Author: Eric Patterson
TLP: WHITE
Overview
Between 25 and 30 April, Infoblox observed a malspam campaign distributing the AveMaria remote access trojan (RAT). Threat actors used email subject lines written in Polish referencing payment confirmations to lure victims into downloading a malicious executable.
Infoblox has previously reported on AveMaria in April 2019 and December 2020.1,2
Customer Impact
First reported in early 2019 by security firm Yoroi, AveMaria is an infostealer that threat actors deliver via document attachments in malicious spam campaigns.3
AveMaria is a modular RAT that allows its authors to customize its functionality as needed depending on the objectives of the campaign. However, its core functionality allows it to harvest credentials for installed email clients (e.g. Outlook), decrypt stored credentials in FireFox and transmit other sensitive information back to a command and control (C&C) server.
Campaign Analysis
The threat actors behind this campaign are likely targeting Polish speaking countries and individuals, based on the primary language in the emails. The subject lures and attachments for this campaign, which are financially themed, are: Ponowne potwierdzenie płatności and Permintaan pesanan.exe. They translate from Polish to “Re: Payment Confirmation” and “Order Request.exe” respectively.
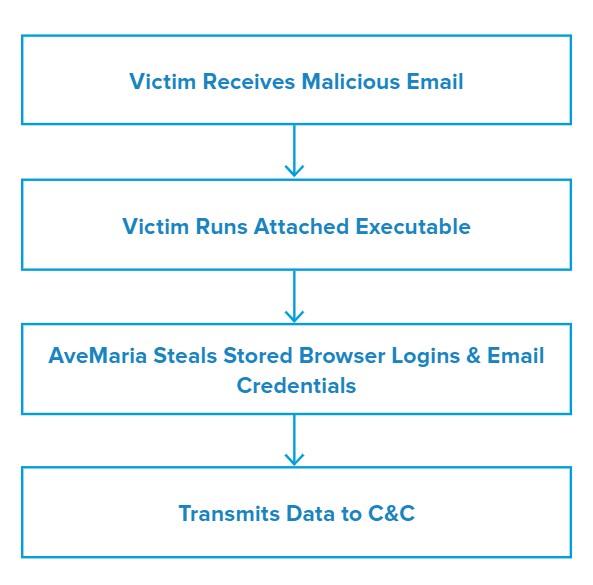
Attack Chain
When the victim downloads and opens the attached executable, the malware performs a series of generic actions like capturing system information, copying the contents of the clipboard and taking screen captures.
AveMaria then attempts to download stored credentials from Google Chrome and Mozilla Firefox, as well as checks for the presence of Microsoft Outlook. It also attempts to steal email-related usernames and passwords.
AveMari transmits the information it acquires to its C&C server over a non-standard port.
Vulnerabilities & Mitigation
Malicious spam attachments that exploit a known vulnerability are the primary infection vectors for AveMaria. Infoblox recommends the following actions to reduce the risk of this type of infection:
- Keep computers and all endpoints up-to-date with the latest security patches to block known vulnerabilities that threat actors could target.
- Be cautious of emails from unfamiliar senders and inspect unexpected attachments before opening them.
- Always be suspicious of vague or empty emails, especially if there is a prompt to open an attachment or click on a link.
- Implement attachment filtering to reduce the likelihood of malicious content reaching a user’s workstation.
Endnotes
- https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–11
- https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–97
- https://yoroi.company/research/the-ave_maria-malware/








