1. Executive summary
During the weekend of 19 March, Infoblox observed multiple email spam campaigns running scams and exploiting Russia’s invasion of Ukraine. War-related text appeared in the subject line or body section of the emails. For reporting purposes, we have grouped these campaigns according to the following social-engineering tactics:
- Baiting email recipients with giveaways of fake gift cards
- 419 scam, which is also known as the Nigerian prince or the advance fee scam
- Charity fraud
Many of these campaigns have been operating since early March. We have seen few changes in their message templates over the past couple of weeks. We suspect that the scam operators continue to reuse most of the message templates because they are effective.
2. Analysis
Many of the spam campaigns described in the following sections began as early as 8 March and continue to operate at the time of this writing. We have observed three common social-engineering tactics across the campaigns: baiting with gift cards, 419 scam, and charity fraud.
The gift card scams exploit the names of famous retail brands and use buzzwords to tempt victims to click links to fraudulent landing pages, where the victims are prompted to fill out web forms with personal details. Notably, the URLs use newly registered domains that are configured with mail exchange (MX) records and are used to send the spam emails.
419 refers to a group of scams that claim to offer their targets the opportunity to earn commissions by handling transfers of large amounts of money. Usually, the sender of the scam email claims to be a government official; in the campaigns we have observed, the sender has provided a backstory about a Ukrainian father who died in the Russia-Ukraine war and left millions of dollars in inheritance.
Ukraine-related charity scams have been using a number of newly registered domains, and we have been tracking these scams since late February.1 The domains we observed during the weekend of 19 March were distributed via spam emails.
2.1 Gift Card Scam
From 9 to 20 March, we saw a large spam campaign use Ukraine-themed emails that contained fake gift cards with messages that enticed users to click links to scam websites. At the end of the body text, the emails contained random text copied from wikipedia.org; this is a common technique used by cybercriminals to bypass email filters that are based on text sequences. For an example, please refer to Appendix 1.A.
The campaigns advertised gift cards by exploiting names of famous retail brands and text related to the Russian invasion of Ukraine and its impact on the global economy. The subject line of the emails typically began with a flashy word, such as congratulations or bonus, and this word was followed by an enticing label, such as KOHL’s Gift Card, YouTube Gift Card, Ukraine Crisis Gift Card, Amazon Gift Card, WaMart Gift Card, Sam’s Club Gift Card, or Inflation Gift Card.
In the email body, the link that redirected to a fraudulent website contained a newly registered domain that, at the time of this writing, is wholly malicious and owned by the spam operator. The domain is used to send the spam emails and redirect the victims to fraudulent websites that, in turn, prompt the victims to fill out a web form or survey and to provide personal details.
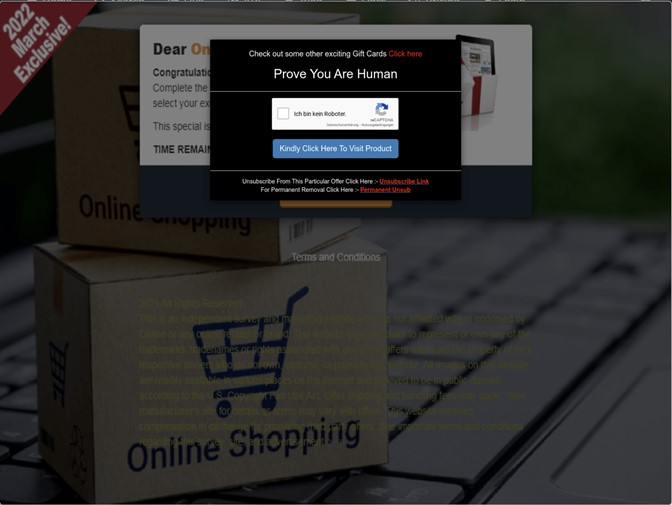
Figure 1 shows a landing page for one such website, hXXps://www[.]shopingmaster[.]com/v1/gp/.
Figure 1. The landing page of a website involved in a gift card scam
2.2. 419 Scam
Since 8 March, a spam campaign has been using not only the social-engineering tactics similar to those used in 419 scams but also a backstory related to the Russian invasion of Ukraine. One of these emails claims to contain a letter sent on behalf of Mrs. Bohdana Boguslaw, a fictitious character. The letter is a lengthy message in English and Dutch and claims that Bohdana’s husband, Andriy Boguslaw (also a fictitious character), was killed by Russian soldiers in Ukraine. The letter also claims that before his death, Andriy revealed to his family that he had stored 16 million euros in a vault and had instructed the family members to find a trustworthy person to help transfer the funds outside of Ukraine. The message instructs the email recipient to contact the sender via helpukraine[@]manavadhikarprotection[.]com so as to negotiate a transfer fee and to coordinate the logistics of the transfer.
