Author: Nick Sundvall and Vadym Tymchenko
1. Executive summary
A new technique for bypassing mobile spam filters and distributing malicious content was recently observed in text messages received by a number of users. Where mobile phishing often includes a fake sender phone number, these malicious messages appear to come from the victims themselves. The messages include a link that, if clicked on, enables threat actors to steal victims’ information. We analyzed one campaign in depth and uncovered a large infrastructure and a complex pattern of redirection to overcome automated security filtering. Operations of this size require significant planning but allow the actors to profit even when only a small number of users fall victim to the lures.
In this report, we will step through a case study of a malicious text message, an analysis of the domain names, and an overview of the threat actor’s redirection infrastructure, including what we will refer to as the front-end domains, campaign broker domains, clickbait pages/domains, and final landing pages/domains.
2. Smishing Background
Smishing is the combination of the terms “phishing” and “SMS” (short message service, also known as text messages). Smishing messages are sent by bad actors to get victims to reveal private information, including passwords, identity, and financial data. The messages typically include some incentive for the recipient to click a link, which may be for a site that hosts malware or a page that attempts to convince the user to submit data through a form.
Actors have regularly used spoofed sender numbers in the text messages to evade spam filters. However, those messages that are not automatically detected by the mobile provider can be stopped by blocking the sender’s phone number. In response, threat actors continue to evolve their own techniques. In a well-known version of mobile phone spoofing, a recipient receives a text or phone call from someone who appears to be in the area close to the recipient. Users are hesitant to block local phone numbers for fear it would also block legitimate phone calls and messages.
Spoofing the recipient’s phone number is another advance by actors to overcome spam filtering and blocking, and to convince users to click on the embedded links.
3. Case Study
On March 29 and 30, we observed multiple smishing texts from one campaign, and we will analyze the details on one of the messages, as a case study, below. All of the messages we saw in this campaign began with the same content; the only part that changed was the URL. The text we will discuss is shown in Figure 1 below.
Figure 1. Case study message; the full URL is redacted because it may uniquely identify the recipient
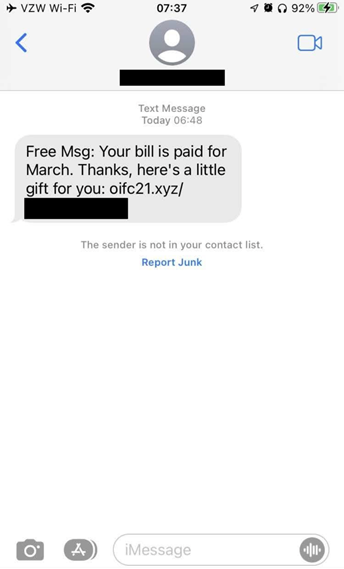
The link in Figure 1 above used the domain oifc21[.]xyz, but we saw a variety of domains used. We will call the domains in the text messages the “front-end domains”. We saw these domains use only the top-level domain (TLD) .xyz. When we clicked on the link, it did not lead us to oifc21[.]xyz; instead, multiple redirects occurred before a final landing page was presented. In this instance, we were redirected to goodasgold[.]shop, then takeoneforlove[.]com, and then eshatl[.]xyz, which presented a fake Verizon survey page. After completing the survey, a message appeared that thanked us “for being a great customer” and asked us to click the displayed button to claim a new Apple Watch.
Figure 2. Example of one of the faked survey questions
Fake Verizon survey
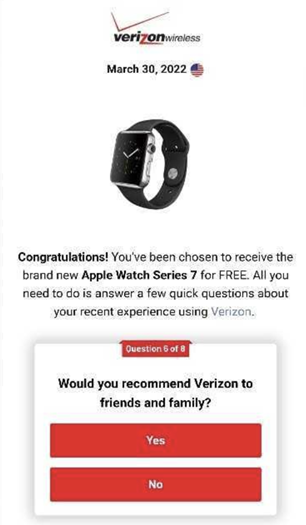
The threat actors tried to imbue their content with a sense of urgency; this is a common tactic used to pressure victims into complying with the scam. After we completed the survey, the webpage warned: “if you leave this page without claiming your reward, we have no choice but to give another loyal customer”. Clicking the button again redirected us to a new website, smartfashiondaily[.]com, where the actors asked us to pay $6.85 for “Shipping & Handling”. The actors also asked for our name, email address, phone number, mailing address, and credit card information.
