Author: Renée Burton, Kathleen Persighetti
Recently we introduced the concept of DNS threat actors and promised a series of portfolios to share details of actors we track; this article is the first.
Open Tangle is a persistent DNS threat actor that leverages a large infrastructure of lookalike domains to target consumers for phishing attacks. For over a year, Infoblox has been monitoring their network and blocking new domains as they are registered. Open Tangle has been operating since at least Spring 2018, targeting Europe, the United States, Canada and Australia. They use broad, undirected campaigns with links to domains that look like financial institutions and government tax organizations, primarily compelling users with threatening messages about their accounts. While they are known to attack users via SMS messages, it is likely they also use other distribution methods, including spam. Like many of the DNS infrastructure actors we monitor, Open Tangle is resilient and regularly updates their network. They have modified their infrastructure over time, maintaining hundreds of active domains at once and a small set of dedicated nameservers under their control.
This blog describes the techniques, tactics, and procedures (TTPs) of Open Tangle operations from a DNS perspective and their evolution over the past year. It is intended to give defenders information necessary to identify and protect against Open Tangle, but also introduce key concepts Infoblox uses in the taxonomy of DNS threat actors. In particular, we consider how Open Tangle uses DNS nameservers and how their choices help create a DNS fingerprint of the actor. As we introduce more actors in this series, we will also introduce more DNS-specific TTPs and how those are used to separate activity between actors.
Using Personal Attacks for Actionable Intelligence
One of the many ways Infoblox finds leads is through threats seen in our personal accounts. In early May 2022, a member of Infoblox’s Threat Intelligence Group (TIG) received an SMS message claiming to be from M&T Bank, a.k.a. MTB. Since this employee had no prior connection to M&T Bank, it was easy to recognize the phishing attempt that served as a signal for further research that ultimately led us to the Open Tangle network. The first message used a bit[.]ly URL shortener, but the subsequent messages received over the course of several months all used lookalike domains. One text claimed that the individual needed to follow the link in the SMS message in order to resolve an overdraft payment. Another message demanded they follow a link to unlock the account. Figure 1 below shows images of these messages, and shows the actor’s use of lookalike domains to the legitimate MTB website, www3[.]mtb[.]com. Similar MTB texting scams have been reported since 2020,1 and MTB has released multiple statements warning customers that the company will never text anyone a link to resolve any issues regarding their accounts.2
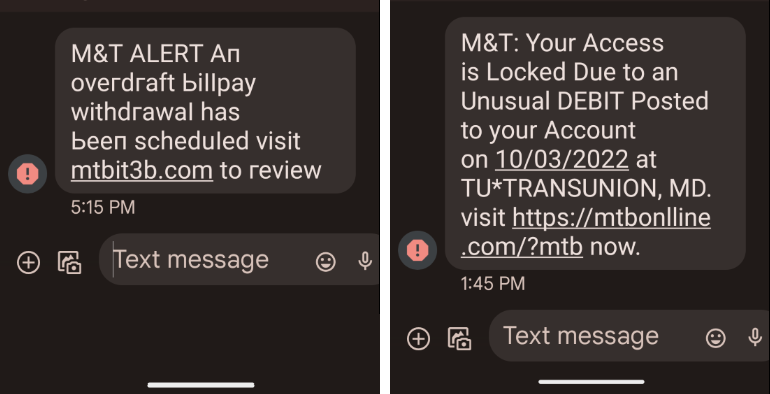 Figure 1: Screenshots of text messages received from the Open Tangle actor.
Figure 1: Screenshots of text messages received from the Open Tangle actor.
