Threat actors have improved their techniques and use malicious domains to launch fast and damaging attacks. These domains are often detected and shared too late by OSINT and threat intel feeds. Defenders need to be able to act faster to stop them.
| Infoblox’s DNS Early Detection Program can spot potentially malicious domains faster than most methods. It uses proprietary techniques to flag these domains as suspicious before they cause harm. The program also compares our analysis of malicious domains with the data from public open source intelligence (OSINT) sources and commercial threat intel feeds. |
Our DNS Early Detection Program highlights and showcases the findings of Infoblox proprietary techniques that provide the earliest possible identification of potentially malicious domains. Infoblox early detection helps defenders gain an edge over threat actors. We identify malicious domains as suspicious early on and make them available for blocking. This way, defenders can prevent attacks days, weeks, or even months before they see them in OSINT or threat intel feeds. In this blog, we share an analysis we did of domains identified as malicious in OSINT by CSIRT KNF, and many examples of our early identification as suspicious.
CSIRT KNF Report on Global Postal Service Phishing Campaign
The Polish Financial Supervision Authority’s Computer Security Incident Response Team (CSIRT KNF1) has uncovered and continues to monitor a phishing campaign that targets mail users in many countries, including Poland, Bolivia, Norway, Portugal, Kuwait, Estonia, and others. CSIRT KNF has done an excellent job in identifying critical infrastructure used by the threat actors, and methodically monitoring and documenting their activity.
The attackers pretended to be reputable postal services and tricked users into giving up their money. They sent messages about fake shipping issues and included a link to a fraudulent website. When users clicked on the link, they saw a website that looked like a genuine postal service, but it was designed to collect their login and payment card information.
CSIRT KNF quickly discovered the infrastructure that the attackers used, including the control panels that they used to run and track the attacks. CSIRT KNF has gained a deep insight into the strategies and techniques of these attackers.
CSIRT KNF most recently published the latest list of observed malicious domains which we have used for our analysis2. In earlier reports on this malicious campaign they also published a large number of malicious domains and more.
Analysis and Methodology
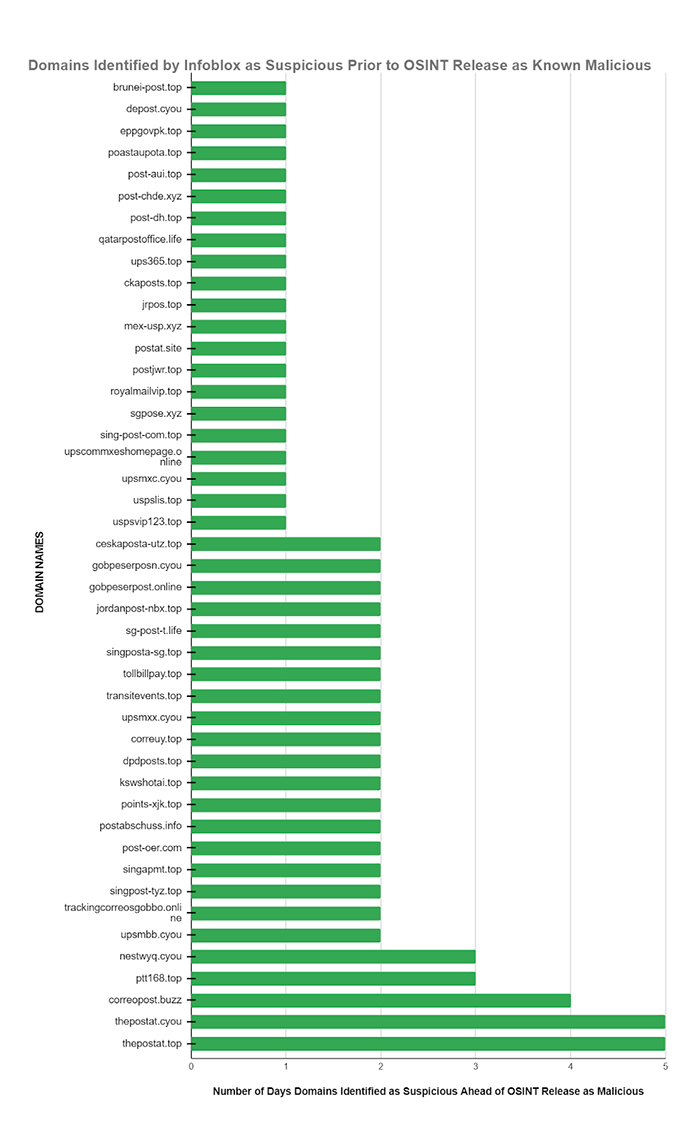
In early November, 2023, data on 107 Global Postal Services Phishing Campaign domains were published in OSINT and analyzed by the Infoblox team to determine if they were identified earlier by our suspicious domain feeds.