The scam operator crafted the email by using spoofed email addresses, such as info[@]ukraine[.]com, and the From name INFO UKRAIN. However, the reply-to address was set to ukraine[@]manavadhikarprotection[.]org. The sender used the domains manavadhikarprotection[.]com and manavadhikarprotection[.]org, which belong to a human rights advocate group based in India. We suspect that both domains have been compromised and are no longer managed by the original content creator.
On 19 March, we observed a different campaign: a 419 scam that was using emails crafted with the From name Mark and the From email address carlos[@]carlauto[.]net. The emails of this scam contained less text than is typically used in campaigns of this kind. The emails impersonated Halifax, a division of Bank of Scotland, and tried to entice the recipients with a 30% commission fee in reward for participating in an alleged transfer of 76 million dollars. The emails instructed the recipients to send personal details to markgrantcharity3322[@]outlook[.]com. Both the Reply-to email address (markgrantcharity33322[@]gmail.com) and the contact address within the email body shared similar email usernames but different email domains.
Figure 2. A short 419 scam message
| Halifax bank PLC on behalf of UNICEF have released the Charity cash transfer of 76,000,000$ to assist the less privilege and Ukraine refugees that have escaped as a result of the Russian Invasion for a 30% compensation. Indicate if you are interested in handling this reputable charity project by providing your Identity & details to this email to commence this project. Mark Mark Email:markgrantcharity3322[@]outlook[.]com Tel:+1(201) 644 6843 |
2.3. Donation Scam
Earlier this month, we shared a list of fraudulent domains that scammers use to redirect donations to their own wallets. We continue to observe this type of activity, and cyber criminals continue to combine spamming and impersonation tactics to reach a larger audience.
The example below shows how a spam campaign attempted to lure email recipients into making donations to support victims of the Russian invasion of Ukraine. The simple and short email message requests donations in bitcoin (BTC):
Figure 3. The message of an email from a donation scam
| Please help us to make a difference in the life of millions of people in need of shelter. food and medical supply in the on going Ukraine Invasion. By donating on our website via BTC http://www[.]giveaidint[.]org/ |
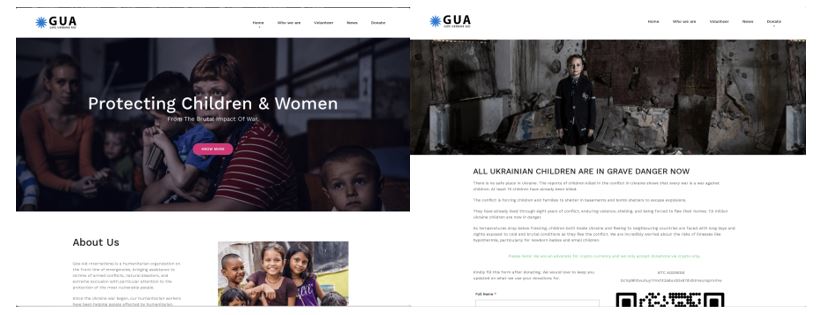
To make the giveaidint[.]org website appear authentic, the scammers use images and descriptions of war victims. However, the website does not provide substantive information about how donations would be managed, and it offers only bitcoin as an acceptable payment currency.
Figure 4. Content on giveaidint[.]org: a website implicated in running a donation scam
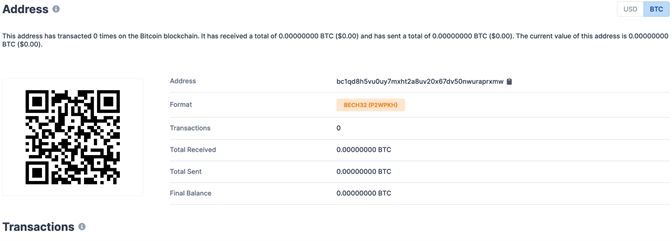
The bitcoin blockchain transaction history shows that the bitcoin address bc1qd8h5vu0uy7mxht2a8uv20x67dv50nwuraprxmw has zero transactions, a common behavior among new and fake donation wallets.
