Introduction
In early 2022, Infoblox detected a widespread attack involving compromised WordPress websites that conditionally redirect visitors to intermediary command and control (C2) and dictionary domain generation algorithm (DDGA) domains.1 Our analysis revealed that the attack was using a long-standing, continually evolving DNS infrastructure, and we named the actor controlling this infrastructure VexTrio. According to a recent report by Sucuri, VexTrio has notably advanced their attack strategy and was observed using DNS TXT records to redirect website visitors to their C2 infrastructure.2 For over two years, VexTrio threat actors have operated a large DNS infrastructure to deliver scam webforms, browser hijackers, adware, spyware, and other potentially unwanted programs (PUPs) to targets across many industries. Although security defenders often overlook these kinds of threats in favor of more harmful malware, the severity of VexTrio’s attack should not be underestimated. The versatility of this DNS infrastructure actor and their ability to do just about anything demonstrates a type of “Swiss Army Knife” nature. Previously, VexTrio was the delivery system for a Danish spear-phishing attack, and was strongly associated with a Glupteba campaign abusing the blockchain system.3,4 We assess that this latest feature will allow VexTrio to bypass more detection systems and strengthen the persistence of its DNS infrastructure. In this advisory report, we go over the new DNS redirect mechanism and other tactics, techniques, and procedures (TTPs) changes. For details of the malicious javascript, see the original reporting by Sucuri.
Background
Infoblox’s Threat Intelligence Group (TIG) has been tracking VexTrio since early 2022. We developed a DNS signature based on numerous attributes associated with the VexTrio DNS infrastructure. This signature allows us to accurately detect both the intermediary C2 and DDGA domains that are involved in VexTrio cyber campaigns. We confirmed that the activity described in the Sucuri report is VexTrio by checking the signature against the reported domains. Based on further research, we assess that VexTrio’s attack chain, as well as the delivered content, largely remains the same. The threat actors continue to compromise websites running vulnerable versions of WordPress and injecting malicious JavaScript into them. This malicious script conditionally redirects website visitors to intermediary controllers that then navigate victims to harmful web landing pages. On a deeper level, the actors made several specific TTP modifications. Among these, the most notable change is the transformation of the JavaScript that is injected into the compromised WordPress websites. The script now gathers victim information and communicates with a DNS-based traffic distribution system (TDS) server via Google’s Public DNS service.5 We suspect this change will challenge detection systems that are not DNS-based or dependent on URL analysis. This is explained in further detail later in this report.
