Author: Nathan Toporek
TLP: WHITE
Overview
On 25 April, Infoblox observed a phishing campaign that used a DocuSign lure and a malicious file attachment to infect victims with the Trickbot banking trojan. Although Microsoft and other organizations disrupted the Trickbot botnet in October 2020,1 multiple sources have seen activity from the botnet since then.2
We have published several reports on Trickbot, including a Malicious Activity Report (MAR)3 and Cyber Campaign Briefs (CCBs).4,5
Customer Impact
Trickbot was first discovered in 2016 and has since grown in popularity.6,7,8 Trickbot infects victims, steals sensitive financial information and exfiltrates it to its command and control (C&C) server. It can also move laterally within a network by brute-forcing Remote Desktop Protocol (RDP) credentials.
Threat actors favor Trickbot due to its modular nature, which facilitates customization and provides attackers the capability to drop additional malware on infected systems.
Campaign Analysis
In this campaign, threat actors sent emails with a subject line of “Please Docusign.” and a malicious Microsoft Excel Spreadsheet file attachment. Messages prompted the victim to open the file attachment to start the signing process.
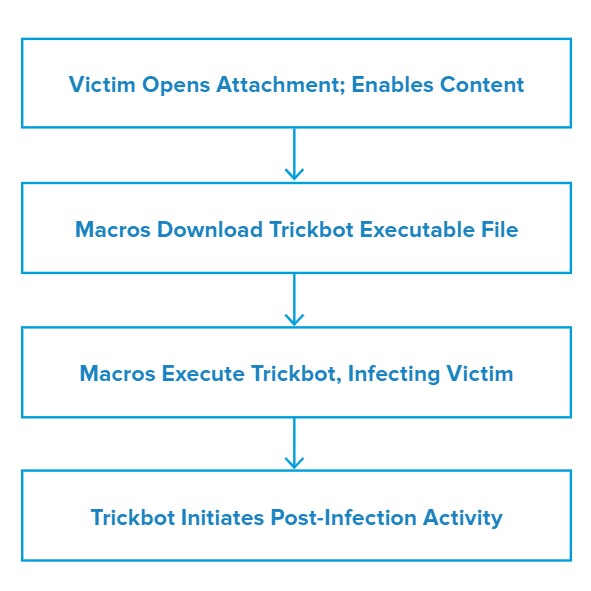
Attack Chain
When the victim opens the file attachment, it presents an image claiming the document is encrypted and that they must enable content to decrypt it. Notably, this image contains the McAfee logo, which may increase the likelihood that the victim will trust the document and enable malicious content.
Once enabled, macros will download and run the Trickbot executable file, infecting the victim.
Vulnerabilities & Mitigation
This campaign relies on social engineering tactics to lure victims into opening a malicious file attachment and executing its macros. As such, Infoblox recommends taking the following precautions to reduce the likelihood of such an attack succeeding:
- Verify important or potentially legitimate attachments with the sender via alternative means (e.g., by phone or in person) before opening them.
- Be cautious of emails from unfamiliar senders and inspect unexpected attachments before opening them.
- Always be suspicious of vague emails, especially if there is a prompt to open an attachment or click on a link.
- Do not enable macros in a Microsoft Office attachment, especially if the file’s only apparent contents are directions to enable macros.
- Regularly train users about potential phishes and how to handle them appropriately.
Endnotes
- https://blogs.microsoft.com/on-the-issues/2020/10/12/trickbot-ransomware-cyberthreat-us-elections/
- https://www.cyberscoop.com/trickbot-status-microsoft-cyber-command-takedown/
- https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–111
- https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–77
- https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–66
- https://blog.malwarebytes.com/detections/trojan-trickbot/
- https://www.fidelissecurity.com/threatgeek/archive/trickbot-we-missed-you-dyre/
- https://blog.malwarebytes.com/threat-analysis/2016/10/trick-bot-dyrezas-successor/