Figure 3. Fake checkout page
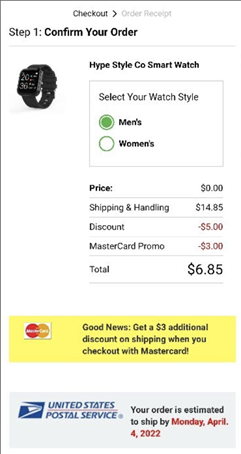
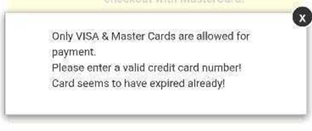
After providing the information, we were told that our credit card number was not valid.
Figure 4. The message shown after we submitted shipping and credit card details
4 Campaign Study
a. Campaigns
Our analysis shows that the same actor carried out at least two campaigns in March:
- The first took place between 6 and 8 March. We call it the CDC campaign because the requests that did not pass the actor’s validations were redirected to cdc[.]gov.
- The second took place between 26 and 31 March; it appears that the campaign may have stopped after less than a week, because no activity has been observed after March 31. We call it the 1TV campaign because the requests that did not pass the actor’s validations were redirected to 1tv[.]ru or 1tv[.]com.
Both campaigns share the same set of domain names registered on 6 March.
b. Domain Names
From several examples, we have noticed that the domains used in the SMS messages have a distinct pattern: four or five alphabetical characters followed by one or two digits, all in the TLD .xyz. This allowed us to create a simple regex and apply it to data for March and the start of April.
Figure 5. Domain creation and update activity

The activity histogram shows when the domains associated with this campaign were registered (“created”) and/or updated. All of the domains we believe to be associated with the campaign have the following characteristics:
- All the domains were registered between 5 and 10 March.
- Their names follow the regex pattern ^[a-z]{4,5}[0-9]{1,2}.xyz.
- The numeric components of their names use consecutive numbers.
- Their registrar is Hosting Concepts.
- They use CloudFlare for their name servers and hosting.
There were several groups of domains registered in March. Most of the domain names followed a pattern of 4 or 5 alphabetic characters followed by a sequential number within the group.
c. Observed Activity
Figure 6 below shows activity related to the domains associated with this campaign. We can see a small amount of activity from 5 to 8 March, and then a much greater spike between 26 and 31 March. This second, larger spike is associated with the smishing campaign that our case study above came from.
Figure 6. Observed activity from 1 March to 2 April

Figure 7. Sample of dates and smishing campaign URLs

5. Campaign Generalization
The structure and activity we observed in the two campaigns described in this paper match that of several older smishing campaigns that we have analyzed. The domains used in the redirect patterns all appear to share similar naming conventions and other properties. A deep study of both older and these more recent campaigns show that they have similar structures of redirect requests and groups of domains used for very specific purposes. The diagram below illustrates the flow of requests and redirects between domains in the infrastructure and the assumed functionality of each layer. We think this is a valid model of infrastructure that, with variations, is likely used by multiple threat actors.
