Author: Nick Sundvall
The Discovery
Infoblox security researchers have uncovered a group of malicious domains that are being used to host cryptocurrency scams, some of which have been associated with the hacking of Youtube channels.
We were able to find the domains by reviewing and analyzing queries in our networks for domains that incorporated certain suspicious keywords. Armed with these initial discoveries, our researchers were able to pivot to other domains belonging to the same registrant organization, CryptDesignBot. Further open-source intelligence enriched our findings and provided greater context, leading us to uncover additional data linked to the ongoing compromise of Youtube channels.
As we mentioned above, the actor or actors behind the creation of these malicious domains initially registered them under an organization that goes by the name of CryptDesignBot. A simple whois query on these domain names revealed that the registrant country is Russia. As we monitored the domains we found during our investigation, we noticed that many of them were frequently changing registrars. It’s quite common for threat actors to try to conceal information about the domain’s creation, especially if they suspect that security researchers could use it to block the domains or identify the perpetrators.
Also it is important to note that these domains are lookalike domains. Lookalikes are domains created to look like a legitimate domain: this kind of threat is common among cybercriminals, and Infoblox recently published a thorough whitepaper on the threat landscape for lookalikes over the last year: https://www.infoblox.com/resources/whitepaper/infoblox-report-deep3r-look-at-lookal1ke-attacks.
Hacked Youtube Channels
Hacked Youtube channels are a profitable platform for threat actors to exploit famous brands for nefarious purposes. Typically, they first remove the channel’s legitimate videos and change its name and profile picture. They then host a “livestream” event promoting their scam crypto domains. Despite being promoted as a “livestream,” these events often just replay old videos.
Threat actors can gain unauthorized access to Youtube channels by using virus or malware tools to steal the cookie that the victim’s browser generates to keep a user logged in. With the cookie, malware like YTStealer1 can access the victim’s account without their login credentials or two-factor authentication. YTStealer targets Youtube channels and extracts authentication cookies using session hijacking techniques, which enable attackers to gain unauthorized access to the account.
Despite the malware’s ability to persist on the victim’s endpoint for a prolonged period, many threat actors choose a non-persistent approach to reduce the chances of detection and minimize the number of artifacts left on the infected host. This also makes it more challenging to detect the breach later. It’s worth noting that the malware is capable of stealing passwords and cookies, and incorporates several anti-sandboxing techniques, including using enlarged files, IP cloaking during downloads, and encrypted archives. In some cases, the malware even displays a false error message, which forces the user to click through to continue execution.
Web applications use session cookies to provide a personalized browsing experience and monitor user activity. These cookies are active until the user logs out and are often sent over insecure connections to the server. If session cookies are not secure, it is relatively easy for threat actors to discover and steal them through an actor-in-the-middle attack. Once they have gained access to a session cookie, threat actors can bypass multi factor authentication.
The Enticing Crypto Call to Action – Double Your Money
In the spirit of an Old School RuneScape scam, some of these cryptocurrency scam domains we discovered claim to double your cryptocurrency. For those that may not recall, Old School RuneScape (OSRS) is a massively multiplayer online role playing game by Jagex, and has a large community that is sometimes targeted by scammers. In one particular OSRS scam, the actor offers to double the target’s money and demonstrates this with a small amount. However, once the actor receives a larger amount from the victim, they vanish without a trace.
Those who visit double-ethereum[.]info and other related domains in the cluster we discovered may find that history repeats itself. The domains frequently use keywords associated with well-known people and brands such as Elon Musk, Kanye West, Andrew Tate, Tesla, Adidas, and others.
When reviewing many of these domains, we observed that Elon Musk and Tesla were common themes. For example, the domain, youtubetesla[.]net displays this image:
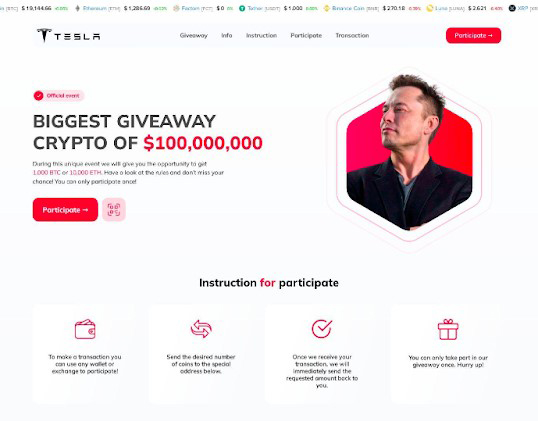
A Youtube video from the security researcher John Hammond at HuntressLabs goes into detail about this trending scam and provides other examples. In a moment of deja vu for us (timestamp 10:30 in the video) John shows a domain that surprisingly has the same exact site content as the screenshot above. Validation is welcome!