Changes in Tactics, Techniques, and Procedures
Since the release of Infoblox’s first analysis report, VexTrio threat actors have made modifications to their DNS infrastructure for better survivability from detection systems. Some of the changes show a simple DNS configuration update, while others indicate a high level of implementation effort according to the Pyramid of Pain.6 Based on our analysis of historical VexTrio indicators, we identified some notable changes to the TTPs:
- Compromised WordPress websites recently fetch the C2 intermediary redirect URL via a DNS TXT record,
- subdomain names on the DDGA domains are based on random numerical characters; previously they were random alpha labels,
- VexTrio has expanded their dictionary by at least 138 new words (See Figure 1),
- and some intermediary C2 domains have switched from using dedicated and actor-controlled nameservers to shared Cloudflare nameservers.
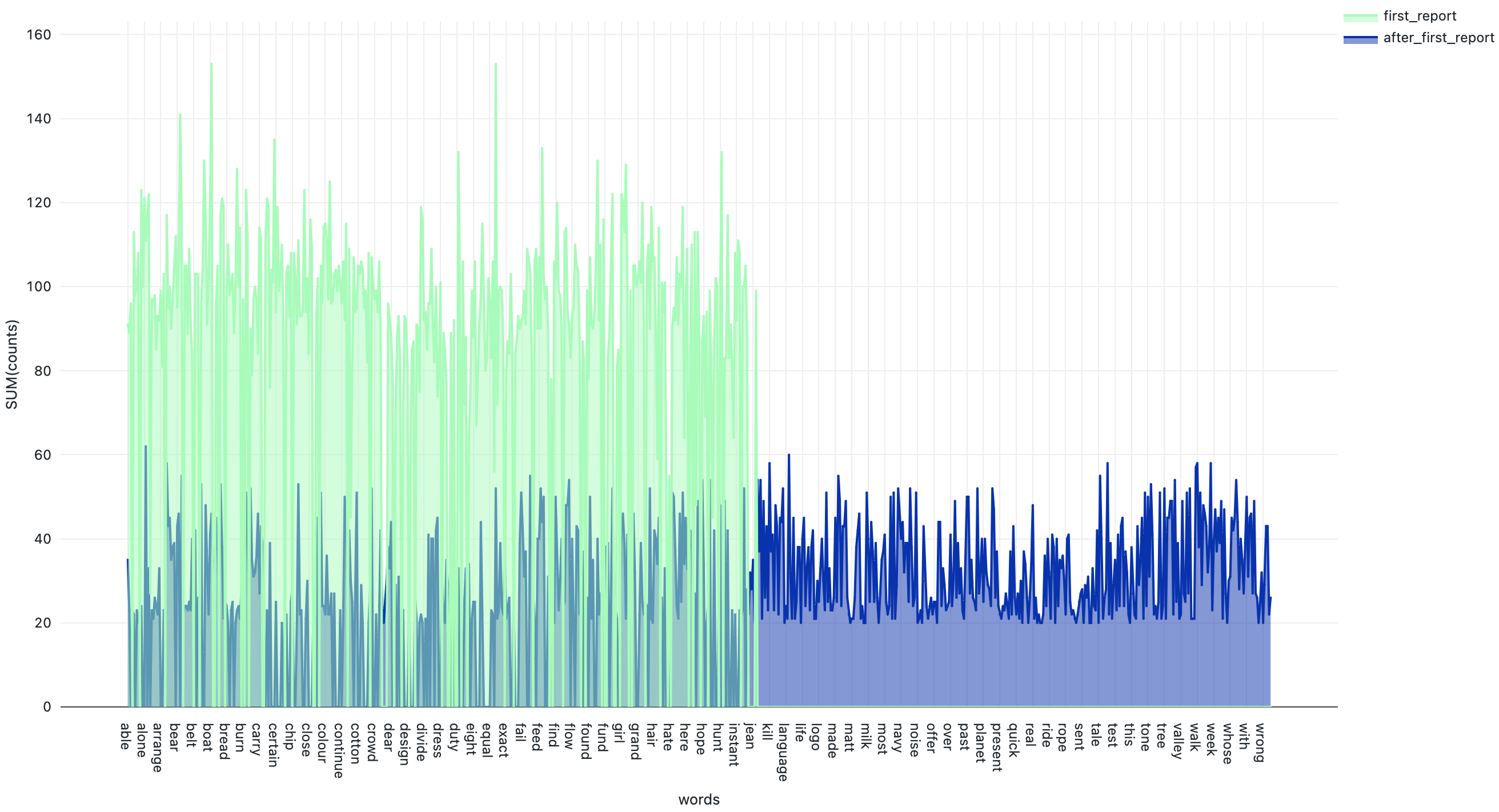
Figure 1. DDGA domains discovered after first publication show expanded dictionary7
Overall, these changes make it challenging for security professionals to identify, track, and disrupt VexTrio network activity. DDGAs are particularly difficult to detect accurately due to their high overlap with legitimate domain assets. Additionally, the continuous change in VexTrio’s selection of DNS providers and subdomain naming scheme can quickly outpace the creation of security rules. This is especially true for organizations that have a limited view of the DNS landscape and rely on detection methods that are not scalable, such as URL blocklisting.
DNS-based Traffic Direction System
TDSs are intermediate controllers that conditionally redirect the HTTP traffic flow of legitimate website users to harmful web content. At the time of our first publication, VexTrio’s TDS showed a more simple design. Previously, the malicious script embedded in the compromised WordPress websites would directly load a remote JavaScript via an HTTPS request and then execute it. This would result in a redirection to other intermediary servers controlled by VexTrio. According to the recent Sucuri analysis, the actors upgraded the embedded scripts to an obfuscated and base64-encoded JavaScript. This new script fetches the URL location of the intermediary controller by sending DNS requests to a malicious DNS server (TDS) that is controlled by VexTrio. More specifically, the malicious JavaScript gathers the name of the compromised website and the visitor’s public IP address. Using Google’s DNS service, it then passes this information to the actors via the subdomain of the TDS DNS server (e.g. tracker-cloud[.]com). The program running on the DNS server parses the data within the subdomain and responds back to the JavaScript with a base64-encoded version of the intermediary redirect URL. Figure 2 is a high-level visual representation of this DNS transaction.
