Infoblox’s DNS Early Detection Program offers a unique approach to identifying potentially harmful domains. By utilizing our proprietary techniques, we can detect these domains early, giving defenders a significant advantage over threat actors. We flag these domains as suspicious at the earliest stage and make them available for immediate blocking. This proactive approach allows defenders to thwart attacks days, weeks, or even months before they appear in OSINT or threat intelligence feeds.
Threat actors continually adjust their techniques and very often use malicious domains to quickly launch damaging and dangerous attacks. Once that link to a malicious domain is clicked the Kill Chain can rapidly unfold to the detriment of the defenders. These malicious domains are often detected and shared too late by OSINT and threat intel feeds. Defenders need to be able to act faster to stop them.
Our DNS Early Detection Program not only identifies and analyzes potentially harmful domains but also cross-references our findings with data from public Open Source Intelligence (OSINT) and commercial threat intelligence feeds. In this blog post, we delve into our analysis of JinxLoader domains flagged as malicious in OSINT, providing numerous instances of our proactive identification of these domains as suspicious.
| Infoblox’s DNS Early Detection Program uses proprietary techniques to identify potentially malicious domains quickly. Infoblox flags these domains as suspicious so that your defenders can automatically block them. |
JinxLoader – A Malicious Malware Loader
JinxLoader is more bad news. JinxLoader, a malware loader recently introduced and written in the Go programming language, is currently being utilized by threat actors to deliver next-stage Kill Chain payloads including Formbook and XLoader.
Malware loaders always pose challenges for cybersecurity teams. A defense for one loader generally does not work for another, even when the loaded malware is the same. Loaders are often delivered via malicious phishing emails that offer socially engineered incentives such as relevant files, invoices, links, and even software updates. Identifying their Indicators of Compromise (IoCs) early in the Kill Chain can provide defenders with the advantage they need to confront and neutralize the threat.
