Author: Maël Le Touz
1. Overview
Since late August, Infoblox has been tracking a campaign distributing JavaScript malware. The malware’s command and control (C&C) domain, distribution method, and code are consistent with those of FIN7: a group of Russian cybercriminals who are motivated by financial gain and who have been targeting businesses around the world since 2013.
2. Customer impact
This campaign is focused on U.S. companies and English-speaking individuals. FIN7 are known for their aggressiveness, creative use of social media, blackmailing, and threatening to disclose victims’ personal data.1
The behavior of the malware in this campaign matches that of Griffon: a JavaScript malware attributed to FIN7. The behavior is also consistent with the assessment that this malware is used as a first-stage reconnaissance tool and as an installer for future payloads.
3. Campaign analysis
Some emails in this campaign claim to contain bills from Tinder or T-Mobile. Other emails claim to be from the U.S. government and to contain new regulations and vaccination requirements related to Covid-19. The emails are sent a) to large groups rather than specific targets, and b) from a variety of free or inexpensive email providers rather than from a single, attacker-controlled domain.
The relatively low volume of emails we observed since 21 August was interrupted by a large spike from 12 to 15 September. On 14 September, the volume had increased by over 1400 percent.
4. Attack chain
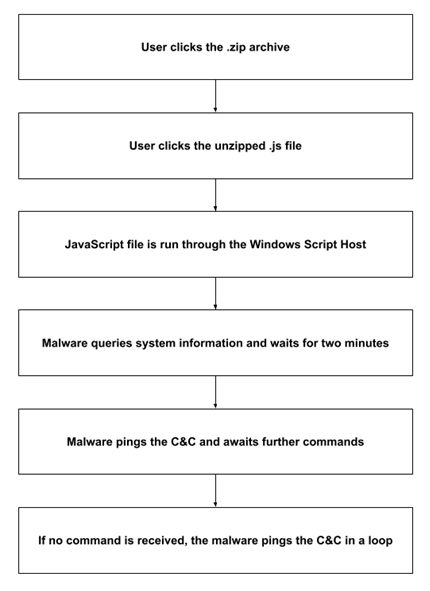
Clicking the email’s attachment decompresses the zip archive and opens a file with a long filename and a double extension, .txt.js, which Microsoft Windows hides by default. If the victim double-clicks the file, Windows Script Host starts running the JavaScript code.
The JavaScript code consists of only 150 lines but is heavily obfuscated. Dynamic analysis revealed that the main purpose of the malware is to reconnoiter the endpoint, send identifying data back to C&C, and set the stage for an offensive operation.
When executed, the malware uses a WMI query to collect the IP address, active network interface, hostname, DNS configuration, and other information about the machine. It waits for two minutes and then sends this data to its C&C on a random URL. If C&C responds, the malware waits for a random period of time then pings C&C again in a loop and waits for its commands. The main loop also prepares a WScript object for receiving and executing future payloads. Public reports suggest that the C&C queries whoami on the local machine and tries to determine whether the user has administrative privileges.
Although JavaScript is mostly platform independent, the malware targets only Windows machines. If the machine is not running Windows, the script fails silently, to suppress its output and avoid detection.
To encrypt communications with its C&C as plain text, the malware uses a custom XOR encryption routine and a random encryption key. The malware chooses URLs for its C&C at random, from a list of defined variables. These URLs end with img, new, or pictures, so they might appear innocuous to unsuspecting targets. The malware also delays its actions frequently, probably to avoid detection and triggering of the antimalware on the victim’s machine.
5. Vulnerabilities and mitigation
Because the malware does not exploit any vulnerabilities but relies on user interaction and default Windows file associations, organizations can follow these recommendations to prevent falling victim to Griffon:
- Disable AutoRun and AutoPlay in Windows.
- Remove .js, .vbs, .hta, .ws, .bat, .ps1, .scr, and other default file associations commonly abused by threat actors. Configure these files such that when double-clicked, they would open in a text editor and would not be executed.
- Do not open attachments that are unexpected or from senders that look unfamiliar.
- Before opening an attachment, check with the alleged legitimate sender whether the file would be safe to open.
- Make sure that user accounts in the organization do not have administrative privileges.