Any assumption that network traffic originating from inside a company’s network is trusted and outside is untrusted, does not hold water anymore. In fact, no traffic can be trusted even if it is originating from inside the corporate network. Some laptop/device on the inside could be infected by malware and start beaconing out to a command and control (C & C) server to exfiltrate company sensitive data.
Zero Trust is a strategic initiative that helps prevent data breaches by adopting a security posture of default deny. Trust is assessed at the time of network connectivity, with an identity and context-based logical access boundary, removing any notion of implicit trust based on your location or IP address.
While there is so much buzz about Zero Trust Network Architecture, it would be good to know what it is and is not, and how can modern foundational network infrastructure services from InfoBlox help achieving zero trust.
What Is Zero Trust Network Architecture?
Originally, Zero Trust Network Architecture (ZTNA) was proposed by John Kindervag, while he was the principal analyst at Forrester Research about 10 years ago, in response to the failure of traditional security models which operate with the outdated assumption that everything inside an organization should be trusted. This assumption is not true when any inside system/device has been compromised by a phishing attack, drive-by download of malware, or when it is being operated by a malicious insider/contractor.
In Zero Trust, you identify a protect surface that is made up of your most valuable data, assets, applications, and services. Then you define user/role-based policies for each protect surface using micro-segmented networks. Because they contain only what’s most critical to an organization’s application environment, protect surfaces are in orders of magnitude smaller than traditional attack surfaces and easier to manage.
At the very core, Zero Trust is both platform and technology agnostic. It enables you to build additional layers of security for your networks by using a wide variety of security technologies including foundational network infrastructure security, micro-segmentation, application-aware firewalls, secure web gateways, cloud access service brokers, and much more.
Five tenets of Zero Trust
- Validate Access to Data: Data is the central element that must be protected. Access to this data, at any time, must be continually and carefully revalidated.
- Analyze Data Flows: To best protect your data, you must understand the flows of your data in and out of systems/devices, both to be able to validate it later and to build out micro-segmented networks.
- Micro-segmentation: With an understanding of the critical data that must be protected, you can then create the micro-segmented networks that map best to the flow of the data.
- Visibility and monitoring: You must have visibility into all activity within your network, log it and be able to analyze it comprehensively by integrating with security information and event management (SIEM) technologies to determine if any malicious behavior is present.
- Automated Response: You should wrap Zero Trust best practices for security automation and orchestration and response (SOAR) tools to support your mitigation efforts.
Forrester recently expanded and clarified its original notion of Zero Trust to draw a road map for implementing a Zero Trust architecture: the Zero Trust eXtended (ZTX) ecosystem. In this report, Forrester identifies key vendors that support its view of the Zero Trust ecosystem and turns Zero Trust from the basic concepts of 10 years ago into a concrete framework and architecture for building out cybersecurity resilience across all of your networks.
DNS Security is the First Line of Defense for ZTNA
Domain Name Service(DNS) acts as the first line of defense for a protect surface (data, assets, applications, services) of ZTNA, by detecting and blocking activity related to most modern malware like ransomware, exploits, phishing, command and control (C&C) callbacks, data exfiltration, domain generation algorithms (DGA), APTs and more, using the latest threat intelligence and ML based analytics.
DNS Security augments your existing security tools and can offload blocking of threats from perimeter security, reducing the amount of malicious traffic sent to these tools and preserving their processing power. Here are the 3 ways DNS security can be leveraged.
- DNS Resolution: When a compromised endpoint attempts to resolve the domain name of a C&C server, the DNS server could block that name resolution and send that connection request to a sinkhole. This will prevent data exfiltration or new malware downloads from these C&C sites.
- DNS Tunneling: Hackers use DNS payloads as means to exfiltrate data on port 53, to circumvent next-generation firewalls, IDS/IPS rules. Enhancing DNS to detect such exfiltration attempts will prevent data exfiltration via DNS.
- Volumetric DNS Requests: Botnets could be used to launch a distributed denial of service (DDoS) attack on external DNS servers and make them unavailable to resolve name resolution of genuine domains. In 2016 the Mirai malware launched a massive DDoS attack on the DNS server operated by Dyn, by using millions of IoT devices as bots to generate fake DNS requests. A robust DNS service should be able to detect such fake DNS requests in large volume.