Figure 5. Blockchain transaction history (source: blockchain.com)
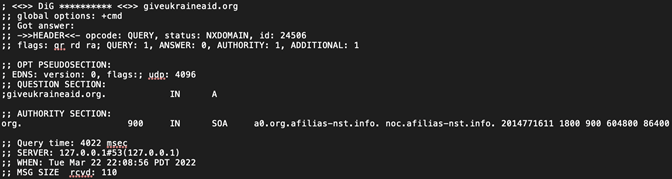
On 13 March 2022, the actor registered giveaidint[.]org with Namecheap and configured it to the IP address 170[.]10[.]163[.]32. We also found two additional domains that we consider likely to be affiliated with the same scammer: giveukraineaid[.]org and taewong[.]com. giveukraineaid[.]org was registered on 8 March 2022, but the following DNS request response indicates that the domain has been suspended.
Figure 6. The NXDOMAIN (“Non-Existent Domain”) error response for giveukraineaid[.]org
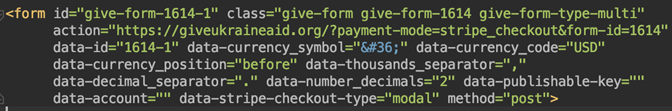
When we analyzed giveukraineaid[.]org, on 10 March, the domain’s web page showed the logos of PayPal and Stripe, which are well-known payment-processing services. However, these services were not integrated into the web page, and we could not determine that any network requests were sent to them. Instead, the page was set up to send form data for credit card information back to itself.
Figure 7. A snippet of giveukraineaid[.]org’s form-submission code
We also observed that taewong[.]com is configured to redirect users to taewoong[.]com, which belongs to a legitimate steel-manufacturing company based in South Korea. Interestingly, we found that subdomain taewong[.]giveaidint[.]org was assigned to 170[.]10[.]163[.]32 and configured on the same date that taewong[.]com was registered. The default page of taewong[.]giveaidint[.]org shows an index directory that is almost empty.
Figure 8. Index directory for taewong[.]giveaidint[.]org
We believe it is not a coincidence that taewong[.]com and giveaidint[.]org were configured at nearly the same time, and in several areas share identical or have similar infrastructure data. This leads us to assess that both domains are probably owned by the same entity.
3. Prevention and mitigation
All of the campaigns described in this report use email as an attack vector. Many of the emails distribute malicious URLs that perform multiple redirects of victims to other fraudulent landing pages. We recommend the following mitigation and prevention methods for strengthening security controls over email, HTTP, and DNS:
- Always be suspicious of vague or empty emails, especially those with prompts to open attachments or to click links.
- Check whether an email’s Reply-to address or the sender’s address is affiliated with the advertised organization. A mismatch would suggest that an email is spoofed.
- Be cautious of links that redirect to unknown third-party websites. Such links are often indicative of fraudulent activity.
- Interrupt URL resolutions that involve newly registered domains, by applying blocklists at the browser or DNS level. Infoblox offers several intelligence feeds that are based on newly observed domains.2
- Be very cautious when filling out web forms with personal details. Ensure that the website is legitimate and uses authentic payment services.
4. Indicators of compromise
The Infoblox Threat Intelligence Group (TIG) has been sharing indicators of compromise (IOCs) related to the Russian invasion of Ukraine, including the campaigns mentioned in this report. For a comprehensive list of our IOCs on this topic, see the GitHub repository infobloxopen:threat-intelligence.3 We derived the IOCs below from our analysis of the campaigns mentioned in this report.