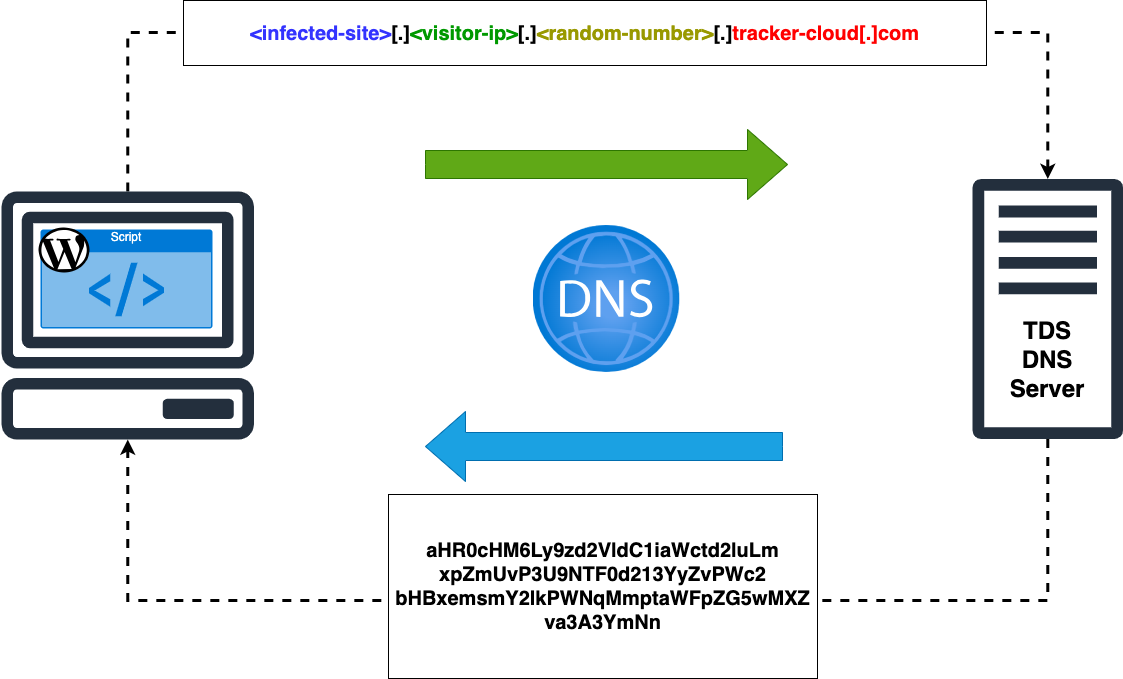
Figure 2. DNS TXT Response from the TDS
From the threat actor’s perspective, the main advantage for using a DNS-based TDS as opposed to calling it directly via HTTP, is persistence. By using Google as an intermediate DNS communication channel, the TDS server is not susceptible to URL or DNS blocking security methods. Many organizations are unlikely to block the Google Public DNS server domain (dns.google), which may be an integral part of their business operations.
Prevention and Mitigation
Infoblox specializes in security solutions that help protect organizations against persistent DNS threats such as VexTrio. Using effective DNS signatures and statistical-based algorithms, Infoblox continues to track VexTrio’s intermediary C2 and DDGA domains. We detected and blocked all of the DDGA indicators provided in the Sucuri report before they were activated for malicious activity. VexTrio is a large and malicious network that reaches a wide audience of internet users. Organizations should not undervalue the severity of VexTrio’s threat based on the perception that the delivered content is seemingly less dangerous than other high profile malware. As mentioned earlier in the report, VexTrio can be used as a delivery vector for other cybercrime syndicates. To improve your organization’s resilience against VexTrio and similar TTPs, we recommend the following actions for protection:
- Disable JavaScript on web browsers completely, or enable it only for trusted sites. This can help mitigate attacks by actors leveraging the VexTrio infrastructure, as well as those who capitalize on the use of JavaScript to run their tasks.
- Consider using an adblocker program to block certain malware activated by popup ads. Along with an adblocker, consider using the web extension NoScript, which allows JavaScript and other potentially harmful content to execute only from trusted sites to reduce the attack surface available to actors.
- Subscribe to Infoblox RPZ feeds that offer protection against malicious hostnames. These feeds enable organizations to stop the connection by actors at the DNS level, as all components described in this report (compromised websites, intermediary redirect domains, DDGA domains, and landing pages) require the DNS protocol. TIG detects these components daily and adds them to Infoblox’s RPZ feeds.8
- Leverage Infoblox’s Threat Insight service, which performs real-time streaming analytics on live DNS queries and can provide high-security coverage, along with protection against threats that are based on DGAs as well as DDGAs.9
Endnotes
- https://blogs.infoblox.com/cyber-threat-intelligence/cyber-threat-advisory/vextrio-ddga-domains-spread-adware-spyware-and-scam-web-forms/
- https://blog.sucuri.net/2023/08/from-google-dns-to-tech-support-scam-sites-unmasking-the-malware-trail.html
- nozominetworks.com/blog/tracking-malicious-glupteba-activity-through-the-blockchain/
- https://derant.com/network%20monitoring/2022/06/07/targeted-phishing-past-defender.html
- https://www.bleepingcomputer.com/news/security/tds-systems-are-the-next-big-money-makers-in-the-land-of-cybercrime/
- https://www.sans.org/tools/the-pyramid-of-pain/
- This diagram focuses on words that show a minimum repetition of 20 and character length of 4.
- https://community.infoblox.com/t5/infoblox-tide-solution/custom-rpz-feeds-from-infoblox-tide/gpm-p/14027
- https://www.infoblox.com/resources/datasheet/threat-insight








