Author: Andreas Klopsch
TLP: WHITE
1. Executive Summary
In December 2020, the Infoblox Cyber Intelligence Unit discovered a spam actor we call WhiteSawShark. This actor targets a wide audience through campaigns that deliver Agent Tesla, FormBook, Loki, Remcos, Snake, and other infostealers and remote access trojans. The actor also uses a custom downloader, which we designated HadLoader.
We discovered WhiteSawShark by tracking spam campaigns sent from a set of recurring similar domains. Through analysis of the malware distributed from this infrastructure, we uncovered 16 additional domains, which serve as C2 servers and spam distribution servers.
Our analysis revealed that WhiteSawShark sent two types of malicious attachments: Rich Text Format (RTF) documents that exploit vulnerability CVE-2017-11882, and archives that contain the final payload in compressed form during this study period. All the malware families that we saw WhiteSawShark distribute are available as malware-as-a-service (MaaS).
2. Discovery
In December 2020, multiple spam campaigns were sent from the same SLD. The campaigns delivered an RTF document weaponized with the CVE-2017-118821 exploit, which (1) downloads an infostealer from a malware distribution server and (2) executes it. The families of downloaded malware were not the same for all campaigns but are all known Stealers offered as MaaS.
Figure 1: An example of one of the campaigns we identified

In January 2021, we discovered that two other groups of malspam campaigns were using the same payload URL host as the one used by the first group of campaigns. These campaigns were also distributing archives and RTF documents weaponized with a CVE-2017-11882 exploit, and they all shared the same payload URLs for downloading malware. These domains were using a different hostname generator.
Figure 2 shows a representation of sender hostnames for spam that ultimately downloaded malware from a shared payload URL host. The thickness of the line, or edge, indicates the number of unique payload URLs observed to have originated in a spam email from the hostname and have led the victim to malware on the hosting site. It is possible that the actor used these pairings more heavily or that our observations were limited for certain campaigns, and this has skewed the data.
Figure 2: A sample of the sender hostnames for spam that downloaded malware from the payload hosting site
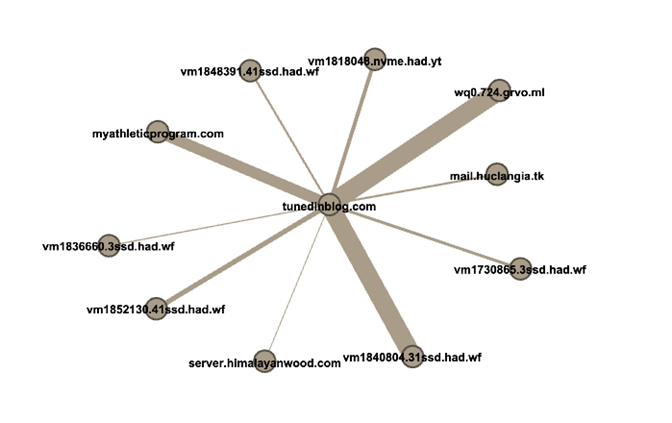
These discoveries enabled us to find thousands of malicious spam emails that were targeting a wide audience: mostly English speakers, but also Italian, Hungarian, Polish, Spanish, and German speakers.
3. Infrastructure
We have identified more than 50 SLDs that have been distributing malicious spam since January 2021. In addition, there are domains that seem to serve multiple purposes for the spam actor (see the green segment Third Group in Figure 3). From 1 January to 9 April, the majority of malspam came via the second group.
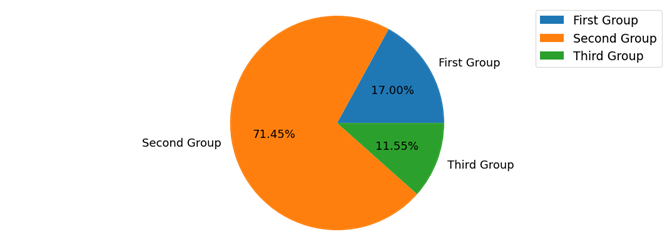
First Group
In the first group, we included all domains related to a single SLD, which has been active since July 2020 or earlier. The domains in this group are used mainly to deliver malspam. In rare cases, the domains are used to distribute malware or are embedded in malware configurations of at least Agent Tesla.2
Figure 4 shows the volume of emails we observed over three months: from 1 January to 9 April. In our data, we have observed multiple campaigns sent from this group.