While there are a number of phishing actors targeting consumers through financial lures, this DNS threat actor stood out to us because of their consistent use of lookalike domains to a small number of targets. They create several similar domains to the same target organization over a long period of time. For example, in the last year they regularly generated new lookalikes to M&T Bank, America First Credit Union, and the Australian Tax Office. Table 1 shows some of the many variations they have registered to these three organizations.
| Target | Sample Lookalike Domains |
|---|---|
| M&T Bank | mtbsuportz520[.]com, mtbsuportz3[.]com, mtbsuportz15[.]com, mtbsuportz1491[.]com, mtbsuportz09[.]com, mtbsuportz0591[.]com, mtbmobilesup0rts[.]com, mtb1t0psupp0rtz[.]com |
| America First Credit Union | amerlcafirstsupp0rts[.]com, amerlcafirstonline[.]com, americanfirstsupporrts77[.]com, americanfirstsupporrts70[.]com, americanfirstsupporrts42[.]com, americanfirstsupporrts22[.]com, americanfirstsupporrts11[.]com, americafirstsuporrts401[.]com, americafirstsuporrts291[.]com, americafirstsuporrts157[.]com, americafirstsuporrts118[.]com, americafirstsup0rts247[.]com, americafirstsup0rrtz[.]com, americafirstsup0rrts[.]com, americafirstssupport247[.]com, americafirstssupp0rts[.]com, americafirstm0biles[.]com, americafirstm0biie[.]com, america3firstsuports[.]com, afcusecured-inf0[.]com, afcusecured-1nfo[.]com |
| Australian Tax Office | myato-syncsdata[.]com, ato-mygov1[.]com, mygovvtaxfile[.]info |
| Table 1. Examples of domains registered by Open Tangle that mimic financial and government institutions. | |
In early 2023 the actor conducted attacks using SMS messages and targeting Australian residents. They registered a few dozen domains along a tax theme. As shown in Figure 2 below, the user would receive an SMS prompting them to enter a code on a website that mimics the Australian Government services portal. Regardless of the organization being imitated, in all cases where we were able to capture landing page images, the user was prompted to log in to a personal account. Open Tangle appears to exclusively gather user credentials through lookalike domains and fake websites, rather than malware distribution.
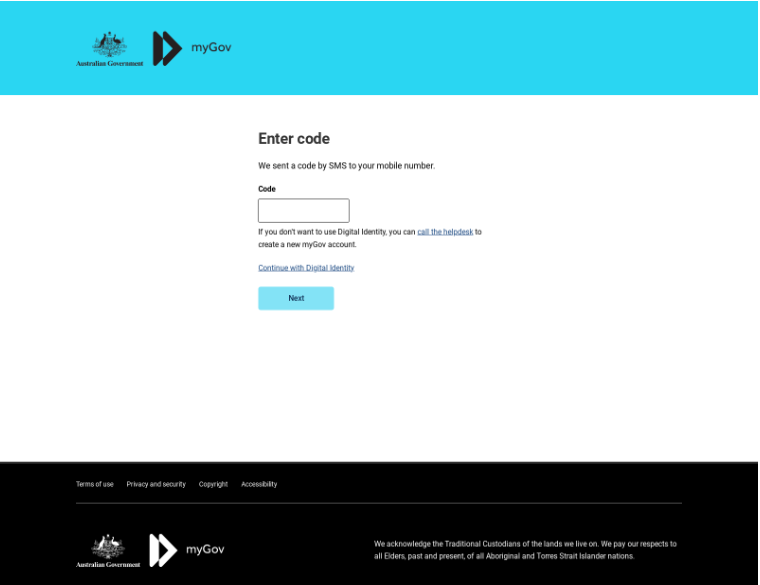 Figure 2. Site targeting Australian taxpayers in February 2023 via SMS, using the domain ato-mygov1[.]com.
Figure 2. Site targeting Australian taxpayers in February 2023 via SMS, using the domain ato-mygov1[.]com.
Dedicated Name Servers
When defining a taxonomy of DNS threat actors, distinguishing between them, and identifying their TTPs, one major behavioral characteristic is how they utilize DNS name servers. Depending on their experience and their operational requirements, DNS threat actors may rely on other providers to act as name servers for their domains, or they may manage their own. Beyond that, there are a number of other choices that an actor makes related to name servers, including the use of shared hosting providers like GoDaddy or NameCheap. A dedicated name server is one that is used solely for the purpose of that DNS threat actor’s operations and is not shared with other users. The use of a dedicated name server allows the actor to track the IP address of the requesting client, and make decisions about how to respond based on that information.
