The frequency of ransomware attacks is staggering, with 317.59 million ransomware attempts recorded in 2023 alone. While all types of organizations are targeted by ransomware, the likelihood of getting hit by ransomware generally increases for larger organizations with higher revenue. From an industry perspective, healthcare was one of the top sectors that reported an increase in attacks over the last year according to Sophos, with attack rate in that sector going from 60% to 67% over the last year.
Business Impact is Costly
Recovery from ransomware attacks is costly and it goes well beyond the ransom payment. 59% of organizations were hit with ransomware last year and 56% of those attacked paid the ransom to get their data back. Even if companies have backup and can recover their data without having to pay ransom, they still run the risk of their data getting stolen and being leaked in the dark web if they don’t meet the ransomware actor’s demands. In a third of the ransomware incidents recorded last year, data was also stolen. It cost companies $2.73 M on average to recover from these attacks, not including the ransom payment.
Now let’s come to the disruption to business that is a common occurrence after a ransomware attack. There are several public examples of critical city services getting impacted such as operations of public courts, emergency services such as police and fire dispatch, or hotel reservations not going through after a ransomware attack. Organizations will try to optimize for minimal financial impact and disruption and many times it comes down to what costs more – paying the ransom or trying to recover the data and systems themselves. On average, it takes 22 days to recover from a ransomware attack which is too long for a business to be offline.
Why are Successful Ransomware Attacks Increasing?
Ransomware is constantly evolving, with more and more ransomware families discovered every year and new variants detected daily. More recently, AI is being leveraged to create more variants to avoid detection from security tools, as well as to increase effectiveness of phishing and reconnaissance used by ransomware actors. AI coding tools also make it easier to create 30 to 40% more variants, making ransomware too easy and profitable for threat actors. Most security tools try to detect and respond to malware based on its behavior AFTER a breach has occurred and malicious activity is underway. This approach is way too slow and error prone. SOCs (security operations centers) are already overwhelmed with too many alerts and IoCs (Indicators of compromise) to monitor, investigate, and remediate. The average enterprise gets 4000 plus alerts per day. In contrast, the average attack breakout time is a mere 62 minutes. This means organizations must detect, investigate, and remediate every new ransomware variant they see flawlessly within these 62 minutes or a broader scale incident is likely. Given the rise of AI as mentioned above, enterprises should expect a dramatic rise in novel ransomware variants specifically designed to evade detection or, in some instances, disable existing malware detection tools. Therefore, organizations must evolve their threat detection and response strategies to go beyond traditional malware-focused approaches or risk becoming yet another ransomware statistic.
Identifying and Blocking Ransomware Domains with DNS Threat Intelligence
Using DNS threat intelligence, Infoblox can proactively stop most new ransomware variants before they can infect and propagate in the environment. We do this by going after the attackers’ supply chains. While attackers constantly morph and change the malware to evade detection, the infrastructure the threat actors use to activate the malware and provide instructions is harder to obfuscate and is often a dead giveaway. Thus we focus on their supply chains by globally tracking the DNS infrastructure that ransomware actors and their affiliates own. An easy to relate to example of this is link shorteners. We have all got the text with a shortened link that is hard to decipher. If it is legitimate communications like your bank messaging you, chances are they use Bitly to produce the link. If it is a cybercriminal it turns out they often will use a link shortener service just for attackers that we nicknamed Prolific Puma. Thus we don’t have to know anything else about the domain/website or worry about convicting a specific file as malicious, if we see the link you are trying to click is shortened using Prolific Puma instead of Bitly we will proactively block the DNS connection preventing an infection from ever happening.
We use this type of approach to proactively block new malicious domains before they are ever used, stopping ransomware threats before they get started. High risk domains that behave in a way that suggests malicious intent or share characteristics with other known malicious domains can be quickly identified and the first DNS query to these domains can be blocked, protecting organizations at the earliest point in the attack. Infoblox analyzes domain related data using sophisticated algorithms that use machine learning to identify suspicious domains and monitor for infrastructure changes to help proactively protect customers from emerging ransomware attacks. Using this approach, 60% of new domains can be blocked even before a ransomware actor can use them once. In addition, data theft via DNS can be stopped, accelerating the time to response and containment for those incidents that do get through.
Almost all malware uses DNS (92%) to initiate and carry out their attacks and ransomware is no exception. We begin blocking domains that will eventually be used by ransomware actors on average 63 days before they are used in a malicious campaign, giving you a massive head start vs. your adversaries.
As an example, Infoblox identified key C2 (Command and Control) domains associated with Blackcat ransomware (a group that has compromised thousands of businesses and organizations worldwide and extorted over $300 million in funds) as suspicious, days to months ahead of the industry.
Disrupting Ransomware Lifecycle at the Earliest Opportunity
The following diagram shows the typical malware lifecycle.
