Authors: Zafir Ansari and Darin Johnson
Often referred to as the “phonebook of the internet,” DNS translates domain names into IP addresses, allowing us to navigate the web. Its fundamental role in internet communication means DNS traffic routinely passes through corporate firewalls with minimal inspection.
DNS tunneling involves encoding data within DNS queries and responses, creating a covert communication channel between a client and server. Cybercriminals leverage this method for purposes like command-and-control (C2) operations and data exfiltration, making it a concern for businesses and cybersecurity professionals alike. Understanding and mitigating DNS tunneling is no longer optional—it is a necessity for safeguarding today’s enterprises from evolving cyberthreats.1
In this blog, we will explore the fundamentals of DNS queries, illustrating how they typically function and how this essential process can be exploited for C2 operations and data exfiltration. We will also dive into the various families of DNS tunneling, shedding light on the techniques attackers use to bypass traditional defenses.
To create a DNS C2 infrastructure, an actor must control a domain name’s authoritative name server. Then, the malware on a victim system can perform periodic lookups of the domain, which, based on the responses, can cause the malware to perform different actions, such as perform a directory listing. The information from that directory listing can then be encoded as subdomain queries. Responses to those queries could be a simple acknowledgement of receipt or commands to perform additional actions. Because the malware uses the DNS system, there is no direct traffic between the malware client and the C2 server. Instead, the communication is sent through the victim system’s recursive name server. Recursive name servers require the ability to communicate with authoritative name servers on the internet, so it will generally have permissive rules. Figure 1 shows the recursive DNS process, Figure 2 shows the packet capture of a DNS tunnel, and Table 1 shows a theoretical example of a DNS tunneling session.
Several tools can perform DNS tunneling. Some of the most common are Cobalt Strike, DNSCat, Iodine, Pupy, and DNS Exfiltrator.
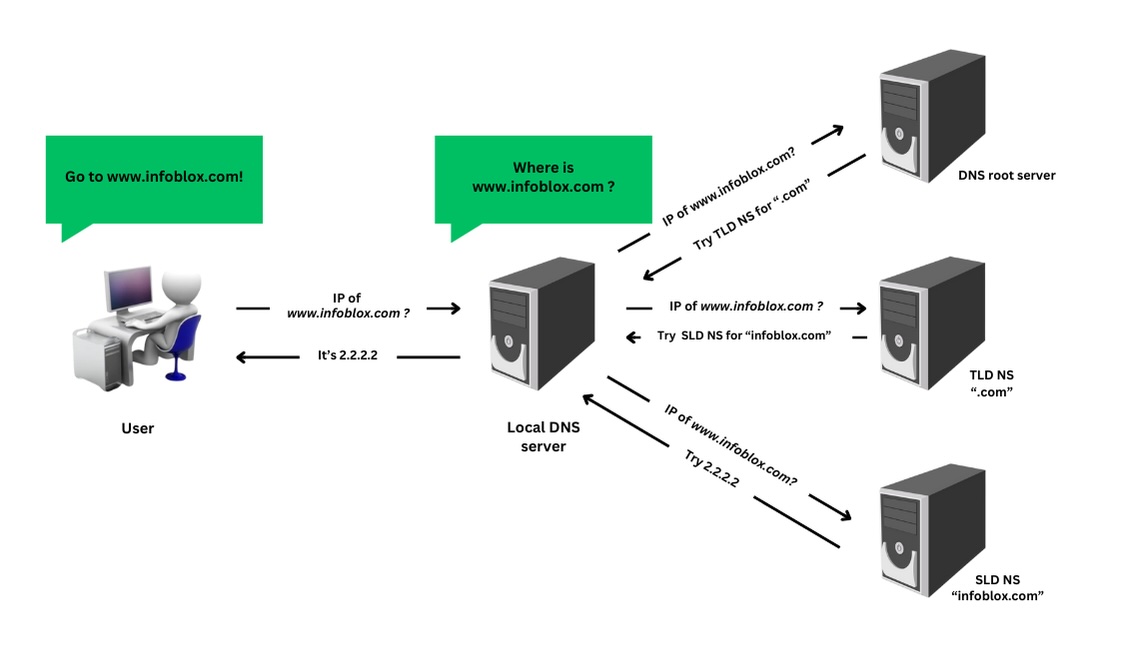
Figure 1. The typical process of how DNS operates
As shown in Figure 1, when a client requests the IP address for a domain, the request is sent to a DNS recursive resolver. This resolver initiates a series of queries, starting with the top-level domain (TLD) server, which provides the address for the second-level domain (SLD). The process continues recursively until the resolver reaches the authoritative nameserver for the fully qualified domain name (FQDN). The authoritative resolver responds with the requested information, which could be an A record (IPv4 address), AAAA records (IPv6 address), TXT record (free form text), CNAME record (canonical domain name), or another type of record. The recursive resolver then returns this response to the client while caching both the query and the response for the specified time to live (TTL), ensuring faster responses for future requests.