Figure 4: Frequency analysis of malicious spam received from the first group
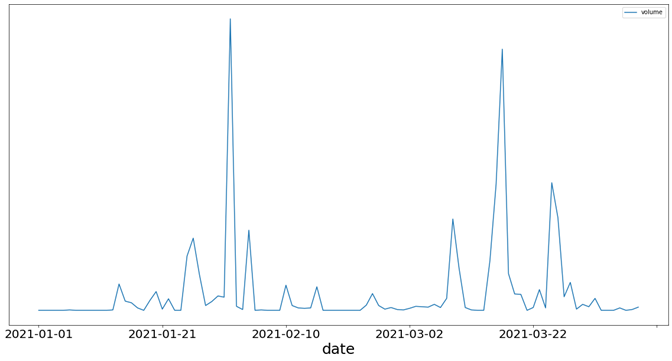
The spikes on 1 February and 17 March are significantly larger than those for the other daily counts. The spike on 1 February was related to the campaign that was distributing malware over the payload URL host tunedinblog[.]com, which we introduced in Section 2: Discovery. The spike on 17 March represents a malspam campaign in which the first group delivered RTF documents weaponized with a CVE-2017-11882 exploit that ultimately downloaded its final payload from the discordapp[.]com content distribution network (CDN).
Second Group
The second group includes multiple SLDs. All domains in this group use one of four country code TLDs such as [.]ml, [.]cf, and [.]ca, and all these TLDs offer free domain registration.
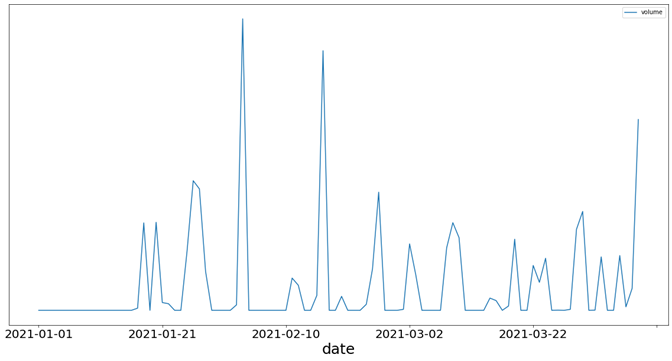
Figure 5 shows the volume of email traffic we observed from the second group over the same period: 1 January to 9 April. A comparison between this traffic and that shown for the first group in Figure 4 suggests that the campaign kick-offs from this part of the infrastructure were more frequent. In most cases, there was a break of two to three days between larger waves.
Figure 5: Frequency analysis of malicious spam received from the second group
Third group
Apart from the members of the groups described above, during this study we identified 16 other domains related to WhiteSawShark. Many of these domains were embedded in configurations that were extracted from the malware distributed by WhiteSawShark. Occasionally, these domains were also used to send out spam.
We observed this tactic of using domains for both mail distribution and hosting malicious content in the campaigns launched by the threat actor WordyThief, on which we reported last year.3 We do not know why these actors repurposed a portion of their infrastructure.
4. Delivered Payloads
From 1 January to 9 April, we observed WhiteSawShark delivering either archives or RTF documents that exploited CVE-2017-11882 as the initial attack vector in our own data. Figure 6 shows the types of attachments that we observed WhiteSawShark deliver from 1 January to 9 April.
Figure 6: Types of attachments that WhiteSawShark delivered from 1 January to 9 April
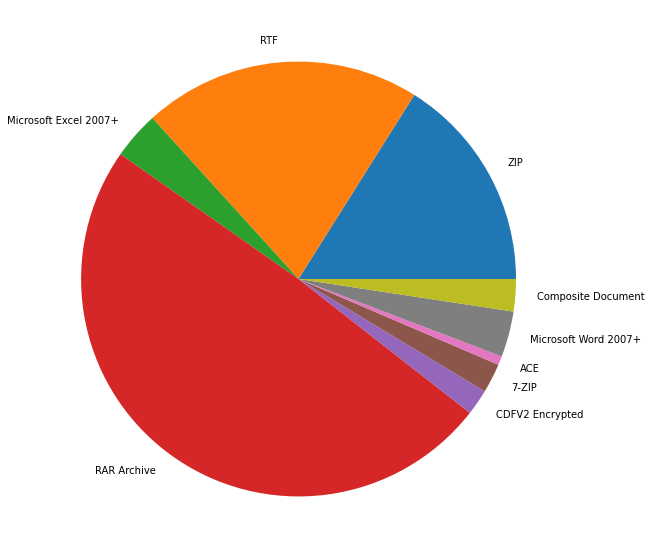
We have not seen WhiteSawShark use custom malware. Instead, the actor uses malware families that are available as malware-as-a-service (MaaS). In addition, the actor consistently uses a downloader that we have not seen publicly discussed before, and we designated it HadLoader.
