Author: Nathan Toporek
Overview
On 11 August, Infoblox observed an email campaign distributing the STRRAT trojan via weaponized file attachments.
Customer Impact
STRRAT is a Java-based remote access trojan (RAT) that is delivered in malicious email campaigns. Although Java runs on all operating systems, STRRAT is compatible only with Windows hosts. STRRAT can exfiltrate passwords to a command and control server (C&C), run code on infected hosts, enable attackers to control infected hosts directly, and create reverse proxies. In addition, it has a rudimentary ransomware module.1
Campaign Analysis
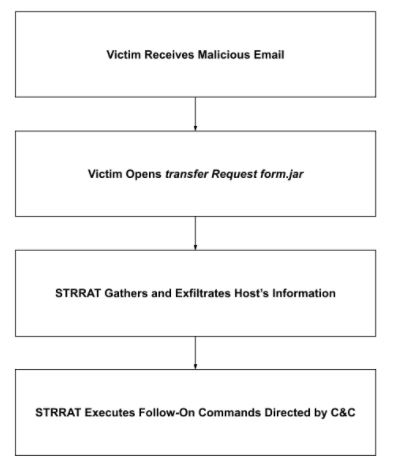
In this campaign, threat actors send victims an email with the subject Re:Transfer Request, no message body, and the file attachment transfer Request form.jar.
Attack Chain
When the victim opens transfer Request form.jar, STRRAT gathers the host’s information, acquires its geolocation, and then sends this information to its C&C. The C&C responds with instruction(s) to run one or more follow-on commands. We observed password exfiltration and remote control; however, there are many more.
Vulnerabilities & Mitigation
This campaign relies on social-engineering tactics to infect computers with STRRAT. Infoblox recommends that users take the following actions to avoid similar infections:
- Regularly train users about phishing emails and how to handle them appropriately.
- Do not open attachments that are unexpected or from unfamiliar senders.
- Do not open attachments with file extensions you do not recognize, and never open files that could be scripts, such as .vbs, .cmd, and .bat.
Endnotes
- 1. “New Java STRRAT ships with .crimson ransomware module | G DATA.” https://www.gdatasoftware.com/blog/strrat-crimson. Accessed 16 Aug. 2021.