In the case of recent JinxLoader activity, a barrage of attacks began, detected as phishing emails impersonating the Abu Dhabi National Oil Company (ADNOC). These emails requested recipients to open password-protected RAR archive attachments. Upon opening, these attachments dropped the JinxLoader executable. JinxLoader then serves as a gateway for Formbook or XLoader.
Analysis and Methodology
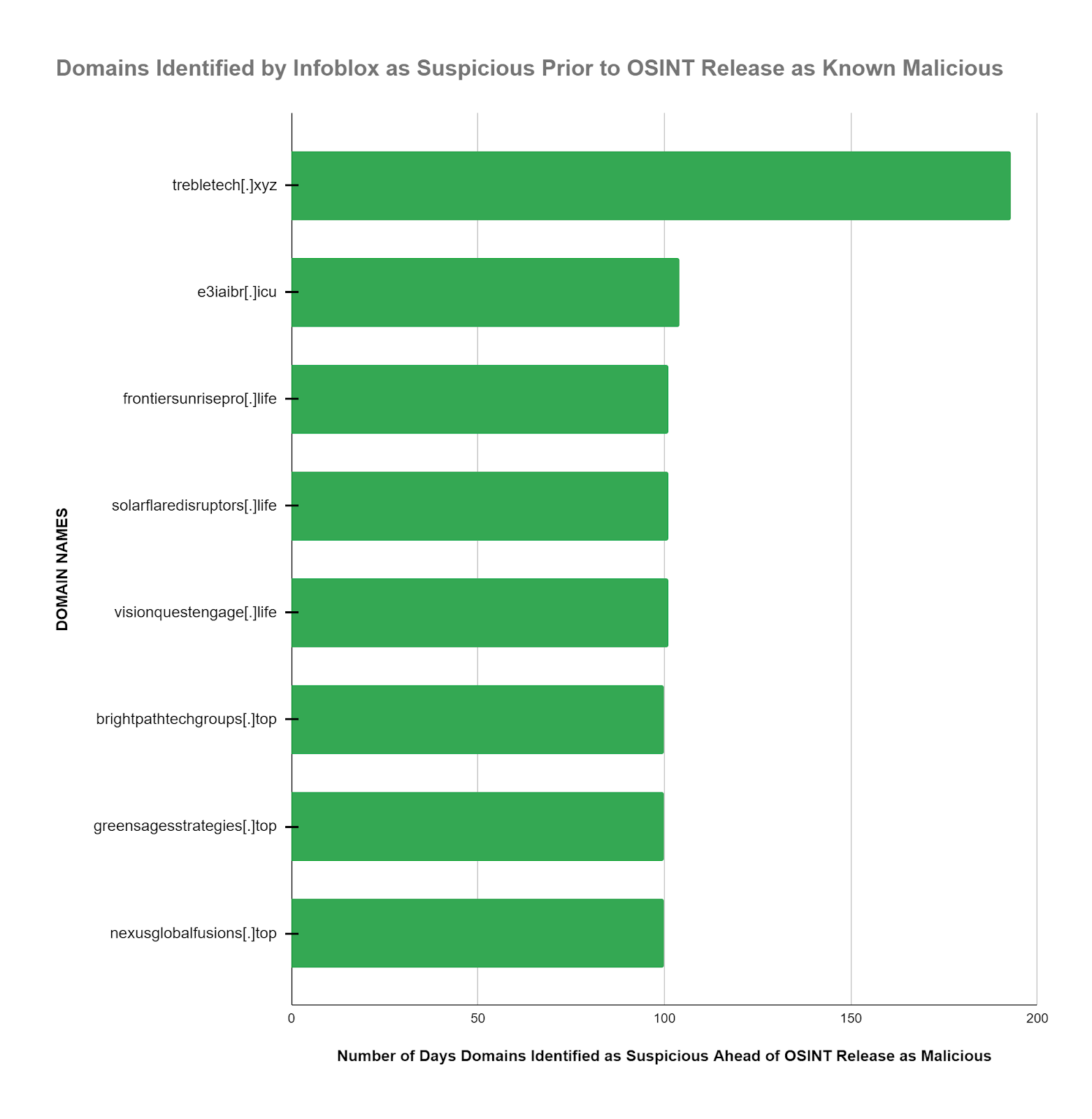
In a sponsored blog post published on February 12, 2024, the team at WhoisXML API identified several malicious domains derived from a DNS analysis of JinxLoader domains initially published in another vendor’s Open Source Intelligence (OSINT) in late November 2023.
These most recently identified malicious domains were then analyzed by the Infoblox team to determine if they were identified earlier by our suspicious domain feeds. Each malicious domain identified in OSINT was researched in the Infoblox Dossier Threat Research portal by our team. We reviewed our timeline feature to extract the earliest dates associated with Infoblox suspicious designation. We also extracted the WHOIS information for additional context.
| Infoblox identified 53.3% of the malicious domains as suspicious an average of 112.4 days earlier than OSINT availability. Similarly, Infoblox identified many of the malicious domains within 2 to 3 days of their WHOIS registration. This enabled our customers to stop the execution of the intended Cyber Kill Chain1 by automatically blocking access to these dangerous domains. |
The conclusions of our analysis illustrate the potential benefits of suspicious domain feeds:
- 53% of the domains were identified as suspicious by Infoblox an average of 112.4 days (3.7 months) prior to the availability of the OSINT designation as malicious.
- Our DNS early detection program identifies suspicious domains weeks to months, as in this case, ahead of OSINT identification as malicious.
- There is often an extended period of time from availability via OSINT to utilization by your cybersecurity ecosystem and defense-in-depth strategy. Infoblox designation of suspicious domains can link to automation to block them immediately.