Figure 8. Smishing campaigns’ redirection layers and activity
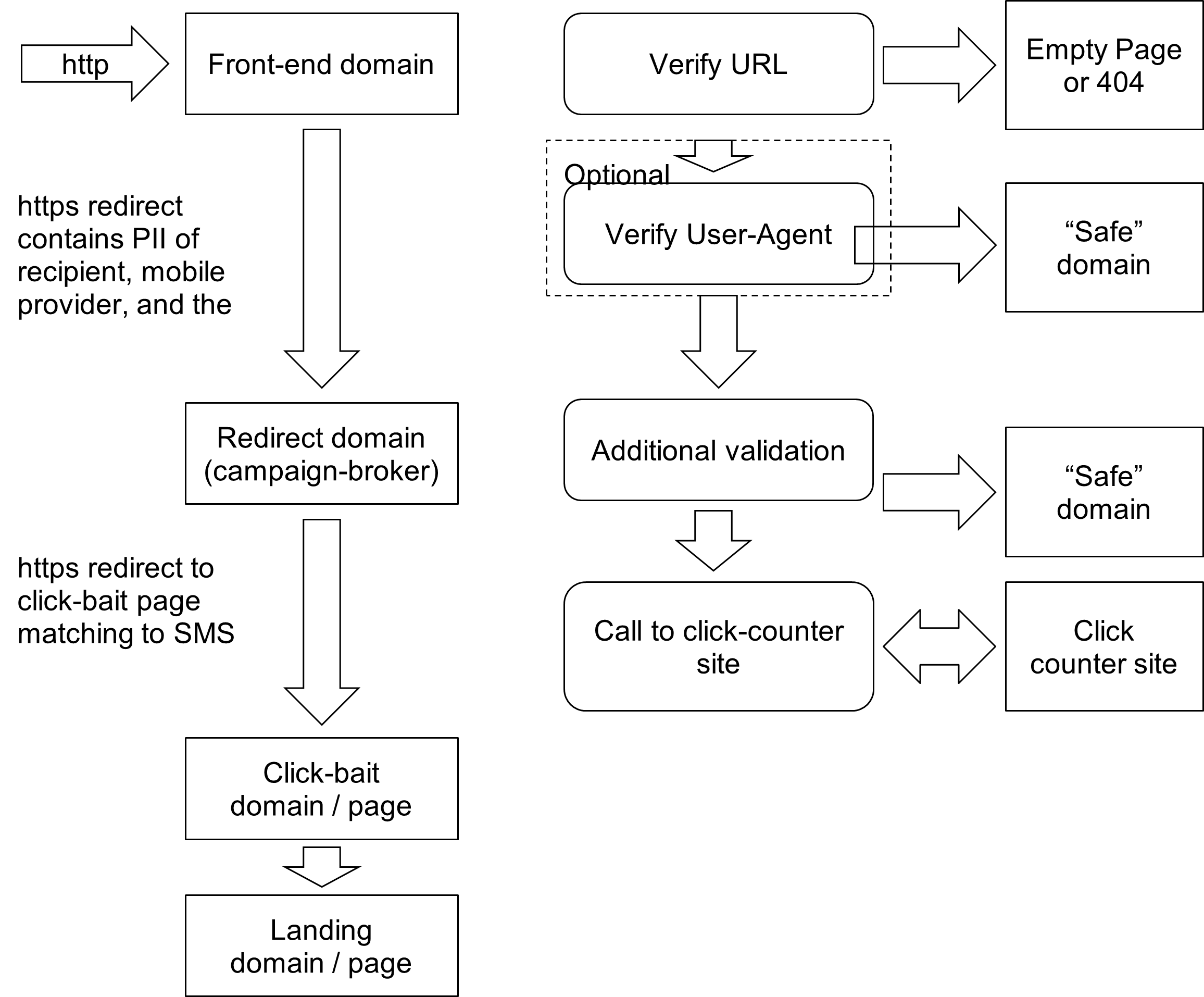
Analyzing the redirect structure showed that it consists of at least 4 layers, all with clearly identifiable purposes. Note that there are some minor differences between the 1TV and CDC campaigns, which we will identify below.
- Front-end URL:
- The domain in the smishing URL typically has a short lifespan because it is the most exposed component of the campaign and thus the most easily identified and blocked by security providers. In most of the previous campaigns, threat actors used the domain within a few hours after registering it. In the 1TV campaign, however, the front-end domains were “aged” for about two weeks before the threat actor put them to use. This aging approach allows the actor to bypass the security provider’s attempts to block threats based on newly registered domains.
- The URL provided in the SMS provides unique identification of the user. The front-end code seems to have very limited functionality checking if the request has not expired (we observed some links expiring in under 2 days). The link will not work with any other domain associated with the campaign, probably due to redirect conditions coded in the web server’s configuration.
- In most cases, the front-end URL is accessed by HTTP protocol. This is likely due to the throw-away nature of the front-end domains. Redirects from these domains to subsequent layers are always encrypted with HTTPS.
- In some cases, we observed the front-end domain perform additional validation of incoming requests, such as user-agent string comparison. If a user-agent string does not match the targeted device, it redirects to a “safe” domain, in our case 1tv[.]ru or 1tv[.]com.
- Redirect domain (campaign broker):
- This domain receives the HTTPS request redirected from the front-end domain. The request contains the victim identifier (in many cases the phone number), mobile provider, campaign name, and other information.
