Generative AI applications have exploded in usage by organizations in the last two years. More than 100 million users are now experimenting and using AI applications. But, as with any new tool, the adoption of GenAI by enterprises introduces unique risks in areas such as security, privacy, legal, safety and organizational reputation. More specifically, risks include the potential exposure of users to malicious domains and confidential data leakage from the use of shadow AI applications.
Organizations must adopt policies, tools and frameworks to manage these risks effectively. This includes implementing preemptive cyber defense approaches that go beyond detection and response, identifying and blocking unsanctioned AI usage and implementing other security best practices.
The Problem of Shadow AI
The problem of shadow AI is impacting almost every organization. A recent study by Software AG reveals that approximately 50 percent of employees in companies are using unapproved AI tools, often referred to as “Shadow AI,” to enhance their work efficiency. Despite potential security risks and corporate policies that prohibit the use of unsanctioned AI applications, employees continue to use these tools because of easy availability and the very positive impact these tools have on their productivity. Due to the fear of reprimands, many employees avoid disclosing their use of shadow AI applications. This results in IT teams not having visibility into AI applications that employees use and the potential risks that come with it.
According to Harmonic, companies averaged 254 AI applications and 45.4 percent of sensitive data submissions came from employees’ personal accounts, such as Gmail. With such widespread use of AI, most of which is unmanaged “Shadow AI,” there are significant risks, which include involuntary exposure of personally identifiable information (PII), such as customer data and employee data, as well as legal and financial data, intellectual property and sensitive code.
The findings underscore the need for organizations to develop proactive strategies to address unsanctioned AI usage. This includes creating policies that balance security concerns with the productivity benefits that these tools offer and integrating approved alternatives that could be more beneficial for both employees and the organization.
Identifying and Blocking Unsanctioned AI Using DNS
In addition to implementing baseline security measures for use of GenAI applications, organizations should use effective strategies to gain visibility into use of AI applications and block or redirect shadow GenAI usage to avoid breaches.
One such simple yet powerful method is to use a Protective DNS solution that can identify when users are accessing unsanctioned AI applications based on their DNS activity. You can then either block that access or redirect them to a corporate sanctioned GenAI application, again using DNS.
Infoblox Threat Defense™ is an industry-leading Protective DNS solution that:
- Uses predictive DNS-focused threat intelligence and algorithmic detections to block cyberthreats across an organization’s entire hybrid, multi-cloud environment
- Has an Application Discovery feature, which provides visibility into the applications used by end users, such as business applications, cloud backup and storage, VPNs, communication tools, email, social networking and of course AI applications. It also points out which unapproved applications are in use by employees and which in-use applications could benefit from a review by the admin.
A key strength of the Infoblox solution is that it is DNS based and can seamlessly leverage your existing DNS infrastructure to provide this security advantage with zero disruption. It delivers value almost immediately as it instantly begins to monitor all DNS activity and provides IT with tools to quickly filter activity to get useful insights and make informed policy decisions.
Using this solution, IT and security admins can:
- Make decisions about which applications to allow, block or simply monitor, including AI applications
- Redirect users accessing an unsanctioned AI application to the corporate approved solution
- Extend these policies to any user, device or workload anywhere—at scale, making it very easy to block unsanctioned AI applications for the entire enterprise
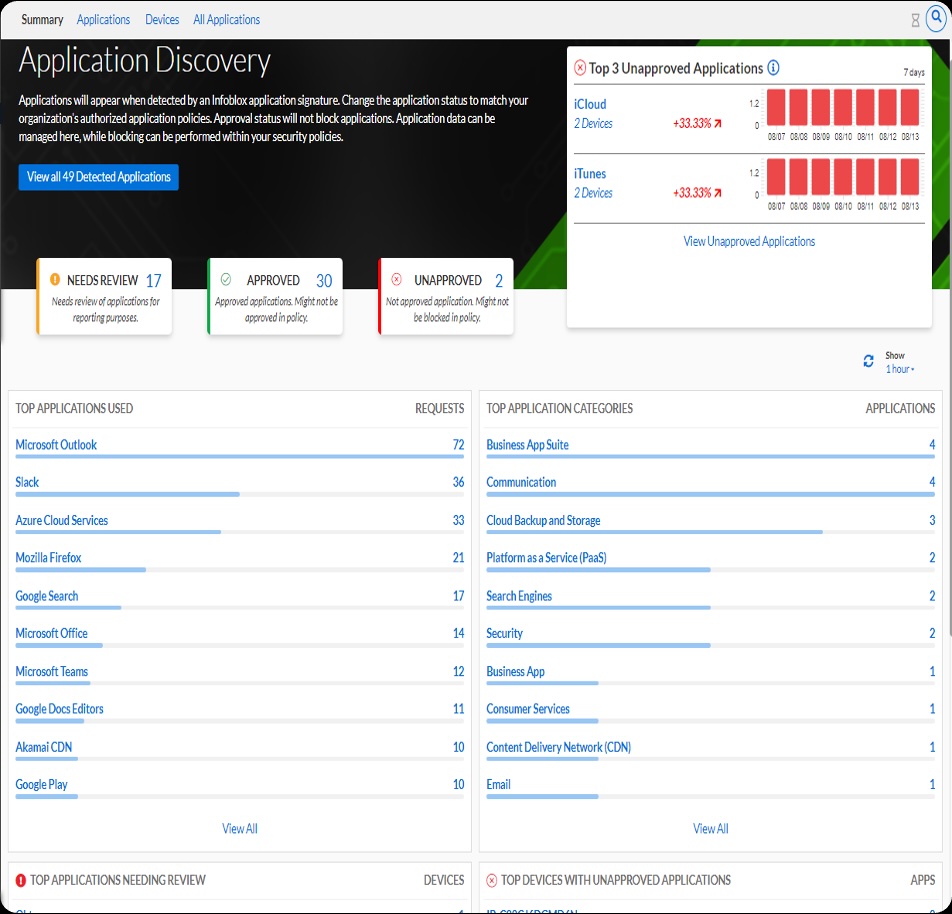
The evolving landscape of AI and the impact on security is significant. With the right approaches and strategies, such as the use of DNS-focused threat intelligence and DNS-based application discovery, companies can get ahead of these risks and ensure that they don’t become patient zero.
Sign Up for a Free Security Workshop
To learn more about managing unsanctioned AI applications and all the ways threat actors can abuse DNS, sign up for a free security workshop here.