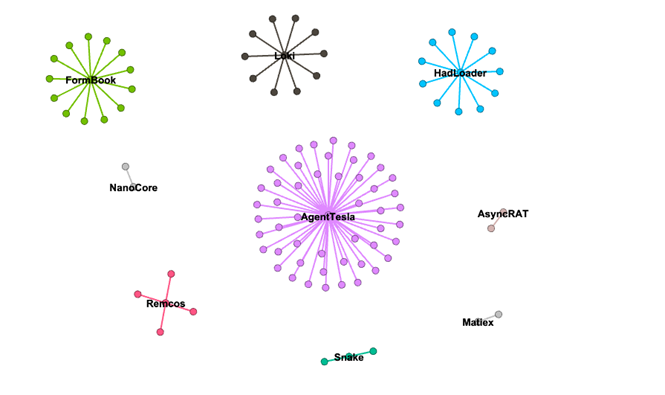
Figure 7 shows a plot of the malware families that we observed WhiteSawShark distribute early this year. The center node is the malware family, and the connected nodes are the distinct SHA256 values of the attachments that dropped the connected malware family. Out of the infostealers and RATs that the threat actor delivers across the campaigns, WhiteSawShark appears to prefer Agent Tesla.
Figure 7: Types of malware that WhiteSawShark distributed in early 2021
5. HadLoader
Since February 2021, we have seen the threat actor use a custom downloader that we refer to as HadLoader. It is written in .NET and serves as an additional stage for delivering the final malware payload. It has gone through multiple changes over time, such as the following:
- Changing the payload delivery mechanism
- Using different C# obfuscation
- Making minor changes in the encryption of strings
- Varying the number of HTTP requests that download the final payload, from 1 to 3
However, HadLoader’s decryption flow and algorithm have not changed very much.
HadLoader tries to download the final payload via an HTTP request from a malware distribution server. Depending on the variant, HadLoader then downloads the payload in one or multiple HTTP requests. If HadLoader downloads the payload in parts, it (1) concatenates and decrypts all of them, by using a substitution cipher with a hardcoded obfuscated key, and then (2) executes the payload. Here is an example of ASCII text downloaded from coroloboxorozor[.]com:
Figure 8: An ASCII text downloaded from a malware distribution server
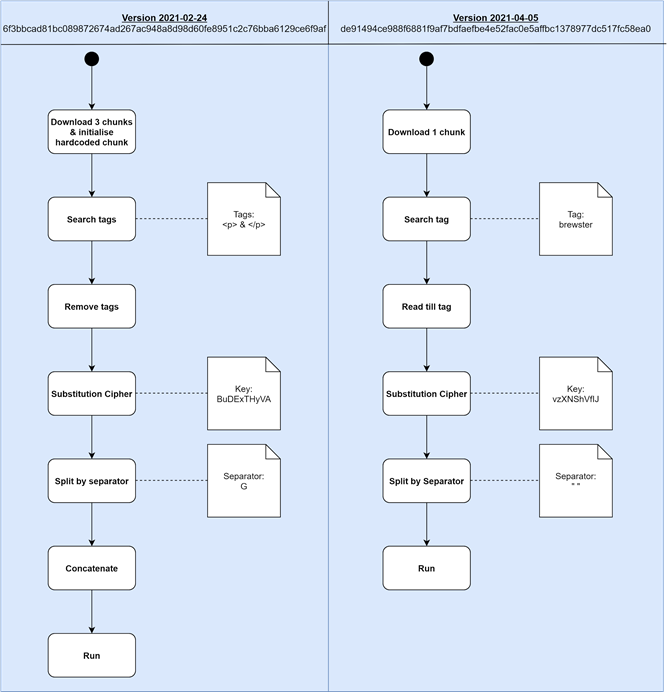
Figure 9 shows a comparison of the decryption flows between a late-February sample and an early-April sample. In the first, HadLoader downloaded three segments and embedded an additional piece in the downloader itself. It decrypted all parts, concatenated them, and then ran the malware in memory. In the April version, it downloaded one segment rather than three, but the core logic of the decryption did not change.
Figure 9: Comparison of the decryption flows for samples collected from 24 February to 5 April
6. Conclusion, Recommendations and Mitigation
This report provides security departments with a detailed analysis of the malicious spam actor WhiteSawShark. The insights on its infrastructure and payloads should help security experts proactively build defenses against the malspam sent by this threat actor.
We expect that WhiteSawShark will continue to target companies and individuals through spam, and we recommend the following preventive actions against WhiteSawShark and actors with similar behavior:
- Install an endpoint protection system. Antivirus (AV) systems should be able to detect the payloads because the actor tends to use malware families offered as MaaS that are well known and detected by AV solutions.
- Use a DNS security solution for email. BloxOne Threat Defense can detect WhiteSawShark’s C2 domains and customers can use Infoblox’s Threat Intelligence Data Exchange (TIDE) to generate blocklists for these types of spambots.
- Always treat attachments with caution. Email is a popular infection vector. If the origin or intent of an email is uncertain, contact the company’s security team.
Endnotes
- CVE-2017-11882 is a popular target for exploitation by threat actors because there are quite a few proofs of concept for it and a lot of documentation about it on the Internet
- https://urlhaus.abuse.ch/host/vm1662026.3ssd.had.wf/
- https://docs.apwg.org/ecrimeresearch/2020/56_Wordythief-AMaliciousSpammer_20201028.pdf