- The redirect domain verifies the user-agent header; if any mismatches are found, the domain redirects the victim to the “safe” domain.
- There may be several redirect domains in the chain.
- There is often a call to a click-tracking site, for statistics-collection purposes.
- After all the checks are successfully passed, the user is redirected to a clickbait page that matches the content of the SMS message.
- Threat actors typically keep their redirect domains active much longer than their front-end domains because users never see them. We have seen redirect domains live for over a year and serve several campaigns.
- Clickbait domain or page:
- Our understanding of the purpose of this layer is that it introduces an interaction point that prevents automated URL-tracing tools from reaching the final phishing site. We have seen several variations of this layer; typically, it is a button that when clicked, takes a user to a “survey” site. In other cases, it is a simple single-click page that takes the user directly to the final phishing page.
- In many cases, the clickbait domain is short-lived due to its relatively high visibility.
- Landing page (phishing site): this is the final phishing site that requests credit card information or other sensitive data.
6. Prevention and Mitigation
Smishing messages are a common method for sending phishing links. Infoblox recommends the following precautions for avoiding smishing attacks:
- Always be suspicious of unexpected text messages, especially those that appear to contain financial or delivery correspondences, documents, or links.
- Never click URLs in text messages from unknown sources. In the campaign under discussion, the source was the recipient, who did not send the message, and that is a red flag.
7. Conclusion
In this campaign, threat actors sent spam SMS messages to Verizon Wireless customers. The messages contained malicious links and appeared to have come from the recipients themselves. The links led to fake survey pages where the victims were asked to submit their personal and financial information, which ended up in the hands of the threat actors.
The actors redirected victims through a series of domains to avoid analysis and detection. We have observed multiple campaigns that used this kind of technique in the past; it makes it particularly challenging for researchers to analyze the malicious URLs. Our analysis of the URL data enabled us to discover additional domains used by the actors.
8. Indicators of compromise
For a downloadable list of our IOCs on this topic, see the cta_indicators folder of our GitHub repository infobloxopen:threat-intelligence.
| Indicator | Registration Date | Properties | Description |
| smsw1[.]xyz