How Can InfoBlox DDI Platform and BloxOne™ Threat Defense Help?
Infoblox provides the industry-leading DDI platform (includes DNS, DHCP, and IPAM) that provides foundational security, centralized point of visibility and control needed to efficiently implement Zero Trust Network Architecture.
- Domain Name Service (DNS): DNS provides a critical audit trail of any domain/hostname lookups. This audit trail can be leveraged to quickly map out services and resources that have been accessed by compromised devices.
- Dynamic Host Configuration Protocol (DHCP): is used to dynamically assign reusable IP addresses to devices on the network, every time when a device (e.g. laptop) joins a network. DHCP data also helps correlate disparate suspicious activity associated with the same device under investigation especially in dynamic environments.
- IP Address Management (IPAM): begins with IP address discovery, tracking, and allocation of data pertaining to all devices on the network. It maintains a centralized repository of data associated with devices, networks, and services in one clear and easy to manage interface.
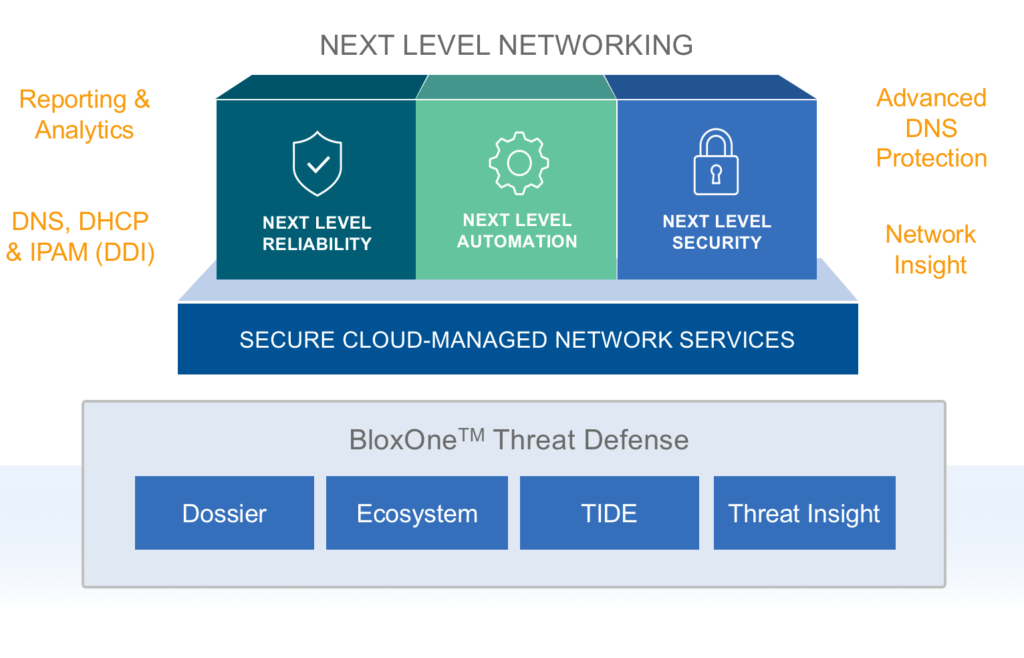
Figure 1: InfoBlox DDI Platform with BloxOne Threat Defense
The Infoblox DDI platform along with BloxOne Threat Defense (as depicted in Figure 1 above), provides foundational support for implementing key aspects of Zero Trust Network Architecture. The Infoblox platform enables you to detect and block data exfiltration and malware C&C communications via DNS. It maximizes brand protection by securing traditional networks, as well as digital imperatives like SD-WAN, IoT, the cloud, and mobility. It integrates with other security technologies such as network access controller, NG firewalls, vulnerability scanners to provide security orchestration and automated response (SOAR) solutions, to quickly contain and remediate cyberthreats, and optimize the performance of the entire security ecosystem and reduce the total cost of enterprise threat defense.
Learn More about ZTNA with this Whitepaper from Infoblox: An Introduction to Zero trust – A Compelling Cybersecurity Strategy for Defending the Enterprise.




















