The MITRE ATT&CK™ framework is a comprehensive knowledge base of cyber attacker tactics and techniques gathered from actual observation of attacker behavior. As an important knowledge base, MITRE ATT&CK enables anyone on the cyber defense team to review and contrast attacker activity, and then understand the best options for defense.
MITRE ATT&CK (Adversarial Tactics, Techniques, And Common Knowledge) was developed and released by Mitre Corporation, a nonprofit, in 2015. MITRE does work for U.S. Government agencies in a wide variety of areas.
This white paper provides an introduction to MITRE ATT&CK, an overview of how MITRE ATT&CK is organized, and a description of the matrix and the tactics and techniques that it contains. It also shares information on various attack groups and the adversary emulation plans that might be applicable. Finally, it shares details on the use cases that make MITRE ATT&CK compelling.
MITRE ATT&CK enables you to think like an attacker. Where are the gaps in protection based upon likely threats? This helps you balance your defensive measures against the steps an attacker will take. The end goal in using MITRE ATT&CK is to make better decisions about assessing risks, deploying new security controls, and better defending your network.
Understanding the MITRE ATT&CK™ Framework
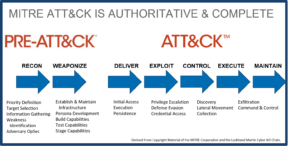
Figure 1: – Cyber Kill Chain® Mapped to MITRE PRE-ATT&CK™ and ATT&CK™
MITRE ATT&CK is not the only cybersecurity framework. There are several other important security frameworks, such as The Lockheed Martin Cyber Kill Chain®, ISO/IEC 27001, the NIST cybersecurity framework, and COBIT. MITRE ATT&CK is distinguished most by the very deep and detailed data on what the attack looks like from the attacker’s perspective. Conceptually, MITRE ATT&CK covers a subset of the Cyber Kill Chain but goes into much greater depth and detail. There is also MITRE PRE-ATT&CK, which helps cyber defenders prevent an attack before the attacker can gain access to the network.
Tactics, Techniques, and Procedures
The MITRE ATT&CK Enterprise matrix provides a navigable taxonomy to all techniques that might involve Windows, Mac, and Linux. Each of the twelve tactics includes from between 9 to 67 techniques that might be used. In some cases, techniques may be used by several tactics. Here is a partial view although not all of the tactics and techniques are visible.
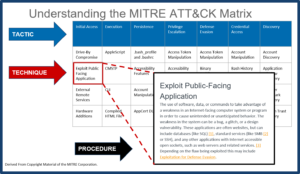
Tactics represent the goals the attacker is trying to achieve. Techniques represent the different ways that cyber attackers can achieve the goals and objectives of the tactic. There you will see data that provides a more detailed explanation of the technique, possible mitigations, and examples of malware associated with the use of this technique by cyber attackers.
In summary, MITRE ATT&CK is a highly powerful open-source tool to understand and classify cyber attacker tactics, techniques, and procedures. By using MITRE ATT&CK, Cyber defense teams can better design a comprehensive strategy for security controls against the likely threats and the tactics and techniques they will exhibit, assess risks, and then prioritize and remediate gaps in the cyber defense.
To learn more, please download our white paper here.
Cyber Kill Chain® is a registered trademark of Lockheed Martin Corporation
MITRE ATT&CK™ is a trademark of The MITRE Corporation
https://trademarks.justia.com/856/75/cyber-kill-85675496.html
https://www.iso.org/isoiec-27001-information-security.html
https://www.nist.gov/cyberframework
http://www.isaca.org/cobit/pages/default.aspx