mfso1[.]xyz pely2[.]xyz wtwx2[.]xyz khed3[.]xyz mgdi3[.]xyz laea4[.]xyz omyq4[.]xyz qyef5[.]xyz idvk5[.]xyz dqvy6[.]xyz dnmc6[.]xyz igtf7[.]xyz kiwv7[.]xyz jjao8[.]xyz kvde8[.]xyz okil9[.]xyz harn9[.]xyz nill10[.]xyz ulht10[.]xyz nijf11[.]xyz qgjt11[.]xyz hcip12[.]xyz jcal12[.]xyz rezb13[.]xyz tslz13[.]xyz hlns14[.]xyz izhm14[.]xyz bgfv15[.]xyz jbeq15[.]xyz mbdq16[.]xyz acgv16[.]xyz nkeh17[.]xyz wzae17[.]xyz rtpe18[.]xyz yhan18[.]xyz yamn19[.]xyz sjwf19[.]xyz zdip20[.]xyz culs20[.]xyz ezks21[.]xyz ysfz21[.]xyz cmrc22[.]xyz vuau22[.]xyz jqiz23[.]xyz hadq23[.]xyz ixyv24[.]xyz lhkp24[.]xyz hpfd25[.]xyz vjhk25[.]xyz uyqb26[.]xyz chkn26[.]xyz aust27[.]xyz ltsg27[.]xyz lcsh28[.]xyz aqfo28[.]xyz erae29[.]xyz mgjg29[.]xyz ithn30[.]xyz qinh30[.]xyz mszp31[.]xyz pomz31[.]xyz ciww32[.]xyz nooa32[.]xyz mvfe33[.]xyz zmtt33[.]xyz jzwc34[.]xyz ktfu34[.]xyz opdb35[.]xyz rrhn35[.]xyz gptp36[.]xyz dtus36[.]xyz qjag37[.]xyz swbt37[.]xyz upah38[.]xyz ixbc38[.]xyz qfac39[.]xyz xifj39[.]xyz aped40[.]xyz jaig40[.]xyz ckex41[.]xyz wgrp41[.]xyz hegz42[.]xyz ciuu42[.]xyz lawn43[.]xyz zoqw43[.]xyz zcyj44[.]xyz qbas44[.]xyz usha45[.]xyz zvlg45[.]xyz zlxg46[.]xyz qhrq46[.]xyz fuir47[.]xyz ixsf47[.]xyz vtpf48[.]xyz ejia48[.]xyz pvut49[.]xyz sgqz49[.]xyz glju50[.]xyz zmxu50[.]xyz |
5 March 2022 | 100 domains
Registrar: Hosting Concepts
NS: *.ns.cloudflare.com
Pattern: ^[a-z]{4}[0-9]{1,2}.xyz
Numeric part: Sequence of numbers from 1 through 50, each number used twice |
Front-end domains from SMS
It was observed in two campaigns: a small CDC-associated campaign on 2022-03-06, and one large 1TV campaign on 2022-03-26 |
| hggq1[.]xyz
wkcq2[.]xyz vfar3[.]xyz svgd4[.]xyz fgoy5[.]xyz gvhj6[.]xyz bepf7[.]xyz vkri8[.]xyz eknz9[.]xyz mslx10[.]xyz dfys11[.]xyz djzy12[.]xyz gytr13[.]xyz qhdd14[.]xyz sbqs15[.]xyz pmlx16[.]xyz iphk17[.]xyz opqk18[.]xyz ntfr19[.]xyz cvwm20[.]xyz |
6 March 2022 | 20 domains
Registrar: Hosting Concepts
NS: *.ns.cloudflare.com
Pattern: ^[a-z]{4}[0-9]{1,2}.xyz
Numeric part: Sequence of numbers from 1 through 20 |
Front-end domains from SMS
Observed in the 1TV campaign on 2022-03-26 |
| wtmz1[.]xyz
xwjv1[.]xyz nyxk2[.]xyz pwnx2[.]xyz dbmy3[.]xyz nvso4[.]xyz vooy4[.]xyz hzkr5[.]xyz* gddr6[.]xyz hhjx7[.]xyz shcw7[.]xyz oxwe8[.]xyz rpws8[.]xyz aqsz9[.]xyz ijph9[.]xyz sqyc10[.]xyz wszd10[.]xyz cegs11[.]xyz odkp11[.]xyz gshu12[.]xyz tfll12[.]xyz dysj13[.]xyz tbsb13[.]xyz ccpt14[.]xyz oyfn14[.]xyz fgvz15[.]xyz hquu15[.]xyz jenh16[.]xyz nrfe16[.]xyz fjow17[.]xyz flgk17[.]xyz anwa18[.]xyz dtxp18[.]xyz inen19[.]xyz ozhn19[.]xyz avyc20[.]xyz oifc21[.]xyz* ukuu21[.]xyz dcdh22[.]xyz htur22[.]xyz ohmv23[.]xyz qflr24[.]xyz xnrh24[.]xyz snqu25[.]xyz hklk26[.]xyz vqsr26[.]xyz ahct27[.]xyz umlp27[.]xyz kdvi28[.]xyz xuuv28[.]xyz lefx29[.]xyz atsk30[.]xyz vflu31[.]xyz zhnv32[.]xyz xdhh33[.]xyz refp34[.]xyz rczt35[.]xyz gxkk36[.]xyz gmec37[.]xyz ahur38[.]xyz asqb39[.]xyz bjas40[.]xyz jnmj41[.]xyz mfis42[.]xyz tyer43[.]xyz spmu44[.]xyz bxqi45[.]xyz islf46[.]xyz gjdl47[.]xyz ztib48[.]xyz ytqk49[.]xyz cepf50[.]xyz kcap51[.]xyz dfeo52[.]xyz lcrn53[.]xyz tgav54[.]xyz sctn56[.]xyz cfzb57[.]xyz lpdl60[.]xyz bikm61[.]xyz doif62[.]xyz ovel63[.]xyz bkhr64[.]xyz vhjp65[.]xyz guxv66[.]xyz qgud67[.]xyz ngkl68[.]xyz wfug69[.]xyz rhlw70[.]xyz |
