In today’s interconnected enterprise environments, the stability and security of network services and infrastructure directly impact business continuity and resilience. Among the most critical yet often overlooked components of the network are Domain Name System (DNS) and Dynamic Host Configuration Protocol (DHCP) services. These services form the foundation upon which virtually all digital operations depend. Many organizations default to using the DNS and DHCP services bundled with Microsoft Active Directory, because of the convenience and perceived ease of deployment during domain controller setup. However, this architecture warrants reconsideration in light of evolving threat landscapes and increasing operational demands.
The True Criticality of DNS and DHCP
DNS (think of it as the GPS for computers to find websites and services) and DHCP (think automatic assignment of IP/network addresses to computers) aren’t merely background services—they are the mission-critical foundation of your entire digital infrastructure. Every enterprise application and security tool in your enterprise relies on DNS as its digital lifeline. Without DNS resolution, applications simply cannot communicate, rendering even the most sophisticated systems inoperable.
When DNS or DHCP fails, the consequences aren’t minor inconveniences—they’re potentially catastrophic events that can escalate to boardroom-level crises. In the most severe cases, complete DNS failure can halt operations across an organization: no transactions, no communications, no operations—everything freezes.
Given this level of criticality, the question becomes: are you architecting these services with the resilience they deserve?
The Hidden Risk: Cascading Failures
Despite the critical role, DNS and DHCP services are often deployed alongside identity services on the same servers—creating tightly coupled dependencies that can lead to dangerous cascading failures across the network. A recent ransomware event at a large healthcare organization illustrated this exact risk. First, the identity service was compromised, giving the attackers privileged access. Because DNS and DHCP were hosted on the same server as identity services, the organization simultaneously lost network access—bringing down core operations and severely complicating recovery efforts. Without these foundational services, even basic troubleshooting became impossible, dramatically amplifying the disruption and prolonging the outage.
Deploying DNS/DHCP and identity services on the same server is the digital equivalent of housing a power plant control room and a city’s emergency services dispatch center in the same building. When that building is attacked or compromised, you don’t just lose electricity—you lose the ability to coordinate a response.
The Hidden Costs of Using DNS/DHCP Bundled with Identity Services
Beyond catastrophic events, there are significant and often underestimated operational costs associated with running DNS and DHCP alongside identity services on the same infrastructure.
The experience of a global energy company with 62,000 employees and annual revenue of $349 billion in 2024 illustrates this point. The organization maintained 400 servers that supported both DNS/DHCP and identity services, all of which required monthly security and other patches—totaling 4,800 patches annually. They had at least a 1 percent failure rate during patch cycles, leading to 48 crashes per year. Assuming each crash disrupted about 50 employees for an average of four hours, and applying a modest cost of $100 per hour per employee, these routine disruptions cost nearly $1 million in annual productivity losses.