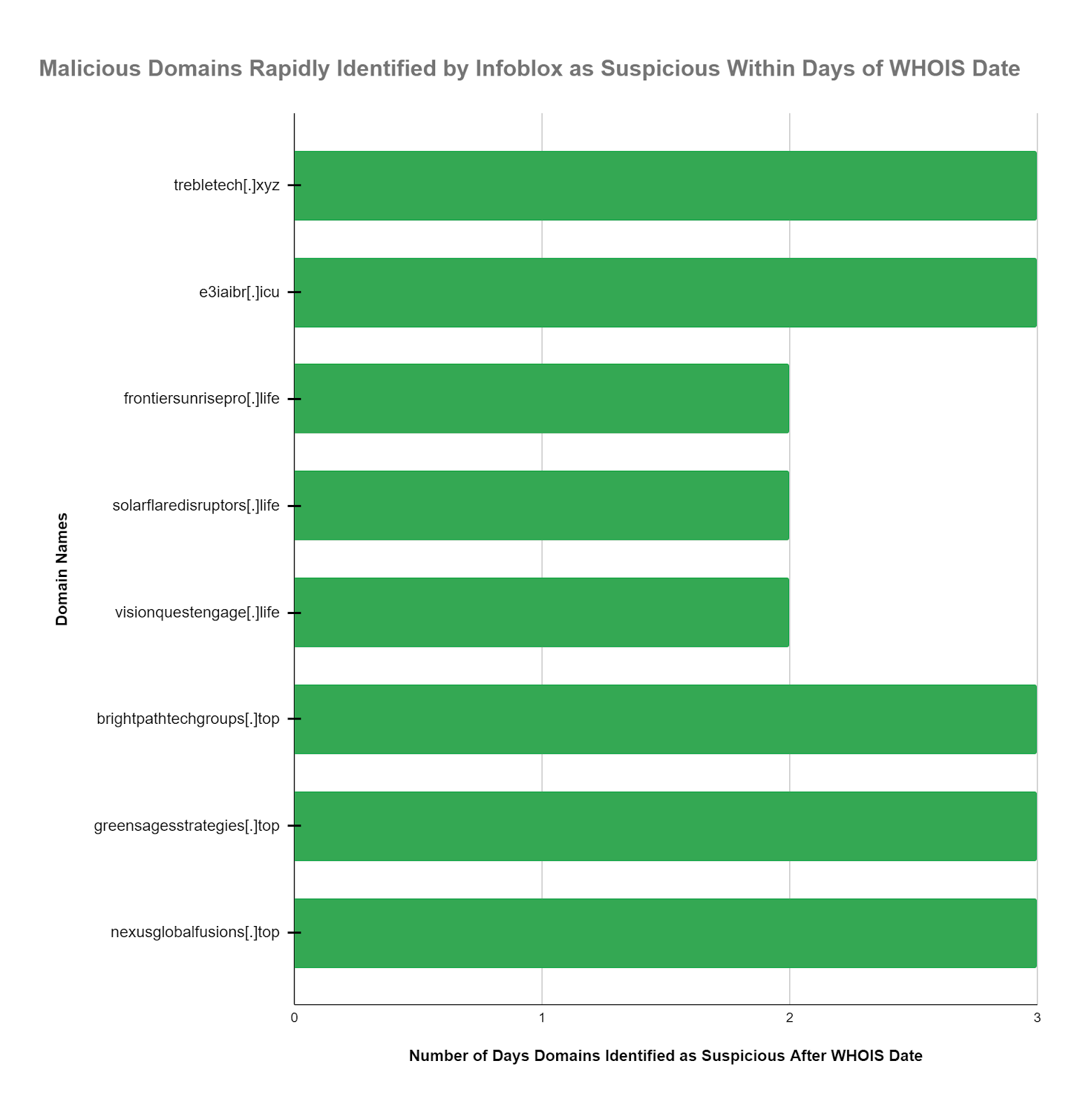
- The same number of the JinxLoader domains were blocked as suspicious within an average of 2.63 days (63 hours) after the WHOIS domain registration date.
OSINT publication dates may sometimes be unclear or lack precision. The dates of published articles by reputable 3rd parties may not always accurately reflect the OSINT availability of each individual domain. The important point is that even if you have the OSINT data, it must propagate through the threat feeds you use and your cybersecurity ecosystem to support actionable policies. All of that is automated with Infoblox DNS Detection and Response (DNSDR) and our suspicious domain data.
