Recently, there has been an observed increase in malicious cyber activity targeting managed service providers (MSPs) and their customers. This is a trend which is expected to grow and continue.
The cybersecurity authorities of the United Kingdom (NCSC-UK), Australia (ACSC), Canada (CCCS), New Zealand (NCSC-NZ), and the United States (CISA), (NSA), (FBI) issued a joint Cybersecurity Advisory (CSA) AA22-131A overviewing the threats to MSPs the potential impacts to their customers. This CSA provides actions MSPs and their customers can take to reduce their risk of falling victim to a cyber intrusion. This advisory describes cybersecurity best practices for securing sensitive data within information and communications technology (ICT) services for MSPs and their customers. The advisory recommends that organizations should implement these guidelines as appropriate, and in compliance with applicable regulations. MSP customers should verify that the contractual arrangements with their services provider for cybersecurity include the measure to address these risks.
MSPs deliver, operate, or manage ICT services and functions for their customers via a contractual arrangement, such as a service level agreement. In addition to offering their own services, an MSP may offer services in conjunction with those of other providers. Services offerings may include platform, software, and IT infrastructure services; business process and support functions; and cybersecurity services.
MSPs generally provide services that usually require both trusted network connectivity and privileged access to and from customer systems. Many organizations use MSPs to manage ICT systems, store data, or support sensitive processes. Many organizations make use of MSPs to scale and support network environments and processes without expanding their internal staff or having to develop the capabilities internally.
Threat Actors Targeting MSP Access to Customer Networks
Whether the customer’s network environment is on premises or externally hosted, threat actors can use a vulnerable MSP as an initial access vector to multiple victim networks, with globally cascading effects. The UK, Australian, Canadian, New Zealand, and U.S. cybersecurity authorities expect malicious cyber actors, including state-sponsored advanced persistent threat (APT) groups, to step up their targeting of MSPs in their efforts to exploit provider-customer network trust relationships. For example, threat actors successfully compromising an MSP could enable follow-on activity, such as ransomware and cyber espionage, against the MSP as well as across the MSP’s customer base.
The UK, Australian, Canadian, New Zealand, and U.S. cybersecurity authorities have previously issued general guidance for MSPs and their customers. This new advisory provides additional specific guidance to enable better communications between MSPs and their customers that center on securing sensitive information and data. This alert strongly suggests a re-evaluation of security processes and contractual commitments.
Download the full government advisory Protecting Against Cyber Threats to Managed Service Providers and their Customers.
Many Types of DNS-based Attacks can Threaten MSPs and their Customers
A DNS Attack is any attack targeting the availability or stability of a network’s DNS service. Attacks that leverage DNS as its mechanism as part of its overall attack strategy, such as cache poisoning, are also considered DNS attacks. At the 1,000-foot view, there are attacks on DNS services which attack the DNS infrastructure itself, either rendering the DNS service itself unavailable or subverting the answers provided by the DNS servers. Like any other server, DNS servers are prone to all network-based attacks. There are many ways attackers can cause a large amount of network traffic to the DNS servers, such as TCP/UDP/ICMP floods, rendering the service unavailable to other network users by saturating the network link to the DNS servers. Attackers can also leverage a specific vulnerability in the DNS server software or host operating system, to either bypass control measures to create rogue entries in the DNS database, or cause the DNS server to crash.
Most types of malware rely on using DNS as part of their overall function to not only communicate with the command-and-control server, but to update and evolve itself. A prime example is the recent WannaCry ransomware, which relies on making an initial successful DNS query before it executes its attack.
DNS Tunneling is another attacker general technique (MITRE ATT&CK Technique
ID: T1071.004) that encodes messages in DNS queries and answers, mostly to evade detection. While there are legitimate uses of DNS Tunneling, where it gets serious is when someone uses it to exfiltrate data. This can be very difficult to detect, due to the ever-changing domain names, and the encoding-decoding schema chosen.
Here you can see an example of a DNS Tunnel – B1txor20 Linux Botnet. This was first observed propagating through Log4j in February 2022. This uses DNS tunneling to register with and execute commands sent by C2 servers. Sensitive information hidden using specific encrypting/encoding techniques (Zlib compress, RC4 Encrypt, Base64) and sent to C2 server as a DNS request. C2 sends payload/further instructions as a DNS response. 14 to 15 different C2 instructions were supported.
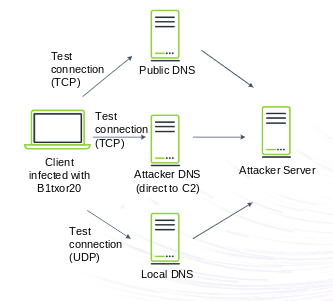
You can learn more here courtesy of the NSA.
Infoblox Secures Your Modern Enterprise
Infoblox BloxOne Threat Defense helps protect an organization against today’s sophisticated and ever evolving threats. BloxOne Threat Defense can reduce incident response time by automatically blocking malicious activity and provide the threat data to the rest of your SOAR and security ecosystem for fast investigation, quarantine and remediation. This can reduce the noise generated by your firewall and the overall number of alerts requiring review. To find out more about how BloxOne Threat Defense can help secure your network and data, please reach out to us via https://info.infoblox.com/contact-form/.
Don’t be the last to know! The June 2021 Gartner report recommends organizations leverage DNS logs for threat detection and forensic purposes with their Security Information and Event Management platforms.

Russia’s invasion of Ukraine could impact organizations both within and beyond the region, to include malicious cyber activity against the U.S. homeland, including as a response to the unprecedented economic costs imposed on Russia by the U.S. and our allies and partners. Evolving intelligence indicates that the Russian Government is exploring options for potential cyberattacks. Every organization—large and small—must be prepared to respond to disruptive cyber incidents. As the nation’s cyber defense agency, CISA stands ready to help organizations prepare for, respond to, and mitigate the impact of cyberattacks. When cyber incidents are reported quickly, we can use this information to render assistance and as a warning to prevent other organizations and entities from falling victim to a similar attack.
Organizations should report anomalous cyber activity and/or cyber incidents 24/7 to report@cisa.gov or (888) 282-0870.