Each malicious domain identified in OSINT was researched in the Infoblox Dossier portal by our team. We reviewed our timeline feature to extract the earliest dates associated with Infoblox suspicious designation. We also extracted the WHOIS information for additional context.
| Infoblox identified many of the malicious domains as suspicious 1 to 3 days earlier than OSINT availability. Similarly, Infoblox identified many of the malicious domains within 1 to 2 days of their WHOIS registration. This enabled our customers to stop the execution of the intended Kill Chain3 by automatically blocking access to these dangerous domains. |
The conclusions of our analysis were definitive:
- 47 domains were identified as suspicious by Infoblox an average of 4.72 days prior to the availability of the OSINT designation as malicious.
- This number was skewed by two domains mocgoevkw[.]top and post-at[.]services which showed designation as suspicious by us at 20 and 123 days, respectively.
- Removing these two from the calculations shows that for the remaining 45 domains designation as suspicious was a little under 2 days on average.
- Normally in this type of analysis we find our DNS early detection program identifies suspicious domains weeks to months ahead of OSINT identification as malicious. Not just a few days as in this analysis.
- This result being measured in a few short days is likely due to the exceptional work done by the CSIRT KNF to rapidly identify the new threat actor infrastructure as OSINT.
- Remember that there can be several days to several weeks (to infinity and beyond!) from availability via OSINT to utilization by your cybersecurity ecosystem and defense-in-depth strategy. Infoblox designation of suspicious domains can link to automation to block them immediately.
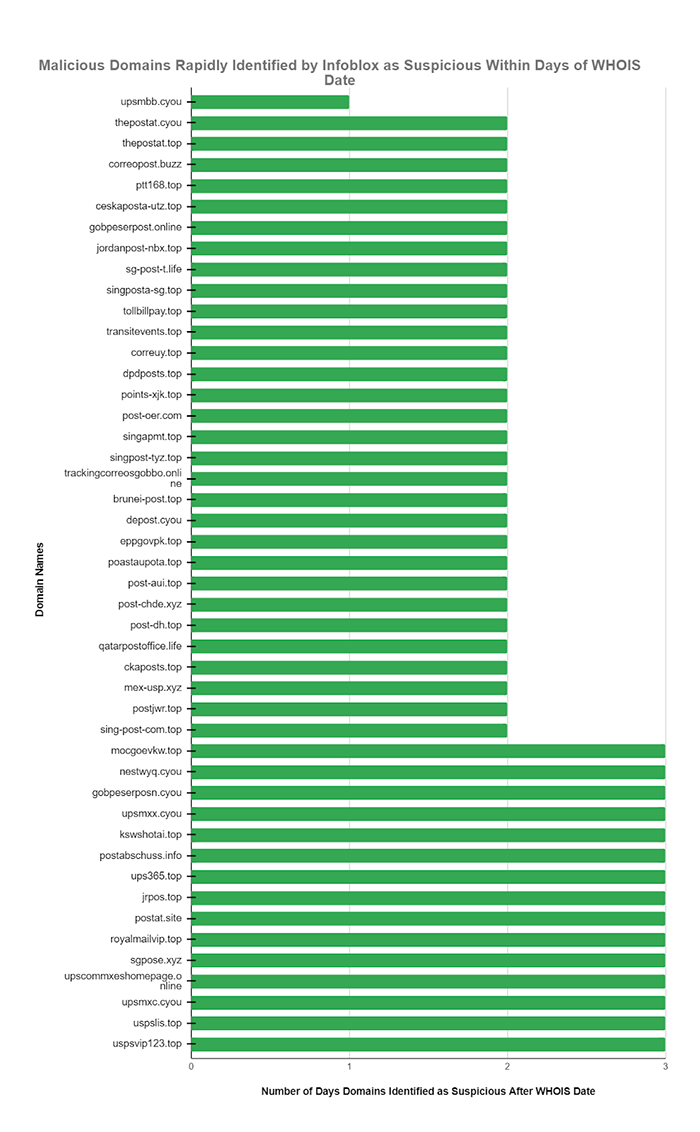
- The same number of the Global Postal Services Phishing Campaign domains were blocked as suspicious within an average of 2.3 days (55.3 hours) after the WHOIS domain registration date.