| Indicator | Description |
| 107[.]179[.]97[.]14
107[.]179[.]97[.]25 134[.]73[.]31[.]107 134[.]73[.]31[.]118 134[.]73[.]31[.]123 134[.]73[.]31[.]98 134[.]73[.]31[.]99 192[.]3[.]26[.]39 93[.]99[.]106[.]220 |
SMTP IP addresses used to send gift card spam |
| AmazingDeals[@]dripwatt[.]co
AmazingDeals[@]govauctionz[.]co AmazonOpinionRequested[@]costcoproof[.]co AmazonShopperGiftCardChance[@]costcoproof[.]co AmazonShopperGiftOpportunity[@]costcoproof[.]co CustomerFeedback[@]dripwatt[.]co CustomerFeedback[@]govauctionz[.]co EbayOpinionRequested[@]legendpotencyx[.]co HomeDepotShopperFeedback[@]manifestub[.]co KohlsShopperFeedback[@]dripwatt[.]co KohlsShopperGiftCardChance[@]dripwatt[.]co KohlsShopperGiftCardChance[@]govauctionz[.]co ThankYouHomeDepot[@]manifestub[.]co UkraineCrisisShopperGiftCardChance[@]unlockguts[.]biz UkraineCrisisShopperGiftCardChance[@]wellbuddie[.]co UkraineCrisisShopperGiftOpportunity[@]unlockguts[.]biz YouTubeOpinionRequested[@]purelean[.]biz YouTubeShopperFeedback[@]purelean[.]biz YouTubeShopperGiftOpportunity[@]purelean[.]biz |
From email addresses observed in the gift card spam |
| Amazing Deals
Amazon Shopper Gift Card Chance Amazon Shopper Gift Opportunity Customer Feedback Ebay Opinion Requested Gas Prices Shopper Feedback Gas Prices Shopper Gift Card Chance Gas Prices Shopper Gift Opportunity Home Depot Shopper Feedback Kohl’s Shopper Feedback Kohl’s Shopper Gift Card Chance Thank You Home Depot Ukraine Crisis Shopper Feedback Ukraine Crisis Shopper Gift Card Chance Ukraine Crisis Shopper Gift Opportunity YouTube Opinion Requested YouTube Shopper Feedback YouTube Shopper Gift Opportunity |
From name observed in the gift card spam |
| !BONUS: $100 INFLATION Gift Card Opportunity
BONUS: $50 KOHL’S Gift Card Opportunity “Shopper, You can qualify to get a $50 YouTube gift card!” Congratulations! You can get a $50 Kohl’s gift card! “Shopper, You can qualify to get a $100 Ukraine Crisis gift card!” Congratulations! You can get a $100 Ukraine Crisis gift card! Congratulations! You can get a $50 Ebay gift card! FW: Congratulations! You can get a $50 Kohl’s gift card! FW: BONUS: $50 KOHL’S Gift Card Opportunity “Shopper, You can qualify to get a $50 Amazon gift card!” Congratulations! You can get a $50 YouTube gift card! FW: [[ You have won an $5OO WalMart Gift Card ]] BONUS: $50 AMAZON Gift Card Opportunity “Shopper, You can qualify to get a $100 Inflation gift card!” FW: … Consumer News: Get a $1000 Sam’s Club Gift Card!… Congratulations! You can get a $50 Amazon gift card! Congratulations! You can get a $100 Home Depot gift card! FW: Verification – Lowe***s Gift Card #8280 Congratulations! You can get a $100 Inflation gift card BONUS: $50 YOUTUBE Gift Card Opportunity |
Subject line used in the gift card spam |
| unlockguts[.]biz
kidneydoctor[.]icu manifestub[.]co costcoproof[.]co legendpotencyx[.]co dripwatt[.]co purelean[.]biz govauctionz[.]co |
Domains used in the gift card scam |
| shopingmaster[.]com
shopperlobby[.]com dailyneedstock[.]com |
Domains for the landing pages used in the gift card scam |
| http://costcoproof[.]co/1aDPbfgFSOj73STBULx5uq8CGVZMnri86NRC8HS1LlWuArRJUA
http://dripwatt[.]co/-ggAzODKygRRvqS3OSLgFJw1gdpV7iwgETG9gym3jm8CPHI http://govauctionz[.]co/_6qXK6kPeBa5QeGwJwtGIAbI0tJWtfXOvUJ7BwTH3JRZLopF http://kidneydoctor[.]icu/2qqbpgaX2eA3NT1otelIFjJQvXP6IKUXysJwPnpULbjr2JYg http://legendpotencyx[.]co/2Yoastq66ZaZUckjjTiDU_a2SR26Bffl4nx78-SqvfzY0lwf http://manifestub[.]co/8firg6h4gt4vh5bpg0QK-sZ5rQSuQEd1K5xWGma-xhOFZhY http://purelean[.]biz/-lvavAZ7LHYA_9crmQrhHEifmP-NjQkKpdpI_GJb4Bj1cj3jUw http://www[.]unlockguts[.]biz/7391-9-3599-110581614/alexa/tindex8[.]html |
Links used in the gift card scam |
| 65[.]108[.]10[.]44
41[.]113[.]206[.]62 41[.]113[.]137[.]189 |
SMTP IP addresses used to send the 419 spam |
| markgrantcharity33322@gmail[.]com
markgrantcharity3322@outlook[.]com helpukraine@manavadhikarprotection[.]com ukraine@manavadhikarprotection[.]org |
Reply-to email addresses used in the 419 scam |
| manavadhikarprotection[.]com
manavadhikarprotection[.]org |
Compromised domains used in the 419 scam |
| giveaidint[.]org
giveukraineaid[.]org taewong[.]com taewong[.]giveaidint[.]org |
Domains used in the donation scam |
5. Appendix
A. An example of a message sent in the gift card spam
| Shopper, You can qualify to get a $100 Ukraine Crisis gift card!