The impact wasn’t limited to downtime. The company also had 15 full-time system administrators focused solely on managing and maintaining DNS/DHCP on the combined infrastructure—resources that could have been redirected toward higher-value, strategic initiatives that drive innovation and competitive differentiation.
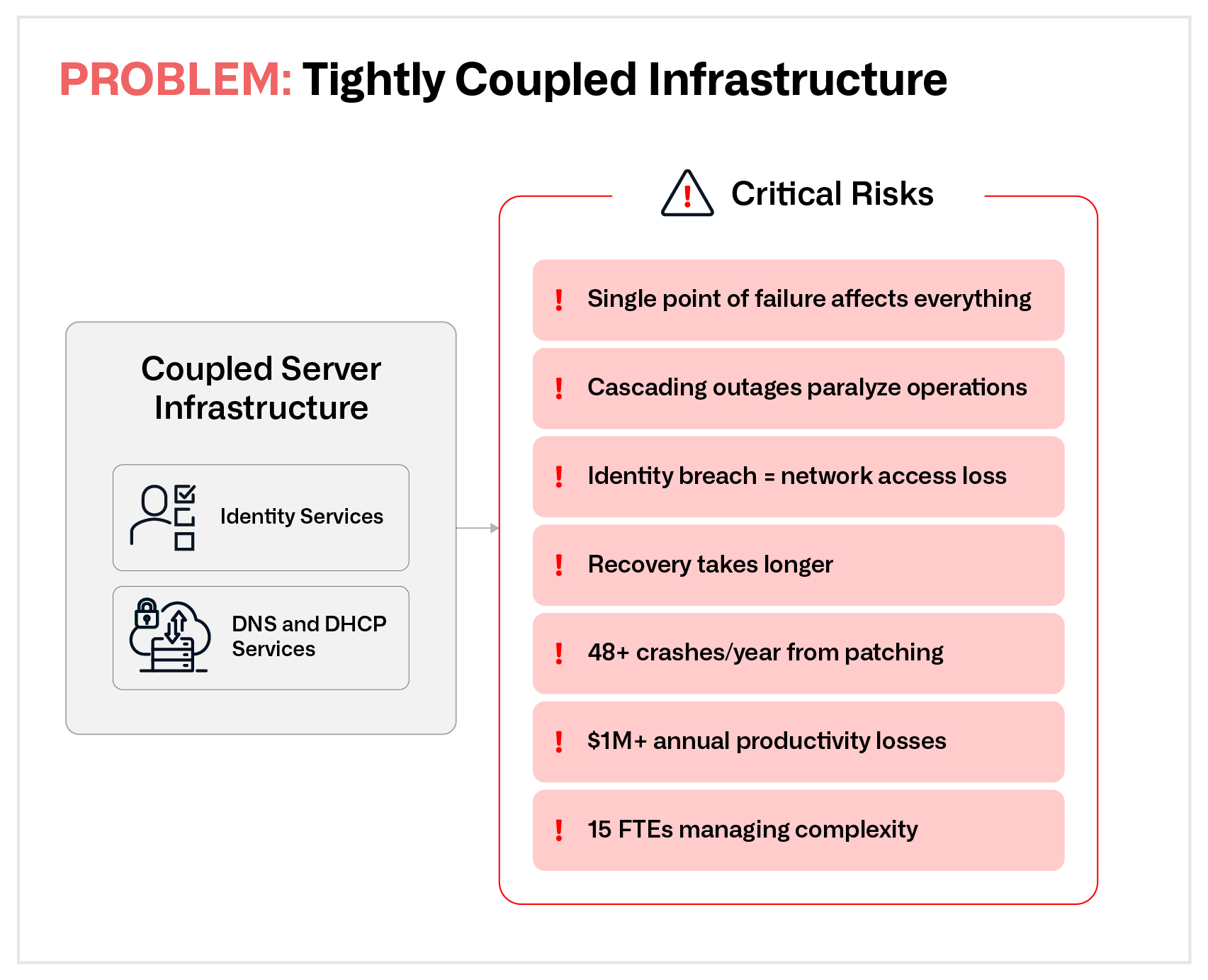
Figure 1. Tightly coupled infrastructure: When DNS/DHCP and identity services share the same servers, a single point of failure can cascade across your entire network, disrupting operations and complicating recovery efforts.
Security Implications: Beyond Operational Risk
Security concerns further reinforce the need to separate DNS and DHCP from identity infrastructure. Advanced persistent threats like Volt Typhoon—which target U.S. critical infrastructure including energy, water and telecommunications—frequently begin by compromising centralized identity systems. These attacks often follow a “live-off-the-land” approach that leverages existing tools to avoid detection.
Their strategic goal of such adversaries is to gather as much intelligence as possible—including credentials and DNS/DHCP data—to execute their operation. When identity services and network services are tightly coupled on the same platform, the attack surface expands significantly: compromising one system can provide access to both authentication controls and foundational network functions.
Separating these services, however, introduces a cleaner separation of responsibilities and enables adherence to the principle of least privilege. DNS and DHCP can function without elevated administrative rights, reducing the number of privileged accounts and limiting the potential impact of credential-based attacks. This architectural discipline is supported by recent draft updates to the National Institute of Standards and Technology (NIST) Special Publication 800-81, which emphasize the importance of separating mission-critical services to enhance cyber resiliency.
The Wake-Up Call: Critical Infrastructure Failures
In July 2024, the CrowdStrike incident served as a stark reminder of infrastructure dependencies. What began as a routine security update became the largest IT outage in history,1 crippling millions of servers that hosted identity services alongside DNS and DHCP functions. The widespread impact occurred because the affected servers were responsible for essential authentication and core network connectivity.
The cascading effects were unprecedented. Mission-critical applications were paralyzed across multiple sectors—over 10,000 flights grounded, hospital operations disrupted and emergency services compromised. This wasn’t just a technical glitch; it exposed the operational fragility of environments where DNS, DHCP and identity services are tightly coupled on the same infrastructure.
A Strategic Transformation: Learning from Leaders
A leading global SaaS provider with 72,000+ employees and nearly $38 billion revenue offers a compelling case study in infrastructure modernization. The organization faced a series of urgent challenges—including network outages when their identity and DNS services were impacted during the CrowdStrike incident, limited visibility across hybrid environments and a looming cloud migration deadline. To address these issues, they needed a more resilient and decoupled network architecture.