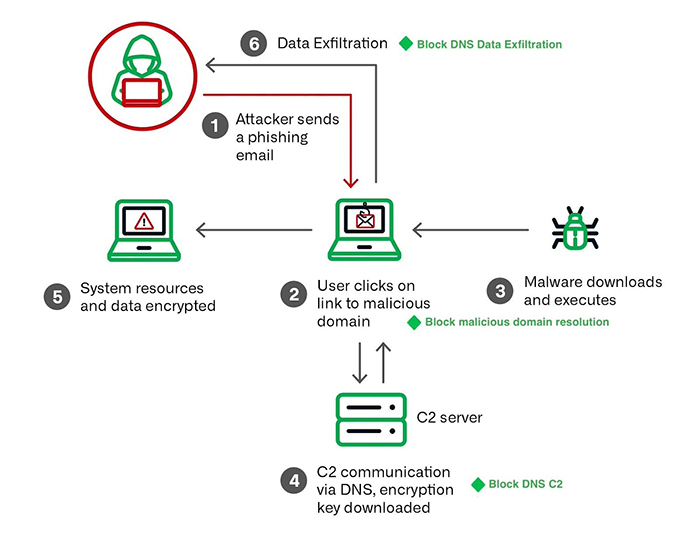
Phishing
Phishing is the primary delivery method for ransomware, with the main goal being to steal user credentials. Once the attacker gets the credentials, it is much easier to access internal networks and systems and encrypt and exfiltrate data before the IT teams can respond.
Protection with DNS: When an unsuspecting user clicks on a phishing link that is part of a ransomware attack, he is taken to the internal enterprise DNS server that will try to resolve the domain. If proactive threat intelligence is used on the DNS server, the user will be blocked from going to the domain because that domain is known to be associated with ransomware. This is the earliest opportunity to disrupt and stop ransomware attacks in their tracks.
C2
Once ransomware has infiltrated a company’s network, and starts executing, it uses Command and Control (C2) communications to download the encryption key onto the end host and encrypt the files. The user is then shown the ransom message from the attacker.
Protection with DNS: This C2 also happens over DNS, and using threat intelligence can block the C2 communications, preventing the encryption key download and the eventual encryption of data.
Data Exfiltration
As the attack progresses, data is often exfiltrated over DNS, to avoid detection by standard DLP solutions. The attacker can then threaten the ransomware victim to pay up or risk getting their data leaked.
Protection with DNS: Using real time inspection of enterprise DNS traffic and streaming analysis, data exfiltration can be detected and stopped as soon as it starts, thereby preventing ransomware actors from getting access to sensitive information.
User and Device Attribution Post Breach
When there is a ransomware attack attempt or a breach, quickly identifying impacted devices and users is key to fast remediation. DNS, DHCP and IPAM data in the Infoblox platform helps SecOps quickly get information of all devices that could be impacted by the ransomware attack, including details such as device type, network location, user and other identifying information.
A Final Word: Hardening Critical Network Services for Resiliency During Ransomware Attacks
Finally, many ransomware campaigns include attacking and disabling the Windows AD (Active Directory) servers to slow any response to an attack and spread chaos. For many enterprise organizations these Windows AD servers still also host DNS and DHCP services, meaning that when the AD server is disabled it can also result in the disabling of mission critical network services such as DNS and DHCP. This can cause the network (or large segments of the network) to also be unusable and critical applications to be unreachable. This results in even longer and more severe business interruptions and inhibits remediation efforts. As such, it is highly recommended that DNS and DHCP servers be separated from your Windows AD server for isolation of duties and better cyber resiliency. Using dedicated enterprise-grade DNS, DHCP and IPAM solutions from Infoblox can help ensure that your critical network services are always up and running, even during a ransomware attack.
Infoblox’s BloxOne Threat Defense uses DNS threat intelligence to disrupt ransomware at the earliest and best opportunity in the attack cycle and delivers precise protection with 0.0002% false positive rate. Learn more here.
Sources:
- https://aag-it.com/the-latest-ransomware-statistics/
- https://assets.sophos.com/X24WTUEQ/at/9brgj5n44hqvgsp5f5bqcps/sophos-state-of-ransomware-2024-wp.pdf
- https://www.cigent.com/resources/blog/ransomware-and-recovery-time-what-you-should-expect#:~:text=A%20cyber%20attack%20can%20last,encryption%20type%20and%20forensic%20investigation
- https://www.securitymagazine.com/articles/100423-report-average-breakout-time-for-intrusive-activity-is-62-minutes#:~:text=A%20report%20by%20CrowdStrike%20revealed,against%20intrusions%20and%20minimize%20damage
- https://www.helpnetsecurity.com/2023/07/20/soc-analysts-tools-effectiveness/











