Author: Christopher Kim
1. Overview
On 1 and 2 September, Infoblox observed a malicious email campaign distributing the trojan downloader GuLoader. The malware downloaded and executed the remote access trojan (RAT) Remcos. Although this campaign used GuLoader to deliver Remcos, other campaigns have used GuLoader to drop other kinds of RATs, such as NanoCore.1
2. Customer impact
Security researchers first discovered GuLoader in December 2019. The malware, written in Visual Basic 6.0, is primarily used to download RATs and information stealers.2
As a typical RAT, Remcos can steal information by capturing keystrokes, taking screenshots, checking browser cache and settings, and searching for files that contain passwords.3
3. Campaign analysis
All emails had the From name Lulama Mbanjwa, and email subject CV/Accountant. Embedded in the emails was a malicious Office Open XML spreadsheet, Retha F. Fourie CV.xlsx, which posed as a purchase-order form and was written in Chinese.
4. Attack chain
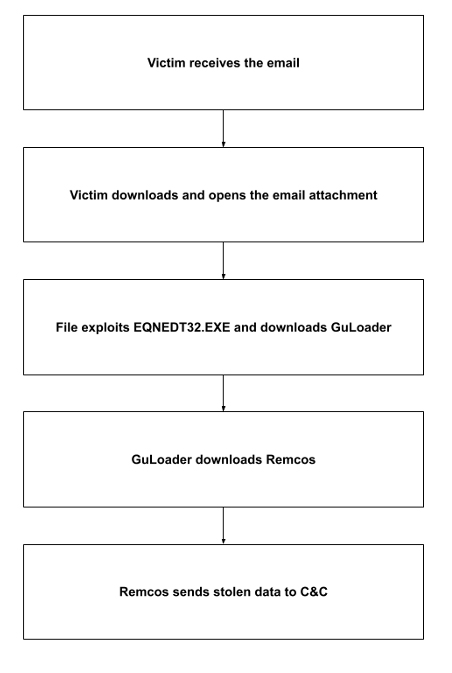
When the victim downloads the email attachment and opens the file, the malware exploits CVE-2017-11882; this stack-based buffer overflow vulnerability in Microsoft Office Equation Editor (EQNEDT32.EXE) allows threat actors to remotely execute code on a vulnerable system. If the exploit succeeds, EQNEDT32.EXE downloads and executes the GuLoader payload XNJ.exe.
GuLoader then attempts to evade debugging and malware analysis by detecting sandboxes and dynamic analysis tools, hiding threads from debuggers, and using other techniques; if successful, it downloads the Remcos payload and executes it.
Remcos connects to its command and control (C&C) server every five minutes, giving the actors persistent access to the infected machine and the ability to steal system information.
5. Vulnerabilities and mitigation
A GuLoader infection can compromise an organization’s data integrity and cause financial losses. We recommend that organizations take the following actions to strengthen their cyber defenses against the kinds of attacks described in this report:
- Be cautious of unexpected or suspicious emails that request action from recipients.
- Implement strong email security solutions capable of analyzing file attachments for malicious activities.
- Quarantine emails that security software has flagged as malicious.
- Monitor for internet connections sourced from unexpected applications.
- Detect computer processes that are not allow-listed and that generate outbound requests at consistent intervals. Presence of such processes might be indicative of C&C communications.
Endnotes
- https://blogs.infoblox.com/cyber-threat-intelligence/guloader-drops-nanocore/
- https://www.proofpoint.com/us/threat-insight/post/guloader-popular-new-vb6-downloader-abuses-cloud- services
- https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–94