Open Tangle uses dedicated name servers, and they do so in a fairly unusual manner. Dedicated name servers are not common, but also not rare. They are used by spam actors for the purpose of tracking email distribution and for controlling the distribution of malicious IPs based on geographic location. It is uncommon, however, to use them as Open Tangle does. Instead of a single dedicated name server, Open Tangle operates a small set of name servers that change over time. The actor will rotate a domain through these dedicated name servers, as well as parking and cheap hosting providers, over time. An example of this behavior is seen in Table 2 below, which lists the name servers serving the domain samcrte[.]com over a two year period. The domain name foundationapi[.]com is used as a name server for expired and parked domains by OrderBox and other providers. The 6 other name servers in the table are controlled by Open Tangle.
| Date | Name Server |
|---|---|
| Aug 2021 | allignmentstyles[.]xyz |
| Oct 2021 | allowedvillage[.]xyz |
| Nov 2021 | allignmentstyles[.]xyz |
| Jan 2022 | aryjewellerymark[.]xyz |
| Jan 2022 | samcrte[.]com |
| Apr 2022 | hostergeek[.]com |
| Apr 2022 | samcrte[.]com |
| Apr 2022 | aimdaddy[.]com |
| Apr 2022 | samcrte[.]com |
| Aug 2022 | foundationapi[.]com |
| Aug 2022 | samcrte[.]com |
| Aug 2023 | foundationapi[.]com |
| Sep 2023 | samcrte[.]com |
| Table 2. The name servers assigned to the domain samcrte[.]com since August 2021. | |
In fact, Open Tangle’s tactic of irregularly rotating name servers is what originally stood out to us. The depiction in Figure 3 depiction of the Open Tangle network shows both actor-controlled name servers and name servers operated by budget providers. Each node in the graph is a domain, where the central nodes are name server domains. A connection between a name server and a peripheral node shows that the name server served the domain at some point. The color of the node corresponds to the registrar for that domain name (Open Tangle uses multiple registrars). This snapshot was taken in October 2022 and has helped us understand the network evolution at a high level.
- The name servers andrioddeveloper[.]xyz and backstagestory[.]top were active in 2019 and served a number of the same domain names, many of which were registered with the Public Domain Registry, PDR Ltd. At the time, the domains were predominantly created using a registered domain generation algorithm (RDGA). The name servers were used in 2019-2020 and were part of a rotating set at the time. Domain names are seen on several TLDs, including xyz, com, and top, including several lookalike domains secure-wellsco[.]xyz and chase-invoice[.]xyz.
- In contrast, the name servers samcrte[.]com, aimdaddy[.]com, and 700eteries[.]xyz serve domains largely registered with NameSilo and NameCheap. These three examples are part of a group of servers active in 2022-2023. This set contains some RDGA domains, but starting in Spring 2022, an increasing percentage of the domain names have been lookalikes.
- The name servers serversorbit[.]com, hostdns[.]web[.]bs, and megaacshost[.]com in contrast serve domains from a large breadth of registrars and also serve domains unrelated to Open Tangle.
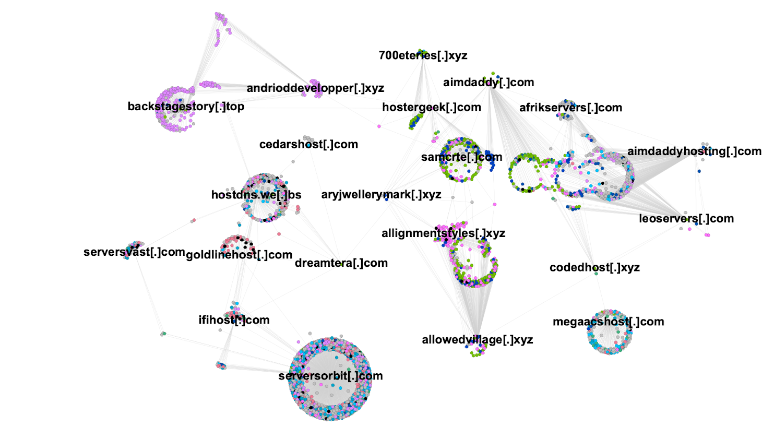 Figure 3. A retrospective view of the network of name server domains and hosted domains derived from Open Tangle campaigns from October 2022. The color of each node corresponds to the registrar of the domain. The labeled domain names all served as name servers between January 2021 and October 2022.
