Author: Yadu Nadh
TLP: WHITE
Overview
On 26 January, Team Cymru posted an update to their analysis of the GhostDNS exploit kit.1,2 Their report detailed an ongoing GhostDNS campaign that targets unsuspecting users by compromising and changing the DNS of their router to deliver phishing websites. NetLab has also reported on this campaign.3
Customer Impact
GhostDNS is an exploit kit that threat actors can use to change DNS settings to route victim requests for certain websites to phishing pages on malicious servers.4 Requests for other sites use a secondary, usually public, server such as Google’s public DNS server. This feature allows threat actors to avoid detection for long periods of time.
Campaign Analysis
This campaign targets more than 70 different types of routers with weak passwords or unpatched vulnerabilities to redirect victims to phishing websites that steal user credentials. The threat actor appears to be targeting Brazilian banks located in Brazil and Argentina, and their customers.
Attack Chain
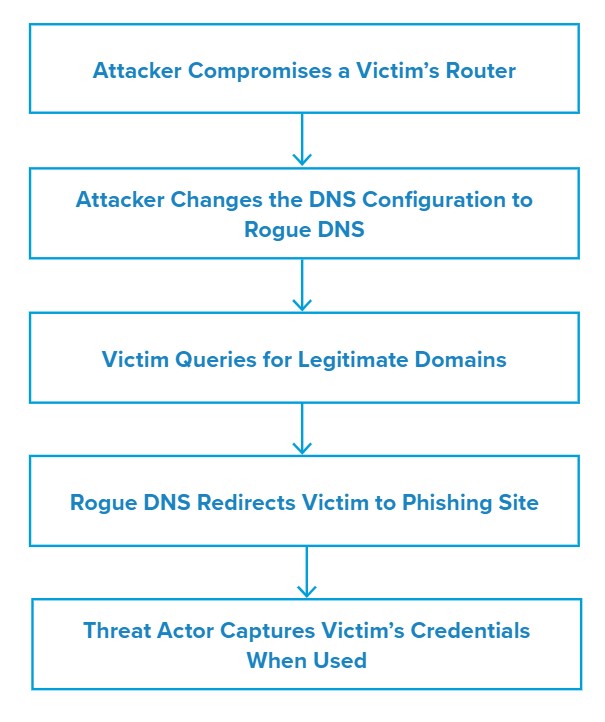
In this campaign, the threat actor scans the internet for vulnerable routers and uses known vulnerabilities or guesses passwords to gain access. They may also bypass the authentication through the dnscfg.cgi exploit.
Once they have gained access, the threat actor then changes the router’s DNS configurations to an actor-controlled Rogue DNS server via the DNS configuration interface.
When the victim queries a specific domain, the Rogue DNS server redirects them to a phishing domain that the actor can use to steal the victim’s credentials or lure them into downloading and executing malware.
Vulnerabilities & Mitigation
This campaign targets routers that are misconfigured or unpatched. Infoblox recommends the following actions to reduce the risk of this type of infection:
- Keep routers up-to-date with the latest security patches to block known vulnerability.
- Configure the router with strong username and password.
- Do not enter credentials without verifying the source
Endnotes
- https://team-cymru.com/blog/2021/01/26/illuminating-ghostdns-infrastructure-part-3/
- https://team-cymru.com/blog/2020/09/08/illunimating-ghostdns-infrastructure-part-1/
- https://blog.netlab.360.com/70-different-types-of-home-routers-all-together-100000-are-being-hijacked-by-ghostdns-en/
- https://decoded.avast.io/simonamusilova/ghostdns-source-code-leaked/









