Author: Nick Sundvall
TLP: WHITE
Overview
On 23 May, we observed a malspam campaign distributing a ZIP file containing Remcos, a remote access trojan (RAT) designed to remotely control a victim’s computer. The campaign’s email subjects attempted to gain the victim’s trust by impersonating a legitimate United Arab Emirates company called Al Salehi Machinery & Equipment Repairing.
We have previously reported on various Remcos campaigns, including one distributing the malware via malicious RTF files in 2019 and another via malicious XLS files in 2020.[1],[2]
Customer Impact
A German company called Breaking Security has been offering Remcos for sale online since 2016.[3] There is currently a free version available with limited features, as well as a paid version starting at 58 Euros. While it is marketed as a legitimate remote administration tool, it is frequently abused by threat actors and used for malicious purposes.
Breaking Security actively maintains and updates Remcos. Its capabilities include remotely controlling infected computers, logging keystrokes, taking screenshots and more.
Campaign Analysis
The threat actor behind this campaign used the email subject RE: Stanadyne Enquiry, imitating a conversation between Al Salehi Machinery & Equipment Repairing and Stanadyne, a fuel pump manufacturer. The emails included links to a legitimate website for Al Salehi, as well as their Facebook and LinkedIn pages. The sender’s address, purchase@alsalehi[.]ae, also adds legitimacy to the emails.
Attached to the emails is a ZIP file named Al Salehi Machinery & Equipment Repairing Enquiry.zip, containing the malicious Remcos executable Al Salehi Machinery & Equipment Repairing Enquiry.exe.
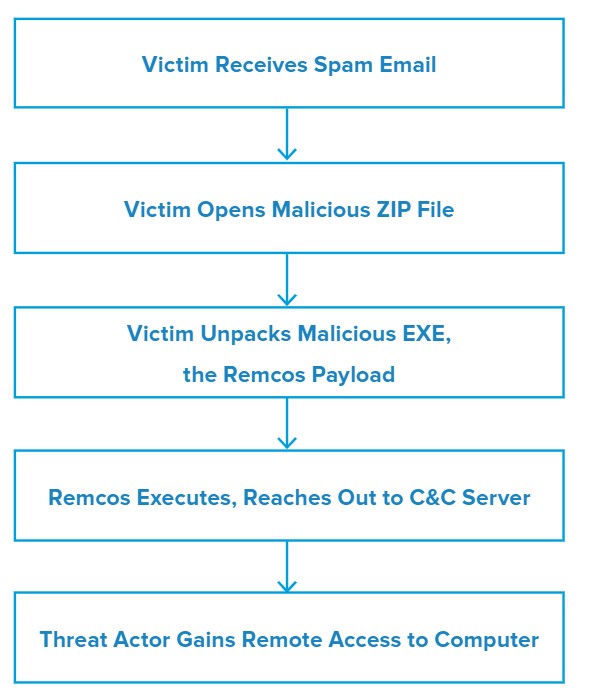
Attack Chain
Upon opening the attached ZIP file, the victim is able to extract the malicious EXE – Al Salehi Machinery & Equipment Repairing Enquiry.exe – from the archive. Running the EXE initiates the Remcos RAT.
From here, Remcos reaches out to Google and Bing before finally contacting its command and control (C&C) server. The threat actor then gains remote control of the computer and is able to run additional commands and send new payloads.
Vulnerabilities & Mitigation
Malspam email campaigns are a common distribution method for phishing scams. Infoblox therefore recommends the following precautions to avoid phishing attacks:
- Scan downloaded files with antivirus software.
- Verify important or potentially legitimate attachments with the sender via alternative means (e.g. by phone or in person) before opening them.
- Be aware of any attachment’s file type, and never open files that could be a script (.vbs, .cmd, .bat), an internet shortcut file, or compression file. Using the latter is a known method for evading detection methods based on file hashes and signatures. Threat actors use them to mask the real malicious file due to email service restrictions on attachment file types.
- Always be suspicious of vague or empty emails, especially if there is a prompt to open an attachment or click on a link.
- Do not open attachments that are unexpected or from unfamiliar senders.
Endnotes
- https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–32
- https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–94
- https://any.run/malware-trends/remcos








