trick targets into divulging information, frequently credentials or other actionable information. Phishing for information is different from Phishing in that the objective is gathering data from the victim rather than executing malicious code.
- .003 Spearphishing Link. Adversaries may send spearphishing messages with a malicious link to elicit sensitive information that can be used during targeting. Spearphishing for information is an attempt to trick targets into divulging information, frequently credentials or other actionable information. Spearphishing for information frequently involves social engineering techniques, such as posing as a source with a reason to collect information (ex: Establish Accounts or Compromise Accounts) and/or sending multiple, seemingly urgent messages.
Here are many of the other techniques which utilize or impact DNS.
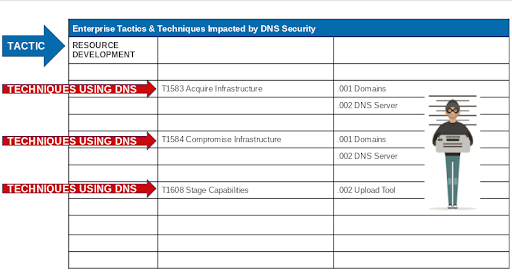
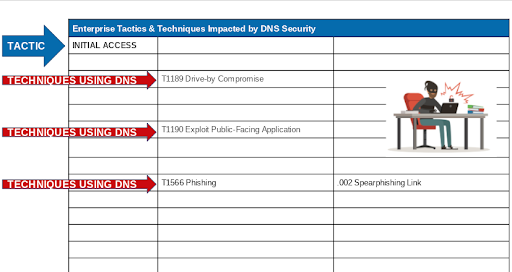
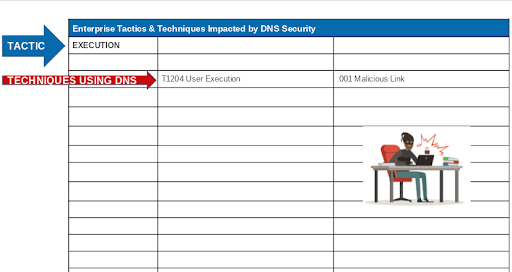
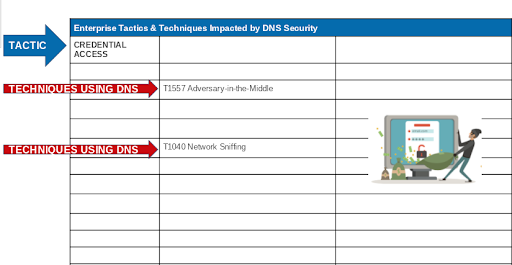
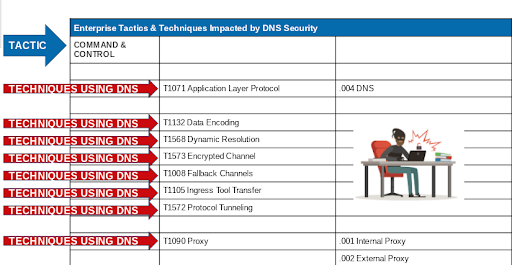
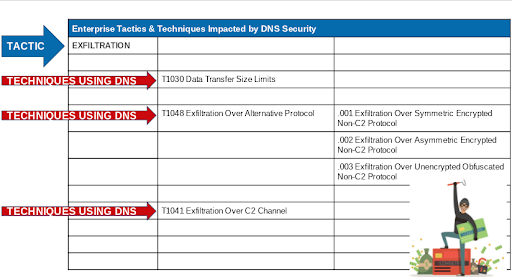
DNS is Used in the Great Majority of Cyber Attacks
DNS is ubiquitous and frequently used as an attacker technique for malware infiltration and data exfiltration. Sooner or later malware must reach back to command & control and DNS is used as a covert communication channel for this purpose. Attackers often use malicious domains and IP addresses that could already have a reputation and therefore be identified by threat intelligence. In many other cases the behavior of DNS queries, in context, can provide the essential clues that organizations need to identify and stop the attack.
Standard security controls and technologies such as next-gen firewalls, IPS, and gateways generally do not inspect DNS for detecting malicious communications. Often these security controls are unable to prevent specific attacks such as DNS data exfiltration. Most importantly, they are not able to detect the nuances associated with newly created malicious addresses and domains.
Infoblox BloxOne Threat Defense enables security operations teams to leverage DNS to get the highest visibility into malicious activity so that the cyberattackers can be detected and shut down early in the kill chain of events. BloxOne Threat Defense integrates with Security Orchestration Automation and Remediation (SOAR) systems, ITSM solutions, vulnerability scanners and other security ecosystem tools to trigger remediation actions automatically when any malicious activity is detected. This helps speed up an organization’s response to security events and provides rapid threat containment.
To learn more about our programs and products, and how to better protect your DNS infrastructure, please reach out to us via https://info.infoblox.com/contact-sales.html.
| Shields Up | CISA
Every organization in the United States is at risk from cyber threats that can disrupt essential services and potentially result in impacts to public safety. Over the past year, cyber incidents have impacted many companies, non-profits, and other organizations, large and small, across multiple sectors of the economy. www.cisa.gov |