| Type | DNS String | Decoded Content |
|---|---|---|
| Request |
757365726e616d653a20616e64792 c2.070617373776f72643a20313233 78797a6162632e.example.com |
username: andy, password: 123xyzabc. |
| Response |
ON2WI3ZAOJWSAL3FORRS643I MFSG65YK |
Sudo rm /etc/shadow (delete password file) |
| Table 1. An example encoded DNS tunnel query/response using TXT records | ||
A subdomain such as 757365726e616d653a20616e64792c2.070617373776f72643a2031323378797a6162632e.example[.]com could be decoded to reveal sensitive information such as “username: andy, password: 123xyzabc.” The server’s response might include a TXT record like “ON2WI3ZAOJWSAL3FORRS643IMFSG65YK,” which when decoded, could instruct the client to perform an action, such as sudo rm /etc/shadow. Similarly, attackers can encode and exfiltrate larger data, such as files, in smaller chunks using DNS, and upload malware through responses.
It is important to note that C2 communication does not have to rely solely on TXT responses. Any DNS record type can be used as long as there is a consistent encoding. Common record types seen for DNS tunnels are A, AAAA, TXT, CNAME, and MX. See.List of DNS record types (Wikipedia) for a complete list of DNS record types
Infoblox’s Threat Insight machine learning algorithms2 detect and block tunneling domains within the first few minutes of a tunnel becoming active. Generally, this happens before the handshake is completed and definitely prior to malicious C2 or exfiltration. While Threat Insight provides real-time detection on DNS tunnels in our customer networks, Infoblox Threat Intel has additional batch algorithms to detect DNS tunnels. Here we focus on our Threat Insight detector.