Note that two previously mentioned domains mocgoevkw[.]top and post-at[.]services which showed designation as suspicious by us at 20 and 123 days, respectively, are not included in either of the graphics in this blog.
It is often the case that OSINT publication dates may sometimes be unclear or lack precision. The dates of published articles by reputable 3rd parties may not always accurately reflect the OSINT availability of each individual domain. More important, is that this information has to propagate through the threat feeds you use and then your cybersecurity ecosystem to support actionable policies. All of that is automated with Infoblox DNS Detection and Response (DNSDR).
Comparison to WHOIS Data
Comparison to WHOIS data really tells you how your threat intelligence systems are really working. To provide context on the performance of our suspicious threat intel feeds we extracted WHOIS dates and found that a large percentage of the Global Postal Services Phishing Campaign domains were blocked as suspicious within an average of 2.3 days (55.3 hours) after the WHOIS domain registration date. The WHOIS dates are precise and provide another perspective on the high value and relative performance of suspicious DNS threat intel feed content.
Speed is always of the essence. The threat actors behind this campaign have been observed over time continually creating and changing the domains they use to hide their activities. All of the key domains used in perpetuating the Global Postal Services Phishing Campaign or any other campaign may be shut down at any time and replaced with new infrastructure. You can see the tangible advantages Infoblox early DNS Detection threat intelligence can bring to your organization.
“Shift Left” With Suspicious Domain Data
Our proprietary technology can detect suspicious domains faster and more efficiently than the usual methods in the industry. This is a significant “Shift Left” in developing and using DNS threat intelligence information. With Infoblox suspicious domain data, security operations teams can get the timely information they need to prevent and counter the new threats before they do any damage.
| By using Infoblox’s suspicious domain data, our customers can help protect themselves from a disastrous data breach. Suspicious domain data can potentially lower risk and boost the value of your threat intelligence program. |
For Additional Information
The Infoblox Threat Intelligence Group provides fast access to accurate, contextual threat alerts and reports sourced from our own real-time research teams. Suspicious Domains feeds were introduced as an Infoblox proprietary product on November 10, 2022 and, since then, have successfully provided many thousands of customers with the advanced information to block domains which ultimately become malicious long before most other threat intelligence sources identify them as malicious. Infoblox allows your team to leverage the high value of suspicious domain threat intelligence while ensuring unified security policy across your entire security infrastructure. Infoblox threat data minimizes false positives, so you can be confident in what you are blocking.
To learn more about suspicious domains and DNS early detection:
https://www.infoblox.com/threat-intel/
To learn more about BloxOne Threat Defense:
https://www.infoblox.com/products/bloxone-threat-defense/
To learn more about Advanced DNS Protection:
https://www.infoblox.com/products/advanced-dns-protection/
To learn more about CSIRT KNF and the Global Postal Services Phishing Campaign:
https://lnkd.in/dzypJhwJ
https://cebrf.knf.gov.pl/images/International_phishing_campaign_EN-2.pdf
To learn more about the National Security Agency (NSA) and Cybersecurity & Infrastructure Security Agency (CISA) guidance on Protective DNS:
https://media.defense.gov/2021/Mar/03/2002593055/-1/-1/0/CSI_PROTECTIVE%20DNS_UOO117652-21.PDF
Footnotes
- https://www.knf.gov.pl/dla_rynku/CSIRT_KNF
- https://lnkd.in/dzypJhwJ
- https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html Cyber Kill Chain is a registered trademark of Lockheed Martin.