8 March 2022 | 89 domains
Registrar: Hosting Concepts
NS: *.ns.cloudflare.com
Pattern: ^[a-z]{4}[0-9]{1,2}.xyz
Numeric part: Sequence of numbers from 1 through 70, with a few gaps. Some numbers from 1 through 28 were reused twice. |
Front-end domains from SMS
Observed in the 1TV campaign on 2022-03-26 |
| eaiys1[.]xyz
upxut2[.]xyz obkom3[.]xyz bsqnt4[.]xyz rninf5[.]xyz lrcoq6[.]xyz hacpg7[.]xyz dfooh8[.]xyz slsvv9[.]xyz eiwku10[.]xyz tuafv11[.]xyz pvtcb12[.]xyz aekse13[.]xyz sbbwr14[.]xyz iiddf15[.]xyz nqldt16[.]xyz ceewi17[.]xyz uzzau18[.]xyz vnaeg19[.]xyz bpdmk20[.]xyz dyzhu21[.]xyz yhqxk22[.]xyz ebtxe23[.]xyz lutod24[.]xyz fxzzc25[.]xyz rjebg26[.]xyz ibjme27[.]xyz svjem28[.]xyz jbbsg29[.]xyz qodmu30[.]xyz yyaad31[.]xyz plzjc32[.]xyz velfu33[.]xyz* kxyps34[.]xyz cnwfz35[.]xyz zhgsb36[.]xyz bypmz37[.]xyz xnqno38[.]xyz ccpxd39[.]xyz qsbhi40[.]xyz qhacw41[.]xyz iwbxe42[.]xyz snqwr43[.]xyz gxrgf44[.]xyz jfbku45[.]xyz einsj46[.]xyz* sirdt47[.]xyz gcfed48[.]xyz* hnxxd49[.]xyz jpjhz50[.]xyz |
8 March 2022 | 50 domains
Registrar: Hosting Concepts
NS: *.ns.cloudflare.com
Pattern: ^[a-z]{5}[0-9]{1,2}.xyz
Numeric part: Sequence of numbers from 1 through 50 |
Front-end domain from SMS
Observed in the 1TV campaign on 26 March |
| pycrm2[.]xyz | 10 March 2022 | Single domain matching common pattern
Registrar: Hosting Concepts NS: *.ns.cloudflare.com Pattern: ^[a-z]{5}[0-9]{1,2}.xyz Numeric pattern: only number 2 |
Front-end domain from SMS |
| easyechoes[.]com
|
18 February 2022
|
Registrar:Hosting Concepts
NS: ns1.openprovider.nl NS: ns2.openprovider.be NS: ns3.openprovider.eu |
Middle-layer domain (campaign-broker / redirector) |
| flagshipsteak[.]com | 5 March 2022 | Registrar:Hosting Concepts
NS: ns1.openprovider.nl NS: ns2.openprovider.be NS: ns3.openprovider.eu |
Middle-layer domain (campaign-broker / redirector) |
| glittersisgold[.]com
|
26 March 2022
|
Registrar:Hosting Concepts
NS: ns1.openprovider.nl NS: ns2.openprovider.be NS: ns3.openprovider.eu |
Middle-layer domain (campaign-broker / redirector) |
| goodasgold[.]shop | 29 January 2022 | Registrar: NAMECHEAP INC
NS: dns1.registrar-servers.com NS: dns2.registrar-servers.com |
Middle-layer domain (campaign-broker / redirector) |
| takeoneforlove[.]com | 11 March 2022 | Registrar: Hosting Concepts
NS: pam.ns.cloudflare.com NS: patrick.ns.cloudflare.com |
Middle-layer domain (campaign-broker / redirector) |
| u30487[.]xyz | 28 February 2022 | Registrar: Hosting Concepts
NS: linda.ns.cloudflare.com NS: rocky.ns.cloudflare.com |
Landing domain (clickbait page) |
| eshatl[.]xyz
|
28 February 2022 | Registrar: Hosting Concepts
NS: linda.ns.cloudflare.com NS: rocky.ns.cloudflare.com |
Final landing domain |
| smartfashiondaily[.]com | 17 September 2021 | Registrar: NAMECHEAP INC
NS: arnold.ns.cloudflare.com NS: maeve.ns.cloudflare.com |
Final landing domain |
* domains observed in malicious SMS