Prevention and Mitigation
Our threat researchers have identified numerous domains as suspicious. Some of them were detected earlier as suspicious new domains or lookalikes by our threat detection tools and were automatically blocked, providing protection for customers who use these feeds against likely harmful sites. The rest were added to our feeds by our team during the research. We recommend that organizations that are not customers of BloxOne Threat Defense add the indicators of compromise (IOCs) from this advisory to their blocklists manually or via our GitHub repository infobloxopen/threat-intelligence.2
Generally speaking, to prevent such types of attacks, it is important to implement measures that can protect against these threats. These may include:
- Protective DNS. The National Security Agency (NSA) recommends implementing this security control because it allows defenders to use threat intelligence data to block communication both to known malicious websites and threat actors, as well as those suspected as malicious. It can stop many of the most advanced malware tools and threat actors from establishing the communication that is essential to their attack chains. Protective DNS brings the ability to analyze, and be alerted to, DNS requests made to blocked domains. This information can then be incorporated into a Security Information and Event Management (SIEM) platform, allowing for effective investigation of incidents. DNS logging is an important and integral part of the monitoring process.
- Secure cookies. These direct the browser to only send cookies to the server when connecting through SSL, thereby preventing cookies from being observed and captured by unauthorized parties during transmission.
- HyperText Transfer Protocol Secure (HTTPS). This can prevent attackers from intercepting session IDs, authentication cookies, and other sensitive information.
- Random session IDs. Configure applications to generate random session IDs to prevent an attacker from guessing a user’s session ID.
- Session timeouts. Configure applications and system level controls to automatically log out users after a certain period of inactivity and thereby terminate the session associated with saved cookies.
Infoblox BloxOne™ Threat Defense
Infoblox BloxOne Threat Defense is equipped with protective DNS capabilities that are designed to combat today’s most sophisticated threats. It offers extensive threat intelligence from multiple sources, providing current, comprehensive, and accurate data about malicious hostnames, domains, IP addresses, and other relevant threat indicators. This enables DNS servers to detect and block malicious activity, including command and control (C2) communications to malevolent destinations. Advanced behavioral analytics, machine learning, and other advanced techniques applied to real-time DNS queries can also swiftly identify and halt zero-day DNS tunneling, DGA, data exfiltration, Fast Flux, lookalike domains, and more.
Threat intelligence plays a crucial role in enabling protective DNS, and Infoblox offers customers a wide range of options to customize the threat intelligence they receive. This includes a variety of feed sources that are managed and curated by the Infoblox threat research team for effectiveness and quality, as well as several specialized feeds from trusted third parties, including government, open-source, and other threat feed sources. The precise blend of threat intelligence available with BloxOne Threat Defense depends on the package purchased. The Advanced package even includes a tool that can support any threat intelligence feed and automate threat intelligence distribution across the entire security stack. This enables customers to power their defenses with a custom “super-feed” of threat intelligence, maximizing the value of all their security investments.
Infoblox’s DDI (DNS, DHCP, IPAM database) data is a valuable resource for gaining critical insights into related devices and actionable network context. This information can provide essential visibility into ongoing attacks and inform remediation strategies. Furthermore, integrating this data with SIEM and SOAR infrastructure can significantly reduce the time required for threat detection and automate incident response. When Infoblox identifies something malicious, a new device or virtual workload on the network, it automatically shares the event information and context with existing security infrastructures like endpoint EDR, SIEM, SOAR, and other solutions. This data can trigger the security tools to prevent network access or scan for vulnerabilities until it is compliant with policy.
For more information:
- Learn more about BloxOne Threat Defense
- Learn more about protective DNS and DNS security here
- Also refer to this recent Gartner report, which recommends organizations leverage DNS logs for threat detection and forensic purposes with their Security Information and Event Management platforms.
Sample List of IOCS:
The table below provides an abbreviated list of the indicators of compromise (IoOCs) relevant to our recent findings. For the complete list of IoCs, see our GitHub repository.3
| Indicators of Compromise | Description |
|---|---|
| 22spacex[.]space
22tesla[.]io 2x-tsla[.]com adidas-drop[.]org andrewtatecash[.]com bonustesla[.]com btcdrop[.]org ceo-xrp[.]net ceotesla[.]pro chatgptbonus[.]live doge2022-elon[.]com dot-pump[.]com double-ethereum[.]info doubletesla[.]live elon-gives[.]net elon-kanye[.]net promo-musk[.]com promo-musk[.]org promo-prize[.]live promo-tesla[.]info promo-tesla[.]org promo-x2[.]live youtubetesla[.]net |
Domains hosting cryptocurrency phishing scams with the original registrant CryptDesignBot. |
Endnotes
- https://www.intezer.com/blog/research/ytstealer-malware-youtube-cookies/
- https://github.com/infobloxopen/threat-intelligence
- https://github.com/infobloxopen/threat-intelligence/blob/main/cta_indicators/cryptdesignbot_cta_20230518_iocs.csv









![[Video] Changing Definition of Core Networking and Enterprise Expectations on Security](https://blogs.infoblox.com/wp-content/uploads/480288900-660x454-1.jpg)
