Author: Maël Le Touz
1. Executive Summary
This paper provides our analysis of a sample of malware called Prynt Stealer, which is spread by cybercriminals who use a number of online channels and groups to set up scams and share hacking tools. Most of the individuals involved in these exchanges have little technical knowledge. They collect credit card numbers by running smishing campaigns that send SMS messages to “numlists”: software-generated lists of valid, country-specific mobile phone numbers. Numlists are either sold in chunks (for example, 1000 phone numbers per chunk) or are generated by scripts advertised as numlist generators.
The sample analyzed below has been shared on Telegram and advertised as a numlist generator named NumberGrabberV5.zip. However, this application generates random, rather than the desired phone numbers, and is in fact a remote access tool (RAT) written in C# that is tailored to steal passwords and login information from infected Windows devices. This has been used by criminals from a specific group to target other criminals involved in scams and to gain access to their data, whether it is stolen passwords or credit card numbers. While this specific sample is not targeted at companies or non-criminal users, it is a textbook example of the numerous Telegram-enabled C# RATs that are sold as malware-as-a-service. In these cases, the buyer is presented with a simple tool for which they must provide a Telegram channel URL for command and control (C2). Once the buyer supplies the C2 URL, the tool will generate specific versions of the RATs that use their Telegram channel, employing various obfuscation and packers to evade static antivirus detection.
2. Malware Delivery
Most Telegram channels that discuss hacking automatically upload the shared files to VirusTotal, to perform antivirus checks. NumberGrabberV5.zip has low detections, making the victim more willing to execute it.1
After opening the file, the victim (who is likely another cybercriminal) is presented with a PE32 called Number_GrabberV5.exe: a Python script packaged by py2exe as a Windows executable and protected by PyArmor. Although some decompilers and deobfuscators exist for PyArmor, they fail to decrypt the most recent versions of the packer. The script presents the victim with a country code and what will appear to them to be a legitimate numlist generator. However, the phone numbers are generated at random, and their validity is never verified.
After performing various checks to ensure it is not running in a virtual environment, Number_GrabberV5.exe unpacks and executes another PE32 executable: updaters.exe.
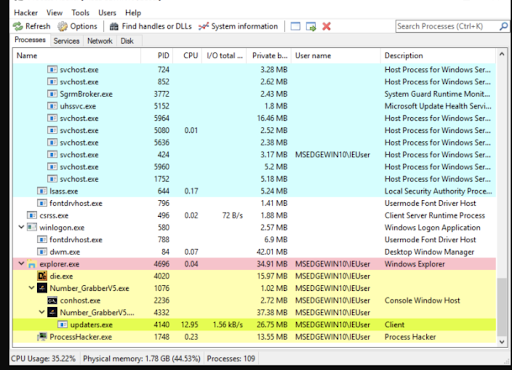
Figure 1: Process explorer view of Number_GrabberV5.exe. Note that updaters.exe has been created as a subprocess of Number_GrabberV5.exe (highlighted in green).
3. Installation of Prynt Stealer
updaters.exe is a version of Prynt Stealer: a malware-as-a-service fork of the popular RATs Stormkitty and AsyncRat, which use Telegram as a C2 channel. updaters.exe is a heavily obfuscated .NET application. To prevent reverse engineering, the criminals have used a custom obfuscation routine to hide function calls and names of variables. In addition to the obfuscation, most configuration strings and function calls are encrypted using AES and decrypted only at runtime, when the malware needs to access them. Removing the layers of obfuscations makes C# code readable by a human.
Once updaters.exe is run, it achieves persistence by writing a copy of itself to a folder and creating a scheduled task, shown in Figure 2 below.
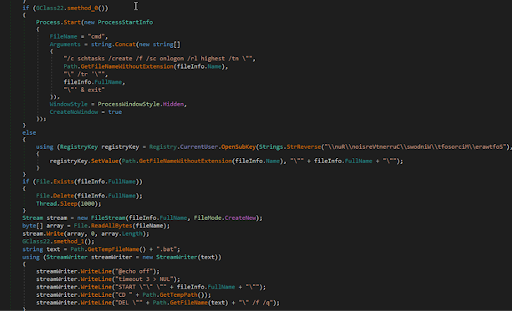
Figure 2: updaters.exe achieving persistence by creating a scheduled task at login.
4. Initial setup and information gathering
In the first run, Prynt Stealer checks the number of parameters to determine whether it is running in a sandbox. It also checks the processor type, the presence of debugging flags, the number of webcams connected, the existence of virtualization drivers, the battery level, the version and product key of Windows, the user name, and the antivirus software. The malware also tries to estimate the physical location of the device: it lists WIFI SSIDs and opens a web browser to Google Maps, to capture the approximate coordinates of the infected machine.
After the infected machine has passed these checks, the malware checks whether it can connect to the internet and the Telegram API’s domain.
5. Communications with the C2 server
After the malware has verified it is not running in a sandbox and is connected to the internet, it creates a self-signed certificate and uploads it to the C2 server. This initial communication contains the device’s fingerprint, which the malware has generated from the device’s characteristics.
