Author: Maël Le Touz
1. Overview
Since the beginning of 2021, Infoblox has been tracking a threat actor, whom we have named PINK BOA. The actor has been highly active throughout this period, but the campaigns have intensified even further over the past several weeks.
PINK BOA uses a dictionary DGA (DDGA) algorithm to generate hostnames at random, and it uses thousands of IPs owned by the U.S.-based hosting provider Digital Ocean and spread out across the world. The results of a scan we performed on public reports suggest that most of the compromised IP addresses have vulnerabilities that can be exploited by remotely executing malicious code.
2. Customer impact
To extend its reach, PINK BOA has translated the email message into Spanish, Italian, German, and other languages. This has allowed the actor to send the message to targets in multiple countries and to keep the overall volume of emails very high.
PINK BOA harvests credentials and other sensitive information by using Agent Tesla,1 Groooboor, Formbook,2 STRRAT,3 Snake Keylogger,4 AveMaria,5 GuLoader,6 and other malware-as-a-service (MaaS) infostealers.
3. Campaign analysis
To lure a target into opening the email, the actor uses the words invoice, quotation, and purchase order in the subject lines. Attached to the emails is an archive that contains either an executable or an infected Microsoft Office file.
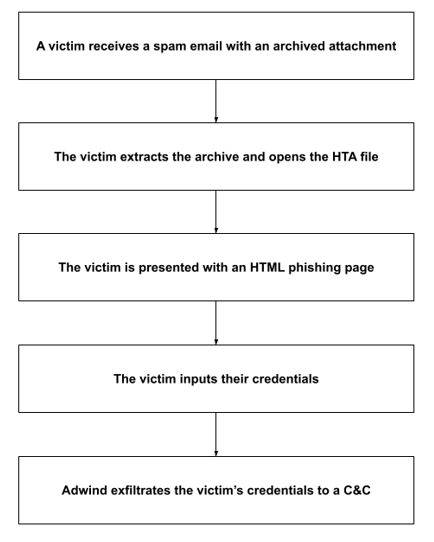
PINK BOA uses phishing templates packaged as HTA archives. On Microsoft Windows machines, these files automatically open in Internet Explorer and attempt to trick the victims into entering their passwords. Each such file is customized to show the recipient’s email address.
4. Attack chain
After the user expands the archive attachment, the file’s code proceeds to exploit an old vulnerability in Office, such as CVE 2017-1182.7
To avoid detection, PINK BOA stores most of its code on a server and downloads it only when the victim interacts with the malware in the attachment.
PINK BOA has a number of distinguishing characteristics:
- Its payload is sometimes hosted on a legitimate website, such as Discord’s content distribution network (CDN) or a Yandex drive.
- It uses IP addresses that have a history of hosting malware.
- In addition to employing various malware and sending them from different IPs, the actor sets the command and control (C&C) server on a per-campaign basis.
- To prevent signature-based antivirus software from detecting the malware, the actor obfuscates the malware payloads with packers or code written in Delphi.
5. Vulnerabilities and mitigation
Infoblox recommends the following actions for reducing the risk of infection by Adwind RAT:
- Regularly train users about phishing and how to handle it appropriately.
- Avoid opening emails from unfamiliar senders, and inspect all attachments before opening them.
- Always be suspicious of vague emails, especially those that contain prompts for opening attachments or clicking links.
- Always be suspicious of unexpected emails, especially those with financial or delivery correspondences, documents, or links.
- Never click URLs in emails from unknown sources.
- Be wary of links in incoming emails. A link in a message sent by a well-known company should point to the company’s domain; for example, if the sender is FedEx, the domain should be http://fedex[.]com. To verify the true destination of a link, pause the cursor over it.
- If clicking a link immediately initiates an attempt to download a file, that file is very suspicious. Do not open it without first inspecting it carefully.
- Before opening an attachment, confirm its legitimacy by contacting the alleged sender via phone or the email address shown on the sender’s website.
- Never enable macros. They are a very common infection vector used by many families of malware.
Endnotes
-
-
- https://blogs.infoblox.com/cyber-threat-intelligence/cyber-campaign-briefs/malspam-delivering-agent-tesla-keylogger-spoofs- oil-gas-co-messages/
- https://blogs.infoblox.com/cyber-threat-intelligence/cyber-campaign-briefs/malspam-rtf-files-drop-formbook-infostealer/
- https://blogs.infoblox.com/cyber-threat-intelligence/cyber-campaign-briefs/transfer-themed-malspam-drops-strrat/
- https://blogs.infoblox.com/cyber-threat-intelligence/cyber-campaign-briefs/snake-keylogger-slithers-through-malspam/
- https://blogs.infoblox.com/cyber-threat-intelligence/cyber-campaign-briefs/polish-language-malspam-campaign-delivers-avemaria-infostealer/
- https://blogs.infoblox.com/cyber-threat-intelligence/cyber-campaign-briefs/guloader-delivers-remcos-rat/
- https://nvd.nist.gov/vuln/detail/CVE-2017-1182
-