Author: Christopher Kim
1. Overview
On 1 March, Infoblox observed a malspam campaign that was using messages related to Russia’s invasion of Ukraine. The malspam campaign was trying to lure users into downloading a ZIP file attachment whose contents could download the Agent Tesla keylogger.
This campaign occurred a week after Russia invaded Ukraine. It is one of multiple campaigns that have taken advantage of the conflict by luring users via socially engineered emails and websites with lookalike domains that serve fake donation content.1
2. Customer impact
Agent Tesla is a malware-as-a-service (MaaS) remote access trojan (RAT) that security researchers first discovered in 2014. It is usually distributed via spam or phishing emails, and it has many capabilities for stealing information from a victim’s machine, including the following:
- logging keystrokes
- extracting data from the host’s clipboard
- capturing screens
- grabbing forms
- stealing credentials from VPN software
After gathering sensitive information from a victim’s machine, Agent Tesla exfiltrates the stolen information by using a web browser or an email client.
3. Campaign analysis
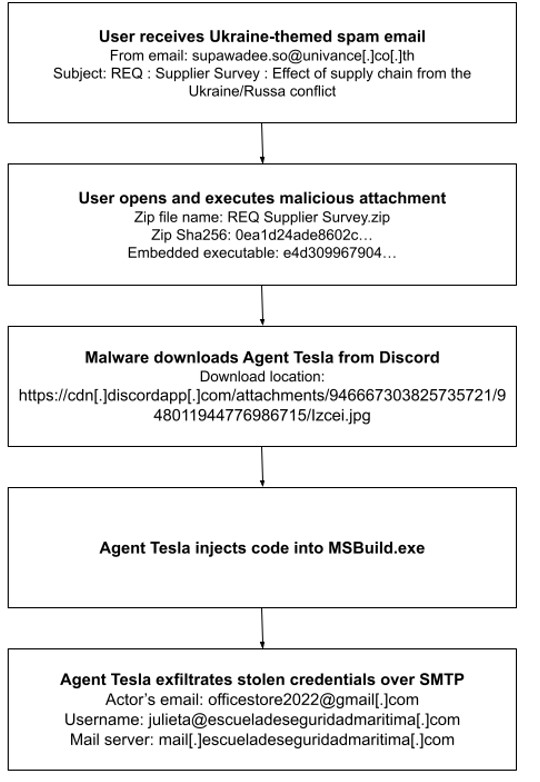
In this campaign, the threat actor(s) crafted messages using the email address supawadee.so@univance[.]co[.]th to impersonate UNIVANCE (Thailand) Co., Ltd: a manufacturer of automobile parts. The subject line is REQ : Supplier Survey : Effect of supply chain from the Ukraine/Russa conflict, and the body section is empty. The ZIP file attachment is named REQ Supplier Survey.zip and contains an embedded Microsoft Windows executable.
4. Attack chain
When a user extracts the ZIP file attachment, the embedded Windows executable is launched and writes itself to C:\Users\User\AppData\Roaming\Fgefvp\Gzgrfb.exe. A Run registry key is also created, and will enable Gzgrfb.exe to run every time the user signs in to the machine. Next, the malware downloads the Agent Tesla binary from Discord’s content delivery network (CDN) servers and injects the malicious code into the legitimate Windows process MSBuild.exe via process hollowing: a common technique for evading detection by antivirus software.2
Next, Agent Tesla steals account credentials and other sensitive information from the compromised system. It sends the stolen data to the actor’s email account officestore2022@gmail[.]com via SMTP, by using the compromised email account julieta@escueladeseguridadmaritima[.]com and the email server mail[.]escueladeseguridadmaritima[.]com.
5. Vulnerabilities and mitigation
Agent Tesla is a dangerous RAT that can have severe and negative impact on its victims. Infoblox strongly recommends that businesses consider the following security measures:
- Be wary of opening emails from unfamiliar senders, and inspect unexpected attachments before opening them.
- Agent Tesla can also communicate with its C&C using a Tor client. Forbid the use of the Tor network if it is not crucial to business operations.
- Identify and flag API requests to messaging and CDN services, such as Discord. Such requests are indicative of unusual user behavior.
- Do not allow web browsers to save credentials or other sensitive information.
Endnotes
- https://blogs.infoblox.com/cyber-threat-intelligence/cyber-threat-advisory/cyber-threat-advisory-ukrainian-support-fraud/
- https://attack.mitre.org/techniques/T1055/012/
Appendix (downloadable list here)
| Representative Indicators of Compromise Description | Description |
| supawadee.so@univance[.]co[.]th | From email address |
| REQ : Supplier Survey : Effect of supply chain from the Ukraine/Russa conflict | Email subject |
| REQ Supplier Survey.zip | ZIP attachment file name |
| REQ Supplier Survey.exe | Executable file name |
| 0ea1d24ade8602c0829bd73735ddfcdd6d6dfa12c6370e7cee0c04653a352839 | ZIP file sha256 |
| e4d309967904ca32fa5a00e70161c95621c687e46f2512bac1f061b0303fe863 | Executable file sha256 |
| hXXps://cdn[.]discordapp[.]com/attachments/946667303825735721/948011944776986715/Izcei[.]jpg | Agent Tesla download URL |
| officestore2022@gmail[.]com | Actor’s email address |
| julieta@escueladeseguridadmaritima[.]com | Email address used for exfiltration |
| mail[.]escueladeseguridadmaritima[.]com | Email server used for exfiltration |