hxxp://kidneydoctor[.]icu/M2mD3cR57JGrA3aJwA0wtCp9DMAYGJrFlFE-7qXOgzdRhMc hxxp://kidneydoctor[.]icu/1tD6mHS8MGxhYJSwf9-jy0yt0uFDNczTrad-gdVlf8NFr_t5 he Progressive Era (1896–1916) was a period of widespread social activism and political reform across the United States of America that spanned the 1890s to World War I. The main objectives of the Progressive movement were addressing problems caused by industrialization, urbanization, immigration, and political corruption. Social reformers were primarily middle-class citizens who targeted political machines and their bosses. By taking down these corrupt representatives in office, a further means of direct democracy would be established. They also sought regulation of monopolies through methods such as trustbusting and corporations through antitrust laws, which were seen as a way to promote equal competition for the advantage of legitimate competitors. They also advocated for new government roles and regulations, and new agencies to carry out those roles, such as the FDA. Many progressives supported prohibition of |
B. An example of a Dutch-language message used in the 419 scam
| Geachte heer, Al mijn pogingen om u telefonisch te bereiken tot in detail uit te leggen zijn niet gelukt.Ik vond het verstandig om deze e-mail te sturen. Ik ben mevrouw Bohdana Boguslaw de vrouwte laat? Andriy Boguslaw uit Kiev, Oekraпne, die eergisteren door Russische soldaten is gedood. Jr. Hij onthult ons dat hij 16 miljoen euro contant geld in een veilige kluis heeft hij van plan was te investeren. Hij gaf ons de opdracht om in uw land op zoek te gaan naar een betrouwbare persoon die ons met eerlijk advies en zekerheid kan helpen om het geld in zijn land te investeren in een investeringen die inkomsten kunnen opleveren. helpen het geld te ontvangen dat het bij banken in Europa deponeert, zal nemen, zodat de persoon kan ons helpen het geld op zijn rekening veilig te stellen en het voor ons te beleggen met volledig vertrouwen, eerlijkheid en geheim. vernietigd/gesloten. Ik heb met de vrachtmeester van de Verenigde Naties besproken dat hij ermee instemt ons te helpen onze bezittingen uit Oekraпne naar een veilige locatie te brengen. Ons leven is in groot gevaar, veel mensen zijn omgekomen door aanhoudende Russische beschietingen en bommen. Russen gebruiken luchtbombimgs / stakingen om te doden onschuldige burgers waarvan als we niet snel vertrekken, we alles zullen verliezen, inclusief ons leven. vele massa mensen miljoenen willen verhuizen met continue air trike en bomaanslagen. De diplomaat van de Verenigde Naties adviseerde ons om onze rijkdom in vertrouwde handen te geven en vervolgens te plannen hoe we met mijn kinderen zouden verhuizen. Want als we dat niet doen? de Russen naderen snel en zullen het geld aannemen als ze het zien. Begrijp alstublieft onze situaties en help. We moeten van deze gelegenheid gebruik maken, iedereen verplaatst zijn bezittingen massaal uit Oekraпne en ook de fondsen. De diplomaat is een eerlijke, Eprience en vertrouwde persoon, hij kan ons helpen het geld in een doos te verbergen zonder dat iemand het weet. helpukraine@manavadhikarprotection[.]com Gebruik bij het beantwoorden het onderwerp: Let op: mevrouw Bohdana Boguslaw Mevrouw Bohdana Boguslaw |
C. An example of a short English-language message used in the 419 scam
| Halifax bank PLC on behalf of UNICEF have released the Charity cash transfer of 76,000,000$ to assist the less privilege and Ukraine refugees that have escaped as a result of the Russian Invasion for a 30% compensation. Indicate if you are interested in handling this reputable charity project by providing your Identity & details to this email to commence this project. Mark Mark Email:markgrantcharity3322[@]outlook[.]com Tel:+1(201) 644 6843 |
Endnotes
- https://blogs.infoblox.com/cyber-threat-intelligence/cyber-threat-advisory/cyber-threat-advisory-ukrainian- support-fraud/
- https://blogs.infoblox.com/security/newly-observed-domains/
- https://github.com/infobloxopen/threat-intelligence









