Author: Yadu Nadh
Overview
On 3 August, Infoblox observed a malicious malspam campaign distributing Oski Stealer, which is best known as a credential stealer, although it also has other capabilities. According to Cisco Talos, Oski Stealer shares code (thus traits) with Vidar and Arkei Stealer.
Customer Impact
The malware, which can be purchased from underground forums for $70–$100,2 targets businesses and individuals in the U.S. and China3 but has not infected machines in the Commonwealth of Independent States (CIS).
Oski Stealer has been distributed via emails that contain a variety of lures and phishing themes, and it comes with an array of features, such as those that allow a threat actor to take screenshots and steal the following from an infected machine:
- login credentials from applications
- cookies, autofill data, credit cards, and other information stored by web browsers
- cryptocurrency wallets
- system information
Oski Stealer can also function as a downloader and can execute other malware. It can evade anti-malware products and make itself hard to detect by obfuscating (1) the strings it used to store the function names and (2) the paths it embedded in the binary and decrypted during runtime.
Campaign Analysis
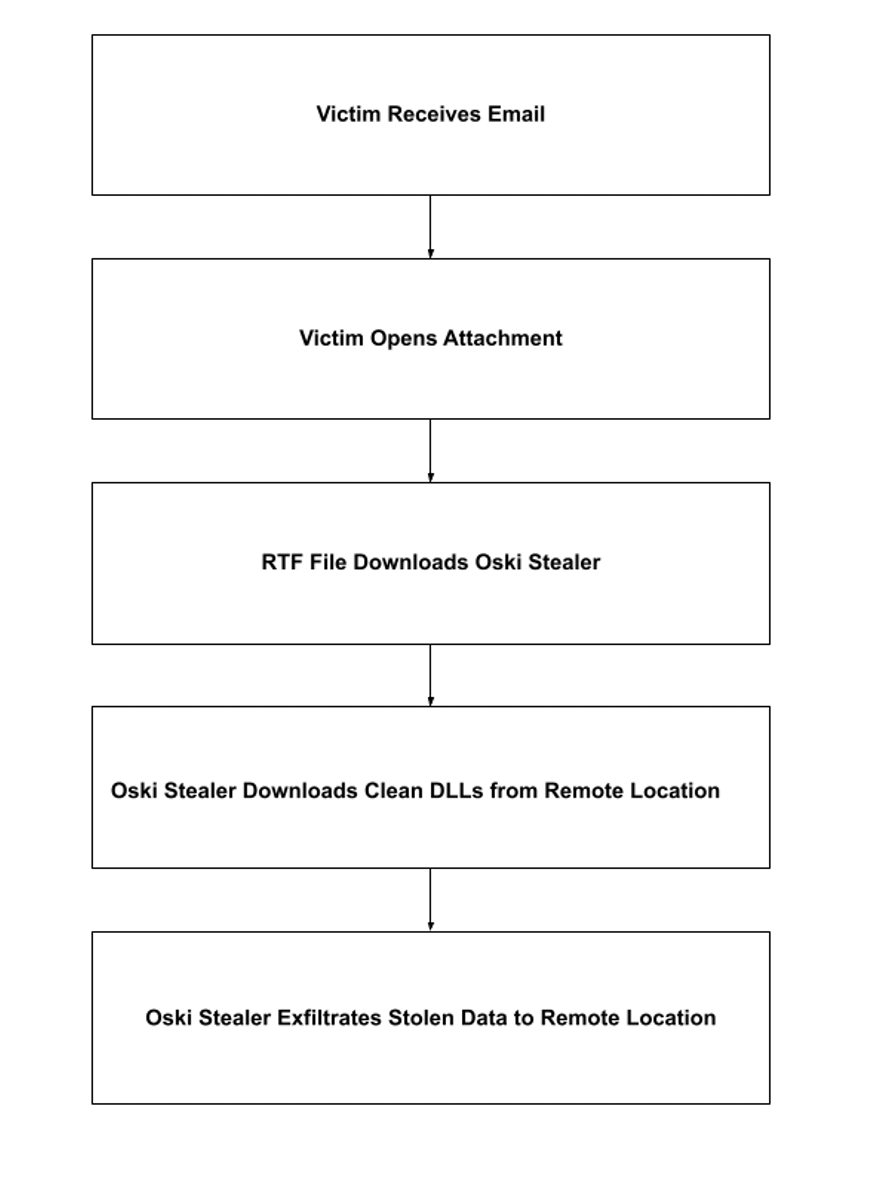
This malspam campaign uses a Swift payment theme to lure victims. The email has the subject 回复: Payments, an empty body, and an attachment that is a Microsoft RTF file swift_message_723-18-22-78_2-8-2021.doc.
Attack Chain
Once opened, the RTF file executes an embedded Windows PowerShell script that contains the instruction powershell.exe” -NoP -sta -NonI -W Hidden…, which silently (1) downloads a .NET binary and (2) executes it.
Oski Stealer then contacts a remote server, downloads seven clean dynamic link libraries (DLLs), and stores them together in C:\ProgramData. It creates C:\ProgramData\755173102468318 to store all the information it steals.
After capturing and storing the victim’s information, Oski Stealer compresses the stolen data into a ZIP file, exfiltrates it to its server, and deletes the stolen information from the victim’s machine by running cmd.exe” /c taskkill /pid 3860 & erase C:\Users\admin\AppData\Roaming\texts.exe & RD /S /Q C:\\ProgramData\\755173102468318\\* & exit.
Vulnerabilities & Mitigation
Malspam email campaigns are a common distribution method for malware. Infoblox recommends that users take the following precautions to reduce the possibility of an infection:
- Always be suspicious of emails that contain documents and links, especially emails that contain delivery instructions or text about financial topics.
- Avoid opening emails with generic subject lines.
- Many malware families use macros as part of the attack chain. Do not enable macros in Microsoft Office attachments, especially macros whose only apparent contents are directions for enabling the macros. Never configure Microsoft Office to enable macros by default.
- Before opening an attachment that seems to have come from a legitimate source, check whether the alleged source really sent that email.
Endnotes
- https://blog.talosintelligence.com/2020/09/threat-roundup-0911-0918.html
- https://www.cyberark.com/resources/threat-research-blog/meet-oski-stealer-an-in-depth-analysis-of-the-popular-credential-stealer
- https://threatpost.com/oski-data-stealing-malware-north-america-china/151856/