Figure 3. A retrospective view of the network of name server domains and hosted domains derived from Open Tangle campaigns from October 2022. The color of each node corresponds to the registrar of the domain. The labeled domain names all served as name servers between January 2021 and October 2022.
Over time, Open Tangle abandons their name server domains and allows them to expire. Several of the domains observed in October 2022 are no longer active. They also tend to use their phishing domains for only a short period of time. When they abandon a domain they usually assign it to a common parking provider or domain reseller. In Figure 4 we show some of the Open Tangle name servers observed over the last year with a representative connection to the phishing domains they served, and whether those domains are actively resolving in October 2023. Notice that while samcrte[.]com and 700eteries[.]xyz are still heavily used for phishing campaigns (blue), the domain allowedvillage[.]xyz is no longer registered and none of the phishing domains it served are active any longer (red).
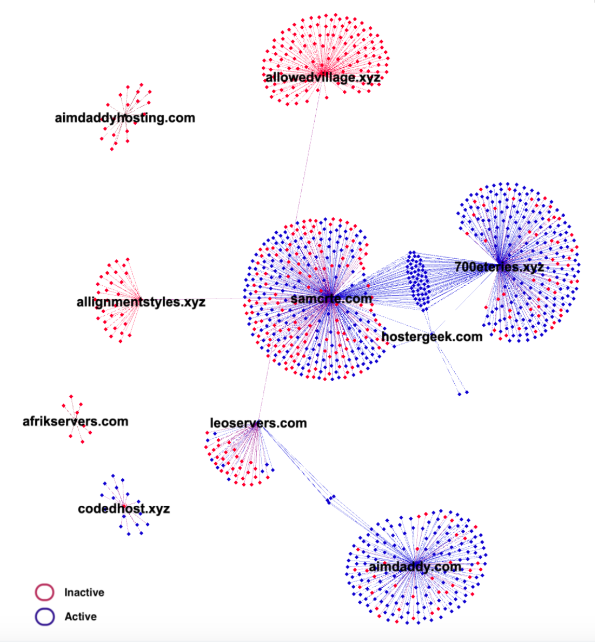 Figure 4. A current partial view of the Open Tangle name server network in 2023. Each domain is a name server domain and each peripheral node is a phishing domain. Many of the phishing domains are no longer active.
Figure 4. A current partial view of the Open Tangle name server network in 2023. Each domain is a name server domain and each peripheral node is a phishing domain. Many of the phishing domains are no longer active.
Between Figures 3 and 4, we see that Open Tangle uses multiple name servers at one time, cycling them as we illustrated in Table 1. In addition, they temporarily use budget providers, typically located in India or Pakistan, and eventually park and abandon their name server domains. They use fairly unusual name server domains that are often designed to resemble hosting providers or shopping sites. The way Open Tangle creates and uses name servers during their operations is distinct from other DNS threat actors we track.
Lookalike Phishing
Aside from the unusual manner in which Open Tangle uses dedicated name servers, they are also distinguished by their phishing domains. They register predominantly lookalike domains, that is domains that are intended to look like well-known legitimate domain names, and they do so in small batches over a long period of time. For the past two years, they have primarily targeted consumers with banking and tax lures, but in the past they have created lookalikes to entertainment and shipping companies.
