By Suzanne Ronca, Phil Miller and Chris Usserman
On July 23, 2020, the Federal Bureau of Investigation, Cyber Division, sent out an alert number AC-000129-TT¹ to inform U.S. enterprises in the healthcare, chemical, and finance industries of potential targeting by the Chinese government against their business and operations based in China. The FBI noted that earlier this year, at least two Western companies operating in China detected malware directly attributed to tax software upgrades required for the Chinese value-added tax (VAT). This malware is embedded in the Chinese software and appears to launch a backdoor into the victim’s systems. This backdoor prepositions the future use of remote code execution, data exfiltration, and other dangerous and unauthorized activity on the victim’s network. Chinese government-based cyber operations have targeted U.S. healthcare, life sciences (pharmaceutical), and chemical sector companies for many years.
Per the FBI, the U.S. Department of Homeland Security, and Britain’s National Cyber Security Center, “ hackers continue to actively target organizations that include healthcare bodies, pharmaceutical companies, academia, medical research organizations, and local governments.”
Infoblox’s BloxOne Threat Defense (B1TD) is designed to protect enterprises from threats such as those identified by the FBI in the recent alert. Infoblox provided an internal investigation and review, and good news. We have those specific indicators already in our BloxOne Threat Defense product both natively (Infoblox-sourced), and partner feeds from SURBL (newly-observed domains), Crowdstrike, and FireEye.
In this specific instance, Infoblox and several of our premium partners already identified the FBI-reported IOCs in our threat feeds. Hence, existing customers exercising our DNS security solutions would be protected as they automatically receive threat feed updates at a customer-configured period, including real-time updates, and have access to informative context to help identify related threat intelligence, associated domains, and threat infrastructure.
Further, BloxOne Threat Defense provides customers with the ability to configure custom rule sets containing their derived threat indicators, as depicted in the screenshot below. BloxOne Threat Defense can be explicitly configured as it relates to enforcing the list of “IOC” (Indicator of Compromise) Domains, look-alike, other C2 concerns, and threats research around all DNS based client/server traffic which occur. Then, as soon as any system, anywhere in the world attempts to resolve the IP address associated with these domains, BloxOne Threat Defense will enforce the defined policy (e.g., block the action) and contain the threat.
Here’s a screenshot of B1TD’s policy engine that would enforce this specific scenario:
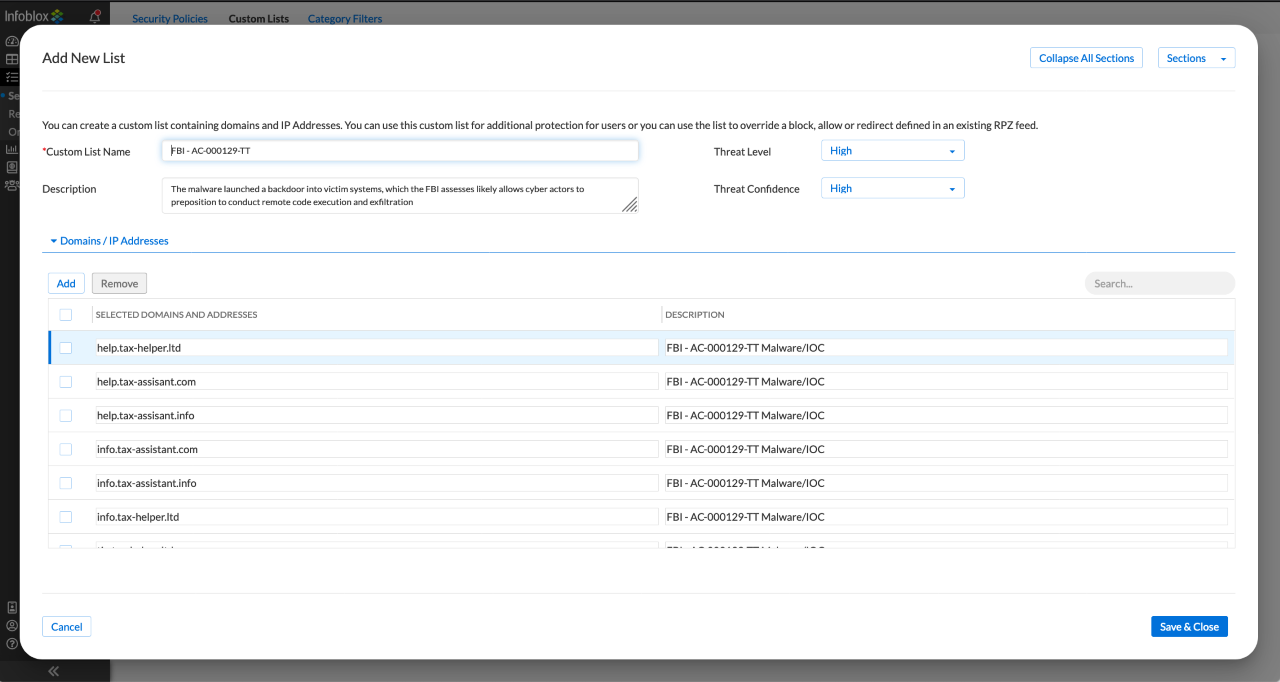
According to the National Security Agency (NSA), a substantial percentage of malicious command & control activity can be stopped in its tracks just by controlling your DNS. Infoblox’s integrations across the security ecosystem enable organizations to enact and automate playbooks in response to various threats triggered by only one event. For example, Infoblox can send an alert message to an endpoint solution associated with a customer’s organization, which attempted to communicate with a ‘bad’ domain on the internet. Or we can integrate many other tools, such as ServiceNow, NextGen Firewalls, or SOAR/SIEM platforms.
Also, exfiltration campaigns are increasingly seen abusing DNS platforms using various techniques; Infoblox provides Data Exfiltration protection for DNS (Cloud, On-Premise, or Hybrid). Infoblox security solutions are purpose-built to ensure uptime and protect the end customer/brand.
Here is an excellent ~5-minute video that summarizes how Infoblox DNS Security can help: https://www.youtube.com/watch?v=6GtjriAais0
Here is a data sheet on BloxOne Threat Defense Advanced: https://www.infoblox.com/wp-content/uploads/infoblox-datasheet-bloxone-threat-defense-advanced.pdf
If you want to know more, please reach out to us directly via https://info.infoblox.com/contact-form.
¹https://www.ic3.gov/media/news/2020/200728.pdf