Comparison to WHOIS Data
WHOIS data is often as close as you can get to reality on the cyber battlefield. Comparison to WHOIS data tells you how your threat intelligence systems are really working. To provide context on the performance of our suspicious threat intel feeds we extracted WHOIS dates and found that 53.3% of the JinxLoader domains were blocked as suspicious within an average of 2.3 days (55.3 hours) after the WHOIS domain registration date. The WHOIS dates are relatively precise and provide another perspective on the high value and relative performance of suspicious DNS threat intel feed content.
The threat actors behind most campaigns have learned to continually create and change the domains they use to camouflage their malicious activities. All of the key domains used in perpetuating the JinxLoader campaigns may be shut down at any time and replaced with new infrastructure. Infoblox Early DNS Detection threat intel brings tangible advantages to your organization.
Break Your Attacker’s OODA Loop With Suspicious Domain Data
What is the OODA loop you say? Observe, Orient, Decide, and Act is a four step approach to military decision making developed by military strategist and United States Air Force Colonel John Boyd. As a fighter pilot, Boyd wanted to develop a simple, repeatable methodology for making rapid iterative decisions in battle where a fraction of a second could mean the difference between life and death.
The modern cybersecurity OODA loop brings focus to filtering available information, providing context, and then rapidly making the best decision. This comes with the understanding that these decisions can and will change as more data becomes available. Once again, it is about the need to be proactive and to move with speed against potential threats.
The OODA loop is the point-counterpoint between defenders and attackers. Attackers effectively have a plan for how they think the OODA loop will unfold given the techniques they execute and the timeline they project. They lay the trap and expect defenders to fall into it.
Infoblox DNS Early Detection can help drive your OODA loop faster and move the advantage back to your defenders.The goal for defenders is to detect and observe the earliest sign of a planned malicious cyber event or Cyber Kill Chain, and then take rapid steps to break that KIll Chain. Defenders need to get inside and ahead of the attacker’s OODA loop. The more rapidly defenders can respond to that earliest sign of a malicious cyber event, the more likely that they can minimize impact to their organization and shut down the threat.
Infoblox Threat Intel proprietary technology can detect suspicious domains faster and more efficiently than the usual methods in the industry. Suspicious domain feeds provide a significant advantage in developing and using DNS threat intelligence information. With Infoblox suspicious domain data, security operations teams can get the timely information they need to prevent and counter the new threats before they do any damage.
| By using Infoblox’s suspicious domain data, our customers can help protect themselves from a disastrous data breach. Suspicious domain data can potentially lower risk and boost the ROI of your threat intelligence program. |
For Additional Information
Infoblox Threat Intel provides fast access to accurate, contextual threat alerts and reports sourced from our own real-time research teams. Suspicious Domains feeds were introduced as an Infoblox proprietary capability on November 10, 2022 and, since then, have successfully provided many thousands of customers with the advanced information to block domains which ultimately become malicious long before most other threat intelligence sources identify them as malicious. Infoblox allows your team to leverage the high value of suspicious domain threat intelligence while ensuring unified security policy across your entire security infrastructure. Infoblox threat data minimizes false positives, so you can be confident in what you are blocking.
To learn more about suspicious domains and DNS early detection:
https://www.infoblox.com/threat-intel/
To learn more about BloxOne Threat Defense:
https://www.infoblox.com/products/bloxone-threat-defense/
To learn more about Advanced DNS Protection:
https://www.infoblox.com/products/advanced-dns-protection/
To learn more about the National Security Agency (NSA) and Cybersecurity & Infrastructure Security Agency (CISA) guidance on Protective DNS:
https://media.defense.gov/2021/Mar/03/2002593055/-1/-1/0/CSI_PROTECTIVE%20DNS_UOO117652-21.PDF
Footnotes
- https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html Cyber Kill Chain is a registered trademark of Lockheed Martin.