Actors may choose to develop their own tunneling software or use common open-source tools. We group these open-source tools into DNS tunneling families. Over the past two years, we surveyed which families were most prevalent in our customer traffic. Table 2 provides an overview of some of these families, many of which have been leveraged in real-world attacks.
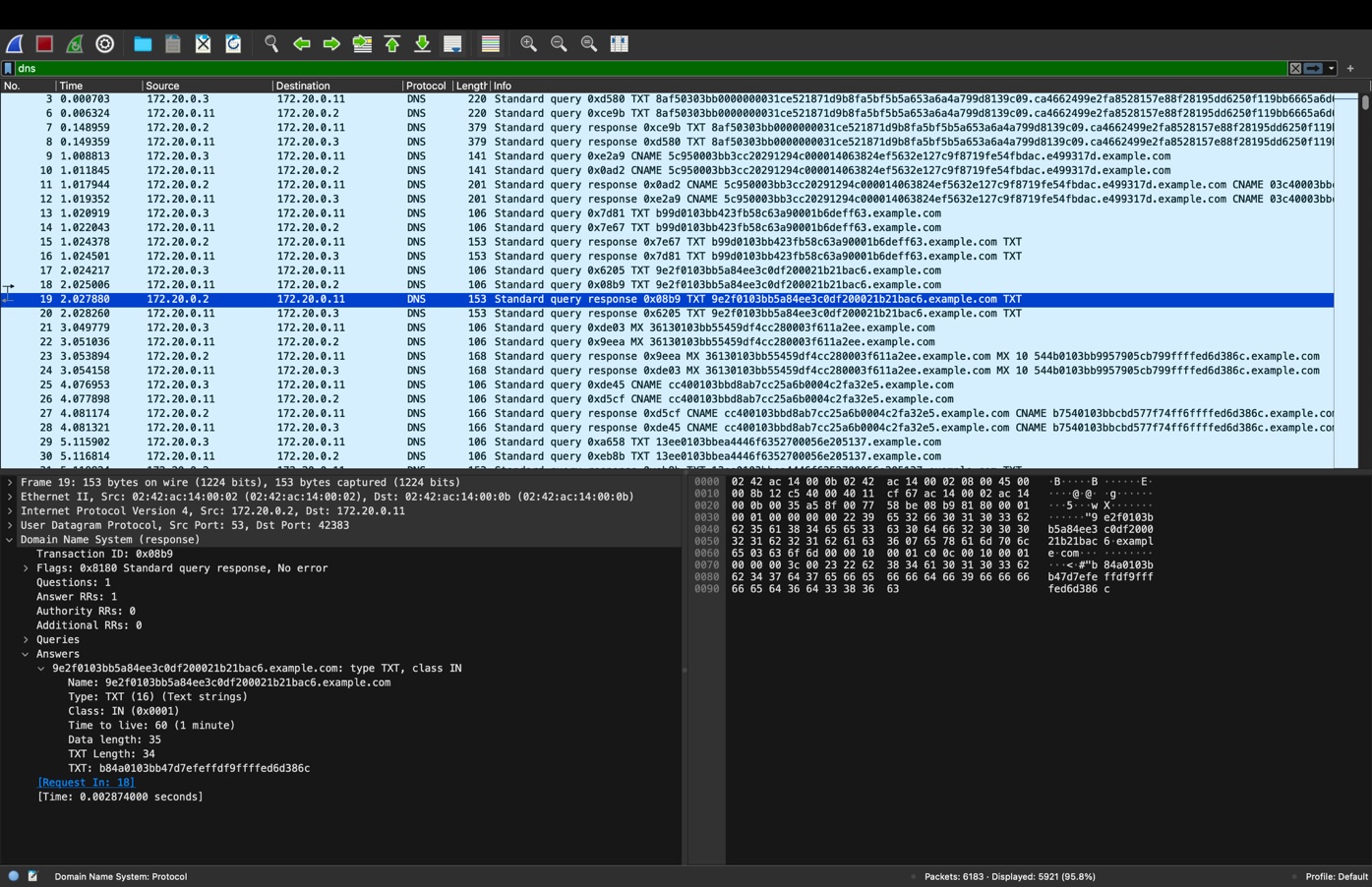
Figure 2: Packet capture displayed in Wireshark file exfiltration
| Family | Example Queries | Unique Domains (%) |
|---|---|---|
| Cobalt Strike | post.a34.cde343de.a1b2c3d4.domain[.]com | 26% |
| DNSCat2 | 67b1017285c8d258ff8d02000cf8da0d6e.domain [.]com |
13% |
| DNS Exfiltrator | 1.yqa5rey3ncqdozqvves3fvdutle7kkcnxntxzxg 26s7yrfsdwncleip6irihksb.pbkyozoc5q2ne6ey 5cgedjmteocypbv7hrpk2ge3mzauakbhg5kvjbsvv asov33.o25jv4gfntbulxvidykra6gua6q5kte2sf qiq7tf7jbdpexbaonxwx6lpak7eye.wmrp655fmvm onexlccsxclbd7ynu7htzqjpjf.domain[.]com |
15% |
| Sliver | Lpgekzzgoeqhrhaugtulrdbtbpgdzqpzmv8ieq26h b6tq8rdscexk2atbhbizpx.ngpc4isa77znjl3afc ljkswcru2tjrue8uippsywo5wciwx3iepklapemze bknv.bl37n83glutyxfgjxlvplcnyn.domain[.]c om |
12% |
| Weasel | feiq- zb3xgodutf25v7vtcsk5dxh7awwww.9c.21f9.dom ain[.]com |
2% |
| Pupy* | Y12rmhy9.chu5zj1hwsylrrq46fxf442yf62a9999 .bla3rzp4nnwrfmnn2a3m3xa9[.]domain.com |
7% * |
| Iodine | 1i5a5xl2ojglpzzggwqlqmfea4100yk2zi3nal14s y3uvbadxu2uugmnbrmmat.gprzfx451baplinw3rx 11og003leilo3pq5mz1uojs34xxc3swo2d1cwh.uj xb4cpux1w21qzbdkwmvswr5n2fxjb2kvwfqtdnfni dqnkrgjfhzcero.g45tgfvbfmzgu55cckomjgepef yqtk2acpkekqdgzj00q5dk4nzt4o0[.]domain.co m |
24% |
|
Table 2. Common families of DNS tunneling seen within customer traffic with typical query patterns and their detection rates across open-source security tools |
||
*Pupy was seen in our customer traffic, but indirectly through internet scanners. See our work on Decoy Dog.
