Picking up where we left off, let’s take a look at some packet captures using Wireshark that will give us more insight into what’s happening with SLAAC (Stateless Address Autoconfiguration) as it auto-configures an IPv6 address.
Start GNS3 and recreate the topology and configuration from the last post.
In the topology window right click on the link between the router and host. Choose capture then select the interface (if you’ve used the router/host topology, only the router ethernet interface will appear as a choice). Note: if you have enabled the router interface GNS will complain that there is no traffic to capture (even if you have, you may get the error anyway but you should see the router interface in the “Captures” portion of the GNS3 screen).
In the “Captures” window, right click on the interface and choose Start Wireshark.
X11, then Wireshark will start and you should get a screen that looks similar to the one below.
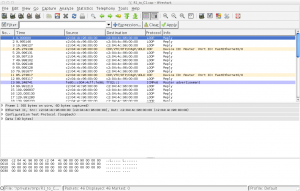
Let’s filter out the packets not related to IPv6 by typing ipv6 in the filter box then pressing Apply.
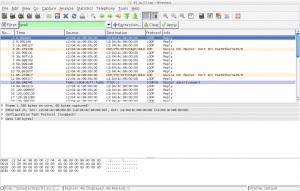
Unless you’ve just configured the IPv6 address you’ll see only router advertisements. Let’s take a closer look at one.
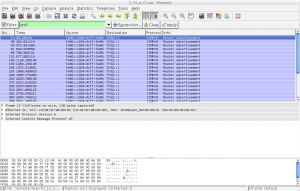
First, expand the “Ethernet II” heading in the middle window.
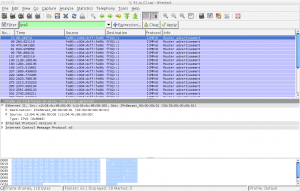
Note the EtherType is set for 0x86DD indicating IPv6. Now expand the “Internet Protocol Version 6″ heading.
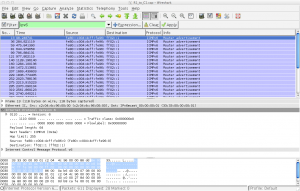
The Next header field is set to a value of 56 indicating that the packet is an ICMPv6 packet. The Hop limit is set to 255 meaning the packet is restricted to the local segment and will be discarded by any routers.
The source address will be the link-local address of the originating router while the destination address is the link-local scoped all-nodes multicast address of ff02::1.
Finally, expand the “Internet Control Message Protocol v6″ heading then the “ICMPv6 Option” subheading.
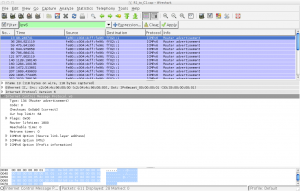
The type of ICMPv6 packet is specified as 134, the code for Router Advertisements and under the “ICMPv6 Option” subheading you can see the advertised prefix of whatever /64 you configured on your router interface (in our example 2001:db8:cafe:1:: ).
Try removing and re-adding the /64 prefix on the router interface. This will generate some other neighbor discovery packets, such as neighbor solicitations and advertisements.
By now, you should have a grasp of how GNS3 can help you “peek under the hood” with IPv6. Be sure to try modeling your particular IPv6 network challenges with GNS3.