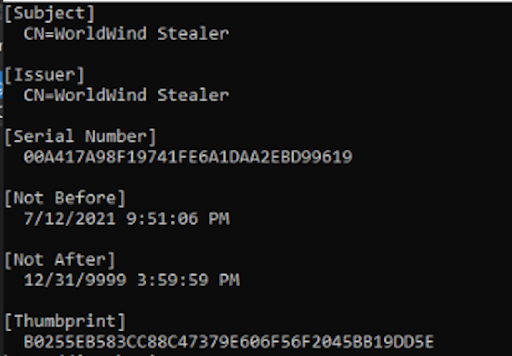
Figure: 3: Self-signed SSL certificate used for communication with the C2 server. All further communications will be encrypted through this certificate.
Communication to the C2 server is conducted through two different Telegram group URLs. One of them is used to exfiltrate stolen data, and the other is used to send additional commands to the implant operated by the cybercriminals via a Telegram bot. Cybercriminals increasingly leverage the Telegram bot API because it is a free alternative to setting up proprietary infrastructure to collect and exfil victim data.
6. Capabilities of Prynt Stealer
This version of Prynt Stealer can silently steal data from many applications, as listed in the table below and shown in Figure 4. Figure 5 shows a screenshot of the categories of stolen victim information that the malware sends to the C2.
| Applications | Data stolen by Prynt Stealer |
| Web browsers |
|
| Steam, Ubisoft Uplay, Minecraft, and other game applications | Login data |
| Zcash, Armory, Bytecoin, Jax, Keystore, Atomic Wallet, Exodus, Ethereum, Electrum, Guarda, and Coinomi, and other digital wallets | Wallets, passphrases, and private keys |
| Discord, Pidgin, Telegram, and other communication and networking applications | Tokens |
| NordVPN, protonVPN, and other VPN applications | Passwords and .ovpn files |
| FileZilla and other file-sharing applications | Login data |
Table 1. Data that Prynt Stealer can capture from various applications.
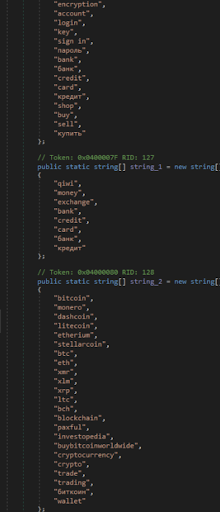
Figure 4: The keywords that Prynt Stealer attempted to find in process windows.
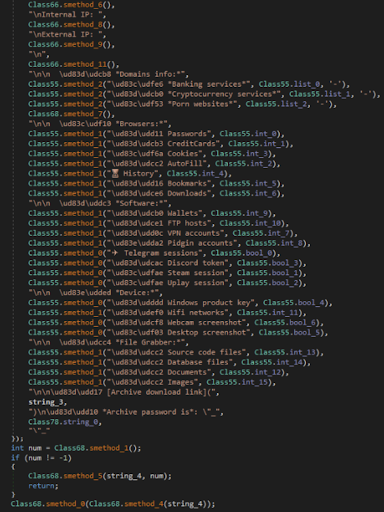
Figure 5: Summary of a victim’s information sent to the Telegram bot.
The malware offers a complete keylogger that can register all keystrokes and send them back to the C2 server. It can be remote controlled by the C2 server and take screenshots, perform network scans, take photos through webcams, and install plugins. Interestingly, when the malware detects specific adult-themed keywords in a process window, it takes a screenshot of the window and then takes a photo of the victim through the webcam, probably to blackmail the victim in the future. The malware can also monitor the clipboard for text that matches the format of a credit card or a crypto wallet; upon detecting a match, it transmits the stolen information to the C2 server.
Other modules offer reverse shells, the capability for creating archives of stolen files and passwords, and the capability for exfiltrating specific files. Despite the relative ease with which Prynt Stealer can be detected, it is still a powerful and versatile malware that can cause long-term damage.
7. Prevention and mitigation
Depending on the policy preferences of the organization, it is generally recommended to monitor or block all communications with the Telegram API and domains. Organizations should also prevent users from installing pirated or unregistered software and software-cracking tools. Finally, organizations should be familiar with appropriate Windows Startup entries, and regularly check them for potentially malicious and unexpected applicationsScan downloaded files by using antivirus software.
8. Indicators of Compromise (IOCs)
The table below provides a list of the IOCs relevant to our recent findings, which can also be found in our GitHub repository.2
| Indicators of Compromise | Description |
| 482f4cf7fe35de03824bddad6925ca4c17d4aaff0411c9d649fd1456afc3f99c | Hash of the original sample |
| 161b63a97d89bf3531175f3de3ade5c1c4eab758530943f018906ea26310ed63 | Hash of updaters.exe |
| hxxps[:]//api[.]telegram[.]org/bot5528293567:AAEvVqFZRYkeHFch3_kTGdMV2u4Swi0-pT8/ | Data exfiltration URL |
| hxxps[:]//api[.]telegram[.]org/bot1784055443:AAG-bXLYtnFpjJ_L3ogxA3bq6Mx09cqh8ug/ | C2 URL for command and control |
- https://www.virustotal.com/gui/file/482f4cf7fe35de03824bddad6925ca4c17d4aaff0411c9d649fd1456afc3f99c
- https://github.com/infobloxopen/threat-intelligence/tree/main/