Cobalt Strike is a popular pen test tool which has a DNS C2 module. It is commonly used by red teams and threat actors.3 It uses hex encoded queries with optional and customizable words prepended, such as “post,” “api,” or “dx.” It performs beaconing using A records and C2, and exfiltration using TXT records.
DNSCat2 is a lightweight tool designed for creating encrypted DNS tunnels, commonly used by penetration testers and occasionally abused by attackers for stealthy data exfiltration. It is included within METASPLOIT, an open-source pen test tool. DNSCat2 can operate using a variety of query types, including A, TXT, CNAME, and MX records.
DNS Exfiltrator is a proof-of-concept tool that encodes data into DNS queries for exfiltration, demonstrating the risks of DNS misuse in real-world scenarios. It uses TXT records, provides only one-directional communication, and is started via the command line. While we have seen this used to test our DNS tunneling detection, we have not seen it used by a threat actor and deem it impractical given the one-directional mechanism.
Sliver is a cross-platform C2 framework with DNS tunneling capabilities, frequently utilized in adversary simulations and malicious campaigns.
Weasel is a less-documented DNS tunneling tool developed by Facebook’s Red Team that supports stealthy data exfiltration and C2, typically used in niche red teaming engagements. It uses A and AAAA records for communications.
Pupy is an open-source, multi-platform RAT with DNS tunneling support, historically leveraged in espionage campaigns against government and corporate entities. It uses A records for communications.
Iodine is a well-known tool for tunneling IPv4 traffic over DNS, used in penetration tests and sometimes abused in attacks, such as by nation-state actors for C2 purposes. Iodine uses A, TXT, CNAME, and MX records to communicate.
One useful observation we made during this study was that all these families had highly unique signatures with the queries and responses they used. We incorporated these signatures at our Threat Defense Recursive DNS Resolver, which allowed us to improve our Threat Insight’s machine learning algorithms from one to two minutes to detect to less than five seconds. This reduces the number of potential queries to less than 10, which eliminates even small amounts of exfiltration.
In addition to the families described above, we found several other tunnels, including automated and custom pen test tools, anti-virus, anti-spam, as well as DNS tunneling demonstration tools from security vendors.
Antivirus and antispam tools use DNS as a mechanism to determine if a domain or file hash may be malicious. A query may be of the form: “<domain>.<guid>.<avdomain>” or “<file hash>.<guid>.<avdomain>” with response being NXDOMAIN if the domain or file hash is not in a known malware or spam list, or “127.0.0.X” if it is in such a list. One might consider this to be an actual DNS tunnel. In Detecting DNS Tunneling Using Behavioral and Content Metadata Features, we showed that one could train on such domains and recover tunnels such as Cobalt Strike and DNSCat2. Infoblox maintains lists of antivirus and antispam tools to avoid blocking generally useful tools. We also use them to ensure our machine learning-based tunneling algorithms are sufficiently robust to be able to detect tunnels other than those in our training set.
Several automated pen testing tools, such as Cymulate and AttackIQ, have appeared. We see these tools’ domains detected on our customer networks regularly. We specifically do not use them for training, add them to block lists or signature them. We rely solely on our machine learning algorithms to detect those domains.
Many customers chose to write their own tools for DNS tunneling to test our software. Most resemble DNS Exfiltrator in that they are one-directional exfiltration channels. Some have taken to using unsuccessful responses, such as NXDomain and SERVFAIL. This requires a careful balancing act as one could also perform tunnel-like queries to legitimate domains and thereby cause the resolver to block all queries to a legitimate domain. To solve this problem, we ensure positive control of the name servers of the domain and otherwise downgrade the detection from DNS tunneling to DNS tunnelling notional, which we recommend such events be logged verse blocked.
