Author: Yadu Nadh
TLP: WHITE
Overview
On 10 May, Infoblox observed a malicious email campaign that used weaponized Microsoft Excel spreadsheets (XLS) that exploited CVE-2017-118821 to deliver BitRAT, a remote access trojan (RAT).
Customer Impact
BitRAT, first observed in late 2020, is a newcomer to the malware scene. Poor coding practices found within the malware signal inexperience from the developers, as large sections of the code appear to be copied and pasted from another trojan called TinyNuke, as well as from a variety of open source projects.2
Threat actors can purchase this malware on popular underground forums and have been observed distributing it via malicious XLS attachments in malspam.
BitRAT’s known capabilities include:
- SSL encryption,
- Cryptocurrency mining,
- Activating webcams,
- Keylogging,
- Downloading/uploading files,
- Controlling the victim’s machine remotely, and
- Communicating via TOR.3
Campaign Analysis
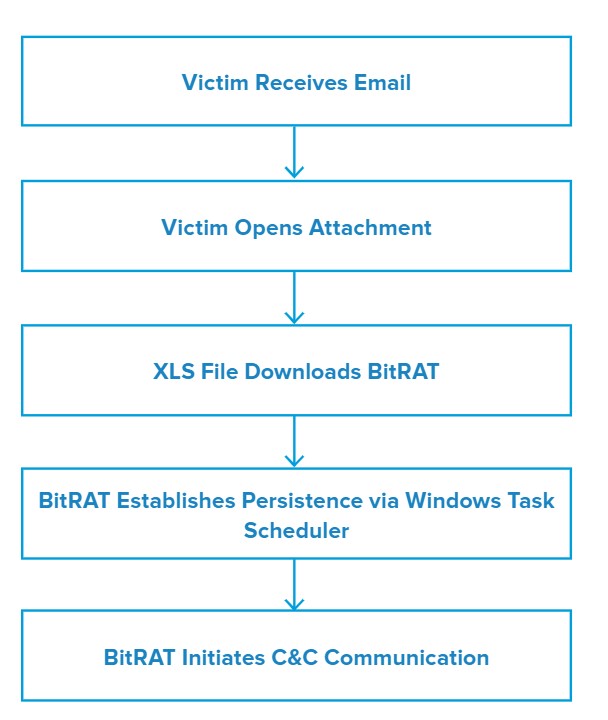
In this campaign, threat actors used a biotechnology theme with the subject line new deal for Biotechnologyinc-CN#324708. The emails contained a message body referencing a “new deal” to lure unsuspecting users to download and open the attachment, named Biotechnologyinc-CN#324708.xlsx.
Attack Chain
Once the victim opens the attached XLS sheet, the file exploits CVE-2017-11882, a memory corruption vulnerability in Microsoft Office’s Equation Editor.
The file then downloads and executes the payload from hxxp://maqboolimpex[.]co/a1/C3b[.]exe. The downloaded binary in this case is a .NET crypter containing BitRAT as its payload.
On execution, the binary establishes persistence via Windows Task Scheduler, and proceeds to initiate communication with its command and control (C&C). Once it establishes C&C communication, BitRAT begins its post-infection activity.
Vulnerabilities & Mitigation
Malspam email campaigns are a common distribution method for malware. Infoblox therefore recommends the following precautions to reduce the possibility of infection:
- Always be suspicious of unexpected emails, especially regarding financial or delivery correspondence, documents, or links.
- Exercise caution if it is necessary to open emails with generic subject lines.
- Do not enable macros in Microsoft Office attachments, especially if the file’s only apparent contents are directions to enable macros.
- Never configure Microsoft Office to enable macros by default. Many malware families use macros as an infection vector.
- Verify important or potentially legitimate attachments with the sender via alternative means (e.g., by phone or in person) before opening them.
Endnotes
- https://nvd.nist.gov/vuln/detail/CVE-2017-11882
- https://krabsonsecurity.com/2020/08/22/bitrat-the-latest-in-copy-pasted-malware-by-incompetent-developers/
- https://research.checkpoint.com/2021/apomacrosploit-apocalyptical-fud-race/









