Author: Nick Sundvall
1. Overview
On 2 and 3 March, Infoblox observed a malspam campaign that used messages related to Russia’s invasion of Ukraine. This malspam campaign was attempting to lure users into opening an attached .xlsx file that downloads the Remcos remote access trojan (RAT). Infoblox has previously reported on malspam campaigns distributing Remcos.1,2
We observed multiple Ukraine-related malspam campaigns within the first week after the invasion. Some of them distribute donation or cryptocurrency scams; others distribute malware, such as Remcos.
2. Customer impact
A German company called Breaking Security has been offering Remcos since 2016.3 One of the versions offered is free and has a limited number of features, and the other version is paid and starts at 58 Euros. Although Remcos is marketed as a legitimate remote administration tool, it is frequently abused by threat actors and used for malicious purposes.
Breaking Security actively maintains and updates Remcos, with the latest update released on 10 February. The capabilities of Remcos include remotely controlling infected computers, logging keystrokes, and taking screenshots.
3. Campaign analysis
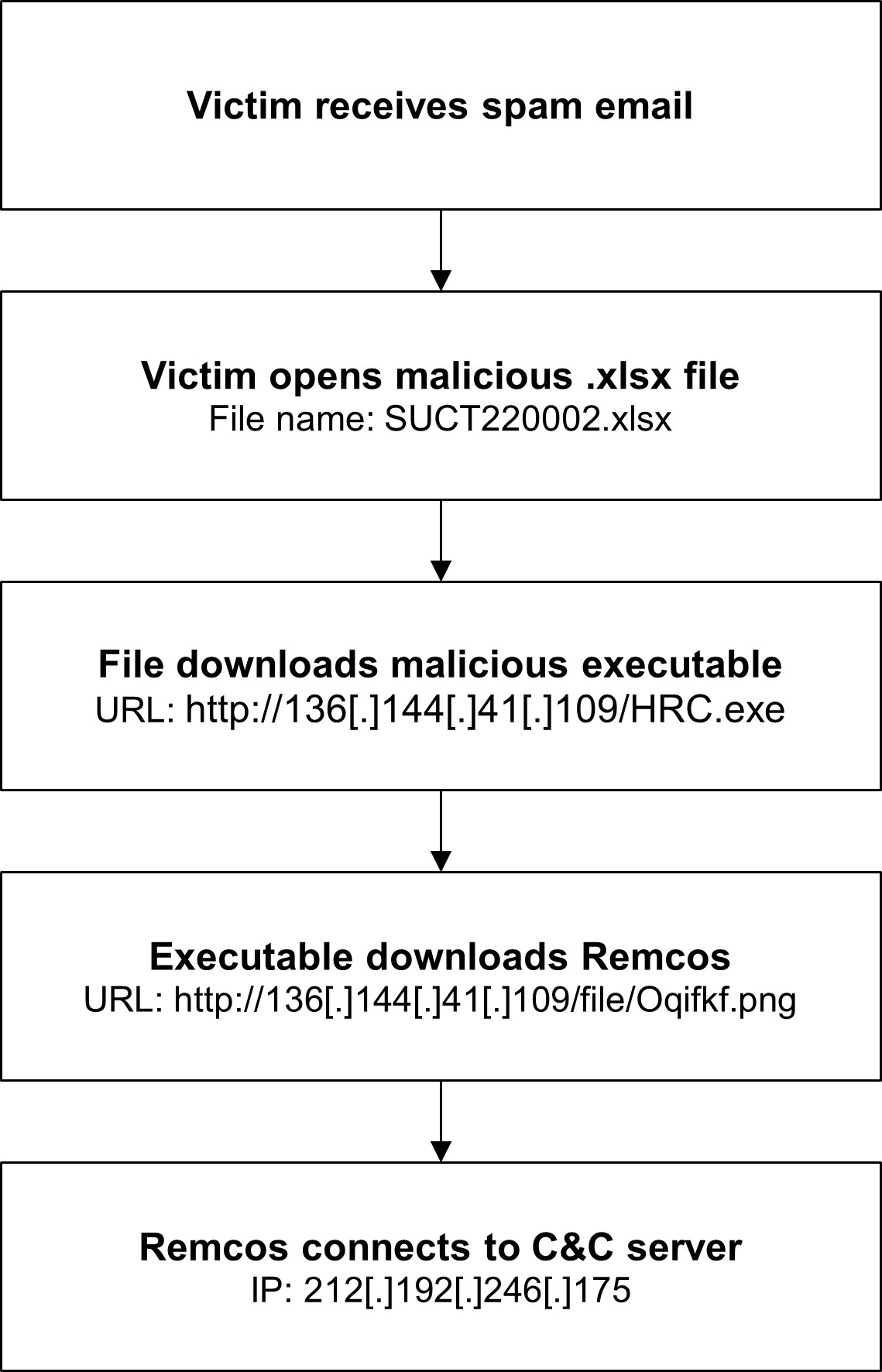
In this campaign, the threat actor(s) send messages with a variety of different subjects, including Re: Ukraine war || Order SUCT220002. The body section is always empty. The attached file is named SUCT220002.xlsx.
4. Attack chain
When a user opens the attachment, the file exploits a vulnerability in Microsoft Office’s Equation Editor, CVE-2017-11882. The exploit downloads and runs an executable, Oqifkf.exe, from http://136[.]144[.]41[.]109/HRC.exe. This executable then downloads and executes the final payload, remcos.exe, from http://136[.]144[.]41[.]109/file/Oqifkf.png. From here, Remcos reaches out to newremc22.ddns[.]net, a legitimate Dynamic DNS (DDNS) service, to get the IP address of the command and control (C&C) server, 212[.]192[.]246[.]175.
5. Vulnerabilities and mitigation
Infoblox strongly recommends that businesses consider the following security measures:
- To block known vulnerabilities that could be targeted by threat actors, keep computers and all endpoints up to date with the latest security patches. A patch for the CVE exploited in this attack was released in 2017.
- Always be suspicious of vague or empty emails, especially those with prompts to open attachments or click links.
- Scan downloaded files with antivirus software.
Endnotes
- https://blogs.infoblox.com/cyber-threat-intelligence/cyber-campaign-briefs/remcosrat-malspam-campaign-spoofs-uae-machinery-company-correspondence/
- https://blogs.infoblox.com/cyber-threat-intelligence/cyber-campaign-briefs/guloader-delivers-remcos-rat/
- https://any.run/malware-trends/remcos
Appendix (downloadable list here)
| Representative Indicators of Compromise | Description |
| Re: Ukraine war || Order SUCT220002
Re: Outstanding payment OCEAN PILGRIM-PORT CHARGE PAYMENT ADVICE Blocked Transaction – SWIFT Message Ref: 2092022 |
Email subject |
| SUCT220002.xlsx | File attachment name |
| 4907309437e12932d437f8c3ae03fbfde7d4e196b6f1dc7f2d98e3a388ce585c
32b2815cdaadfdd47448673d44b03d480939162234234bf09e74aa8ab936755c |
File attachment SHA256 |
| http://136[.]144[.]41[.]109/HRC.exe
http://136[.]144[.]41[.]109/file/Oqifkf.png |
Remcos download URL |
| Oqifkf.exe
remcos.exe |
Remcos file name |
| 537288ba6b141a9e76bbd1f77348494c4b3b82bb0c1f0c08afeeb544ccea85e8
706f40859cd3de0725c0c1795e98277d54bbc37ff90fc1e251e2eb99d0e713f0 |
Remcos file SHA256 |
| newremc22.ddns[.]net | DDNS domain |
| 212[.]192[.]246[.]175 | C&C server IP |










