Ransomware has struck once again at another healthcare institution. Threat actors have targeted and disabled an Italian vaccine registration system in Lazio, one of Italy’s largest regions. Lazio is a central Italian region bordering the sea which includes Rome, Italy’s capital. The Italian government’s post in Facebook noted that a “powerful” attack had disabled Lazio’s databases and systems, including the system that manages the COVID-19 vaccination scheduling and appointments1.
According to Nicola Zingaretti, president of the Lazio Region, the attack took place starting Saturday night and continued into Sunday morning “blocking almost all of the files in the data center.” Zingaretti noted that the “situation is serious and we immediately alerted the police and the highest levels of the state, which we thank.” The cyberattack hasn’t so far interfered with any existing vaccination appointments, but it caused the temporary suspension of new appointments.
The regional health councilor of Lazio, Alessio D’Amato assured more than 500,000 citizens that had already scheduled their vaccinations through August 13th that they would still be able to receive the vaccination. D’Amato further described the recent incident “as the most serious cyberattack ever carried out on an Italian public administration.2”
Verification of the exact source of the attack, and the ransomware used, is still unfolding. There is unverified data3 that the attack may have been promulgated by the use of RansomExx4. In a ransom note that appears to be used in the Lazio attack, the ONION URL listed appears to be a known TOR site for the RansomEXX operation. RansomEXX “negotiation pages” are unique for each victim. They may also include exfiltrated data including screenshots of files and more. The Italian security threat researcher JAMESWT has pointed out that the ransomware attack may be attributable to LockBit 2.05.
2021 has turned out to be one of the worst years for ransomware and perhaps for healthcare. Threat actors are shameless in their pursuit of extorted dollars and know that healthcare systems are essential for the public welfare. Even back in 2020, CISA published and HHS published joint advisory on ransomware, most notably Ryuk ransomware, targeting the healthcare sector.
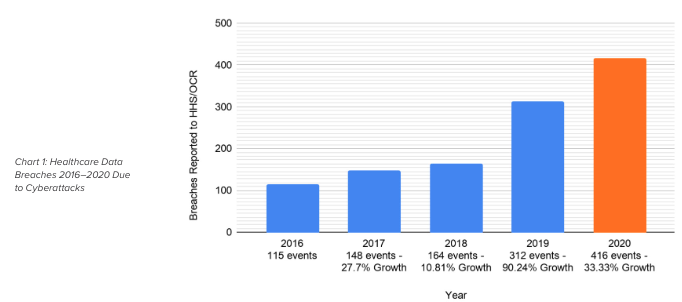
According to the Infoblox 2021 Healthcare Cybertrend Research Report6, there were over 416 major healthcare data breaches reported in 2020 in the United States which was a substantial increase over the 312 major healthcare data breaches reported in 2019. 62 percent of the largest of these healthcare cyberattacks in 2020 were directly attributable to ransomware per the Infoblox analysis. Ransomware remains by far the most predominant weapon of choice used by threat actors in their war on healthcare.
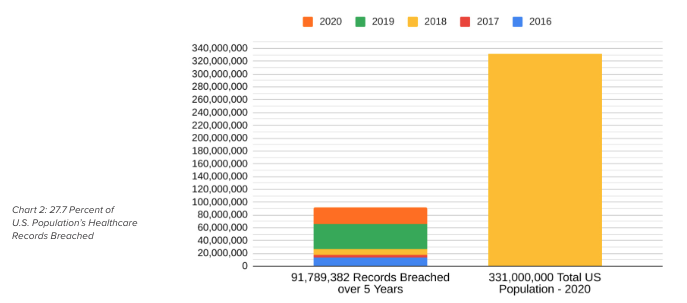
Chart 1 below, excerpted from the report, illustrates the research statistics on major healthcare data breaches from 2016 – 2020 due to cyberattacks. This data reflects a total of approximately 91.8 million data records breached versus the total estimated U.S. population of 331 million. Assuming no overlap of patient data records breached, then the total percentage of patient data records breached would be 27.7 percent of the U.S. population. That is, almost 3 in 10 U.S. citizens had their personal data breached in the past five years by cyberattacks. In context, a simple analysis of healthcare data records breached in 2020 would yield the conclusion that approximately 8 percent of the U.S. population was compromised that year.
Chart 2 below, also excerpted from the report, further illustrates that 27.7 percent of the entire U.S. population’s healthcare records were breached, in great part due to ransomware over the past 5 years.
DNS plays a critical role in execution of ransomware campaigns, and is the mechanism by which compromised devices make C&C calls to download additional malicious commands and execute them. Using threat intelligence and AI/ML based analytics deployed on DNS platforms, organizations can disrupt the use of DNS as a malware channel, stop DNS based data exfiltration, notify the broader security ecosystem of any suspicious activity and improve the security posture of the entire organization.
The Infoblox CIU continues to observe the Lazio attack details as they unfold. The CIU has published this Cyber Threat Advisory (CTA) which will be updated as further details are released. In addition, the Infoblox CIU will update the Threat Intelligence Data Exchange (TIDE) with indicators of attack (IOCs) once they become available and can be confirmed7.
2. https://edition.cnn.com/2021/08/02/business/italy-hackers-covid-vaccine-intl/index.html
5. https://twitter.com/JAMESWT_MHT/status/1422652277467328517?s=19





