Powerful New Framework for Cyber Defenders
The MITRE Corporation has just released D3FEND, a complementary framework to its MITRE ATT&CK matrix. D3FEND will help cybersecurity professionals better defend and protect networks and information technology assets. MITRE received funding to create the D3FEND framework from the US National Security Agency (NSA).
The basic idea behind D3FEND is that the framework will provide defensive techniques that system administrators can apply to counter the activities of threat actors detailed within the MITRE ATT&CK matrix. The D3FEND technical knowledge base outlines defensive countermeasures which correspond to common offensive techniques. D3FEND enables cyber defenders to move with speed, precision, and accuracy to better counter and shut-down the activities of the most advanced threat actors.
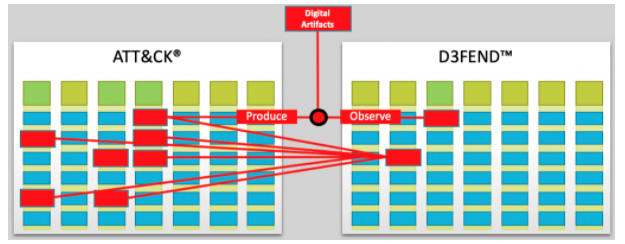
Image by MITRE Corporation
“D3FEND establishes terminology of computer network defensive techniques and illuminates previously-unspecified relationships between defensive and offensive methods,” the NSA said in a press release today. NSA believes that organizations that previously started using the ATT&CK framework will use the correspondent D3FEND techniques to counter those threats in the case of future intrusions.
D3FEND also potentially sets the stage for better automation of defensive measures. Automation is the key to expanded defensive capabilities especially as adversaries automate their offensive operations. Once the tactics, techniques and procedures of an adversary are recognized and identified, then the right defensive capabilities and counter-moves can rapidly be brought to focus on the attack. Over time, D3FEND can help provide a framework and improved strategy for organizing a rapid defense and linking to orchestration tools such as SOAR (security orchestration and response).
MITRE and the NSA have recommended that organizations start implementing the D3FEND framework. The MITRE Corporation has also released a comprehensive whitepaper (PDF) that describes the core principles and design behind its new framework.
Leveraging MITRE ATT&CK and MITRE D3FEND Requires Visibility
The NSA has spoken.
The National Security Agency and the Cybersecurity & Infrastructure Security Agency have gone on record in 2021 noting that every agency, organization and enterprise should leverage the existing DNS protocol and architecture by using a protective DNS service. Infoblox is referenced in the table of NSA recommendations here.
DNS security is an important and critical part of your defense. DNS is the translation that looks at where you want to go and translates that into an IP address. DNS gives you an opportunity to know and control what resources a user is accessing on the network. DNS is the first step in beginning to understand the user’s true intent.
In order to best leverage MITRE ATT&CK and MITRE D3FEND you must have visibility and comprehensive data about the activities occurring within your networks. BloxOne® Threat Defense, DNS security solution from Infoblox, along with DNS, DHCP, IPAM (DDI) provide deep visibility to this activity, including which network assets are accessing which destinations, where compromised devices are on the network and when new devices join the network . BloxOne Threat Defense helps protect enterprise users, devices, and systems. across your on-premises/HQ, cloud workloads, remote locations, and teleworking environment against phishing, exploits, ransomware and other modern malware, and prevents your teleworkers from accessing objectionable content restricted by policy.
DDI functions are core and critical network services. Nothing happens on the network if a device has no IP address and cannot query for domains. Tremendous visibility and insight can be gained by looking at DDI as it applies to security. Using DDI, you know who and what is on your network and the services are being accessed. DDI data is a critical part of your first first line of defense.
DHCP is the first step in the DDI chain. Before a device can access anything on a network, it needs to obtain an IP address using DHCP. On the surface, this protocol might be seen as the simple way a device requests an IP address and then gets it. Now the server now has a record (i.e., a lease) that ties that device via its MAC address to the granted IP. DHCP links an IP address to a device and unlocks all of the metadata associated with the DHCP process.
DNS is the second step in the DDI chain. DNS knows the service that is being accessed based on the domain for which the user traffic is destined. Envision this as a security stack where you have devices (and associated metadata), IP, and now data about the traffic destinations.
IPAM brings all of the data together so you can use it to improve your defense and make faster and better decisions. IPAM is the authoritative inventory for all devices on the network. IPAM is one place any host, subnet, server, or service VIP is defined, tracked, and kept up-to-date. This information is an invaluable and important part of any cyber defense strategy.
BloxOne Threat Defense Foundational Security is an essential control point and a critical part of your intelligence gathering and defensive measures. Find out more about how BloxOne Threat Defense can help you better leverage the powerful capabilities of MITRE ATT&CK and MITRE D3FEND.
To find out more please go to: https://www.infoblox.com/products/bloxone-threat-defense/