We have seen a few customers attempt to create bidirectional DNS tunneling tests; one interesting find included a detection event for a domain using the queries and responses in Table 3.
| Query Type | Query Prefix | Query Answer |
|---|---|---|
| 16 | cgluzzey.t1.<redacted> | “hello” |
| 16 | cgluzzey.t1.<redacted> | “whoami” |
| 16 | cgluzzey.t1.<redacted> | “ls -lsa” |
| 16 | cgluzzey.t1.<redacted> | “cat /etc/shadow” |
| 1 | etrvrq.ciwsldovcnvul3n5c3rlbwq6l3vzci9zymlul25v.t1.<redacted> | 12.12.12.3 |
| 1 | jxfszd.mgpetlnfegzpbhryyxrvcgpkbnnwb3quymlucmru.t1.<redacted> | 12.12.12.3 |
| 16 | cgluzzey.t1.<redacted> | “aGVsbG8” |
| Table 3. Example queries from a custom DNS tunnel | ||
We performed queries for domains with responses “whoami,” and discovered two additional domains, which were also detected as tunnels earlier. In total, the unique answers included: “hostname”, “ls”, “aWQ”, “pwd”, “ls -lsa”, “oa”, “whoami”, “test”, “hello”, “cat /etc/passwd”, “uname -a”, “whoamid”, “d”, “ia”, “cHdk”, “ls -lsa /”, “whoama”, “aGVsbG8”, “whoamd”, “bHM”, “cat test.txt”, “cat /etc/shadow”, “oda”, “ls”, “exit”, “ao”, “ls /”, “cat test.py”, “id”, “wasdasd”. Later, we saw the domains with the CNAME requests and Base64 encoding.
Finally, we sometimes see our customers use our competitors’ DNS tunneling tools. On September 17, 2024, we observed a domain paioaltonetworks[.]tech in our DNS exfiltration detection system, Threat Insight. At first, we thought this might be a false positive or the result of a mistyped URL in an application. However, on inspection the queries looked like:
Mf9q7qgqmy003024muqg4zlxebwgk5tfnrzsa33g.paioaltonetworks[.]tech
Mf9q7qgqmy006024or3w64tlebugk4tpmvzs4icp.paioaltonetworks[.]tech
Mf9q7qgqmy001024ivwxa33xmvzca6lpovzcasku.paioaltonetworks[.]tech
In addition, we noticed its name servers were ns1.paioaltonetworks[.]tech and ns2.paioaltonetworks[.]tech, and it was registered in January 2024 with OVH.
Within one minute of the initial queries, the domain was blocked. We then looked at the domain in Domain Tools. Here we noted that domain has a low-risk score of 23 out of 100. This is not particularly odd for domains used in DNS exfiltration, unless there is previously published work on the domain in question.
Domain Tools allows us to dig deeper into investigating the domain in question using a powerful tool: the registration pivot engine. Using the pivot engine, we observed the registrant organization is Efficient IP and there are nine other domains associated with the registrant, including rockitwith[.]me, paioaltonetworks[.]tech, nicecricket[.]online, framatech[.]online, melenchon[.]online, redfusion[.]xyz, efficientip[.]io, dga[.]how, efficientip[.]net, efficientip[.]org, infobiox[.]com, efficientip[.]it, efficientip[.]at, efficientip[.]com, and dns-blast[.]com. All domains were registered with Ghandi or OVH.
The website https://www.efficientip.com advertises Efficient IP, which offers DNS, DHCP, and IP management solutions similar to Infoblox.
We observed that the domains rockitwith[.]me, paioaltonetworks[.]tech, and nicecricket[.]online were all detected as DNS exfiltration by our streaming detection algorithms in Threat Insight and as suspicious/potential exfiltration by our batch Threat Intel algorithms.
The domains melenchon[.]online, dga[.]how, framatech[.]online, redfusion[.]xyz, and dns-blast[.]com were not seen in Infoblox DNS traffic. Many of these domains have nameservers of the form “ns1.exf.<domain>.” This domain structure resembles that of hack53[.]shop, which was detected as DNS exfiltration in 2022.
Combining DNS exfiltration and lookalike domains is a common tactic used by both malicious actors, such as Side Winder and pen testers, and we have noticed an uptick in the combination in 2024. Infoblox leads the industry in state-of-the-art techniques to detect both these behaviors and more with Infoblox Threat Defense™.
Due to the lookalike nature of paioaltonetworks[.]tech and infobiox[.]com we did add these to our suspicious feeds. We continue to rely on our machine learning-based detections for the other Efficient IP domains.
Footnotes:
- What Is DNS Tunneling?, Infoblox.
- Detecting DNS Tunneling Using Behavioral and Content Metadata Features, Johnson, Darin, Software Engineering Institute, Carnegie Mellon University, February 6, 2023.
- DNS Early Detection – Cobalt Strike DNS C2, Zuckerman, Michael, Infoblox, March 22, 2024.