Their transition to the Infoblox Universal DDI platform delivered several key benefits:
- Established a clear path to a cloud-first infrastructure
- Gained unified visibility across hybrid environments
- Enhanced resilience and security by decoupling DNS from identity services
- Built a robust foundation for seamless multi-cloud operations
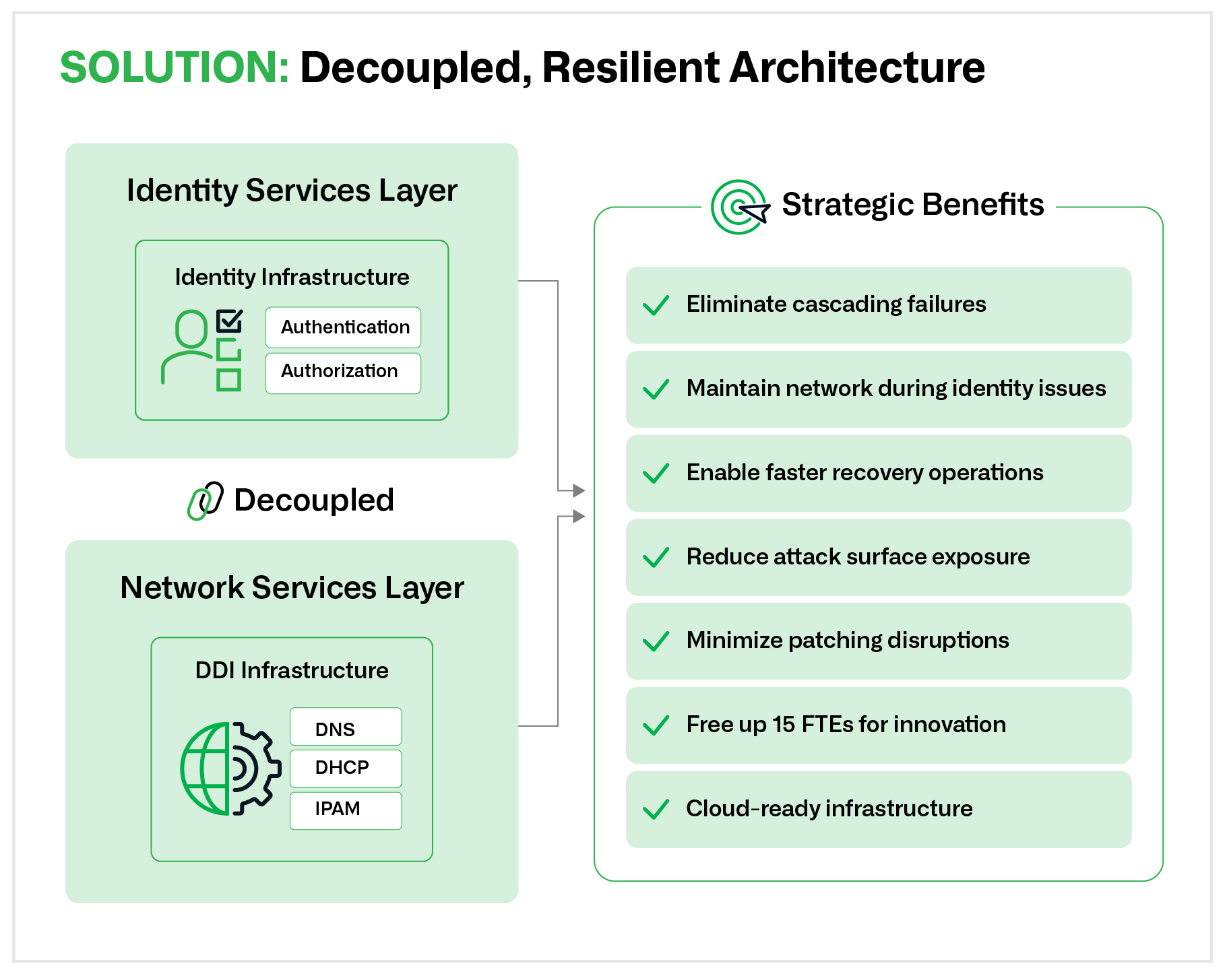
Figure 2. Decoupled architecture: Separating identity services from network services (DNS, DHCP, IPAM) eliminates cascading failures, enables faster recovery and provides the foundation for resilient, cloud-ready infrastructure.
Moving Forward: Three Steps to Resilient Infrastructure
To strengthen your DNS/DHCP architecture and improve operational resilience, consider these three key actions:
-
Decouple DNS/DHCP services from centralized identity systems
This architectural shift reduces cascading failure risks and allows you to retain flexibility in choosing identity providers. -
Educate your team on integrating DNS with external identity platforms
Misconceptions about decoupling can be addressed through internal training and planning. We’ve published a white paper to help teams understand these integration paths—available for download here. -
Explore enterprise-grade DDI (DNS, DHCP and IP address management) solutions
Purpose-built DDI platforms offer the operational maturity, scalability and security your critical infrastructure demands—especially in hybrid and multi-cloud environments. You can start by exploring Infoblox’s Universal DDI solutions here.
Strategic Imperative: Decoupling for Resilience and Security
DNS and DHCP are too essential to risk bundling them with other high-value systems. Decoupling these services from identity systems and deploying enterprise-grade DDI solutions are not just an IT best practice—it’s a strategic imperative for organizations aiming to strengthen uptime, security and agility.
As digital transformation accelerates and cyberthreats continue to evolve, your network architecture choices today will define your ability to operate securely tomorrow. Separating these foundational services from identity systems is a practical and proven step toward building infrastructure that’s ready for what’s next.
Footnotes
- CrowdStrike outage explained: What caused it and what’s next, Kerner, Sean, TechTarget, October 29, 2024.