The domains registered by Open Tangle are lookalikes, but they are not particularly clever. For example, the domain lnfoblox[.]com is a far more convincing lookalike to infoblox[.]com for the average user than mtbsuportz865[.]com is to mtb[.]com (the primary domain for M&T Bank in the United States). All of the text messages our staff received included some kind of threat, and Open Tangle may rely on the reactive fear of consumers to click through to their fake website without carefully examining the message.
Relative to other DNS phishing actors, Open Tangle is not particularly prolific; they create a handful of domain names each week, often centered around a single legitimate organization, and then use them for a short period of time. For example, in the few days surrounding August 7, 2023, Open Tangle created a number of lookalike domains that mimic Houston Federal Credit Union, including:
- h0ust0nfcu[.]org
- h0ust1nfcu[.]org
- houstonfcuoniine[.]org
Campaigns using these domains were then conducted in mid-to-late August 2023. Because Open Tangle phishing campaigns are so widespread, sending undirected SMS messages to consumers, and are blatant copies of well-known institutions, their phishing domains are quickly identified by security vendors.
Conclusion
Lookalikes are ever present in today’s threat landscape. They are a common tool threat actors use to target and deceive consumers for financial gain. The ability to register domains cheaply and quickly makes these broad spectrum attacks challenging to defend against; the user is often the one left to defend themselves. Open Tangle is just one of many actors who use this technique. For a comprehensive discussion of the threat posed by lookalikes, see Infoblox’s whitepaper “A Deeper Look at Lookalike Domains,” which includes an analysis of over 300,000 lookalike domains during a one-year period.
What makes Open Tangle interesting as a DNS threat actor is less their use of lookalike domains than the way in which they manage and assign their name servers. While the phishing domains they register are quickly detected, we have found that the dedicated malicious name servers go largely unnoticed. As such, the information security community does not recognize this net of phishing campaigns, conducted over at least a five year period, as a related group. Protection is also reactive, responding to online phishing content after it is published rather than stopping the activity before it is started.
Infoblox BloxOne Threat Defense Essentials and Advanced customers are protected against Open Tangle, including new domains as they are configured. A selection of their indicators of compromise (IOCs) is found below and in our GitHub repository.
| Indicators of Open Tangle Phishing Domains | ||
|---|---|---|
| americanfirstsupporrts69[.]com | mtbsuportz92[.]com | mtb3quickverif[.]com |
| mtbwebverif3[.]com | nbtsupp0rt07[.]com | mtbsuportz865[.]com |
| mycitibankunion[.]com | mt3bsupports[.]com | mtb-securem0bile[.]com |
| mtbsuportz642[.]com | americafirstsup0rts247[.]com | mtbsuportz4[.]com |
| mtb1t0psupp0rtz[.]com | nbtsupp0rt2[.]com | mtbsup0rtsonllne[.]com |
| mtbsuportz912[.]com | citizensverly0[.]com | mtbsuportz385[.]com |
| ato-mygov1[.]com | nbtsupp0rt1[.]com | mtbsuportz661[.]com |
| mtbsuportz05[.]com | americanfirstsupporrts22[.]com | americafirstsup0rrtz[.]com |
| mtb-customer[.]com | qadriyasubhaniya[.]com | mtbsupoprtsonlines00[.]com |
| americafirstsuporrts112[.]com | mtb3mobiie[.]com | mtbonlinesupports3[.]com |
| mtb10reviews[.]com | mtbsuportz9264[.]com | americanfirstsupporrts30[.]com |
| mtb0nlinewebverifl3[.]com | mtbonllnesup0rts[.]com | apexebank[.]com |
| allignmentstyles[.]xyz | allowedvillage[.]xyz | aryjewellerymark[.]xyz |
| samcrte[.]com | hostergeek[.]com | aimdaddy[.]com |
Endnotes
- https://www.cbsnews.com/newyork/news/scam-alert-texts-m-t-bank/
- https://www3.mtb.com/personal/personal-banking/fake-text-message-signs







![[Video] Changing Definition of Core Networking and Enterprise Expectations on Security](https://blogs.infoblox.com/wp-content/uploads/480288900-660x454-1.jpg)
