Many organizations commonly provide content filtering that uses transparent proxies for devices – they don’t own – but that are on their networks. Transparent proxies commonly use SNI data to understand whether a user is accessing inappropriate data, so if the SNI field is encrypted, it will disrupt the use of transparent proxies.
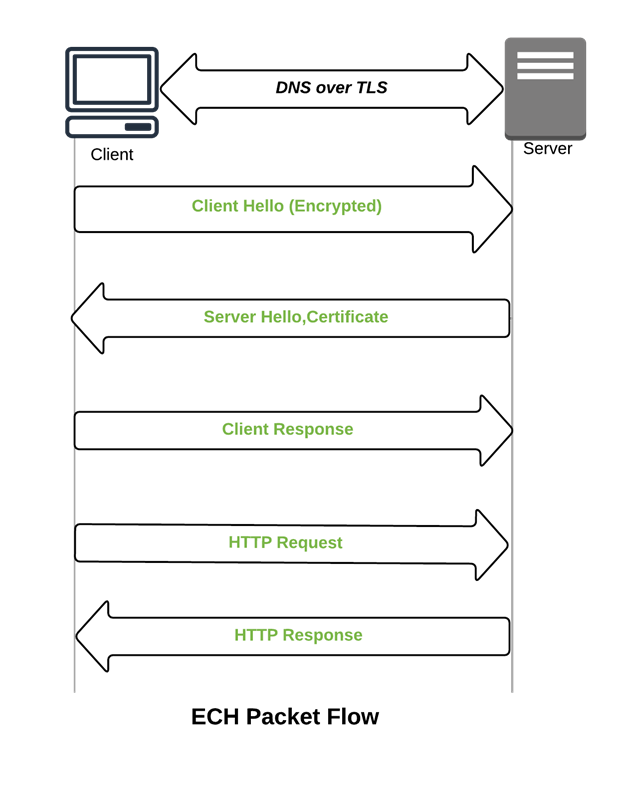
Encrypted server name indication (ESNI) is a security feature that is used for keeping user data private while browsing. This feature prevents TLS from leaking any data by encrypting all of the messages, including the initial Client Hello message. This ensures no snooping on the TLS handshake information (such as domain) by third parties. It also helps prevent data on the server certificate presented by the server. ESNI encrypts the server name indication (SNI) field of the TLS handshake. Encrypted Client Hello (ECH) came into the picture to overcome the shortcomings of ESNI. Encrypted Client Hello (ECH) no longer encrypts the SNI extension but instead encrypts an entire Client Hello message. This resulted in the name change from “ESNI” to “ECH”.
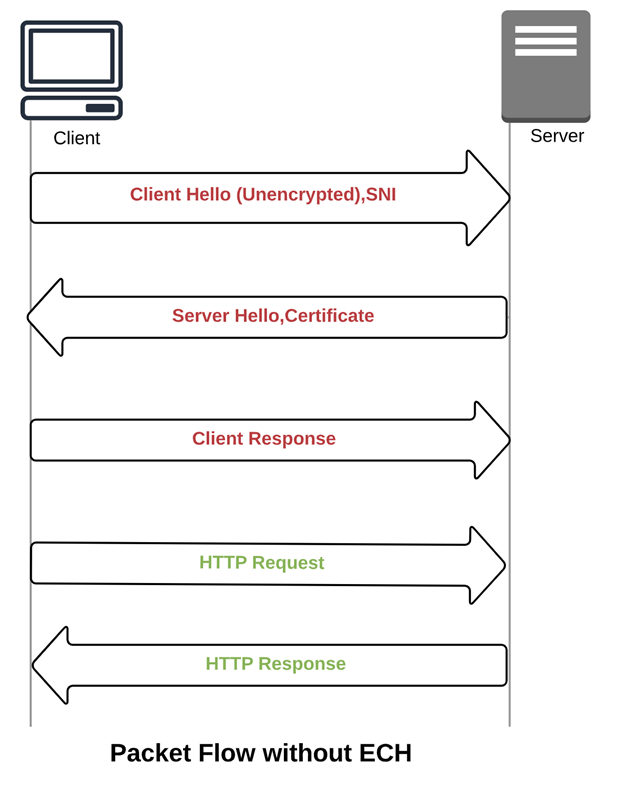
As an example – a user XYZ wants to visit a website, www.example-website.com. This is a TLS based website, which means the traffic is encrypted. In addition, it also uses ESNI to protect the initial Client Hello information.
Here is a high-level exchange that occurs when a user tries to access a website with ESNI:
- XYZ user sends a query to a DNS server to find out the www.example-website.com IP address.
- The DNS response tells the XYZ user what is the IP address of the website with the website’s ESNI public key.
- XYZ now sends an encrypted Client Hello using the website’s ESNI public key.
- The Website server verifies the information and the certificate.
- After this, the normal TLS handshake completes, and the user is able to access the website. This prevents any attackers from monitoring what website is being accessed by the user.
 Key Impact
Key Impact
DNS is an important piece for multiple services like Proxy’s, VPN, web traffic etc. and changing anything related to the DNS can break the functionality of these things. With ECH/ESNI, we would see an impact on the user experience, because a lot of changes are needed (application specific/DNS configuration).
Presently, the majority of devices use their ISP’s DNS capabilities. DoH could drive a shift from ISP/single device DNS settings to each application being able to select their own DNS provider. With ECH, customers may need to set-up content filtering on a per device/application basis, risking inconsistent experiences.
DNS Filtering
DNS filtering provides some capabilities to augment SNI-based filtering. Filtering is an important tool which leverages DNS information to stop accidental access to malicious content (e.g. Phishing/Malware sites). Most of the organizations use transparent proxies that are often combined with DNS filtering, to safeguard users against malicious content. However, the proxy requires unencrypted SNI to check the domain information. Using ECH will hamper this function.
With Infoblox, we can provide a content filtering solution that is scalable and cost effective. It also provides the ability to dynamically identify users and apply policy decisions in near real-time.
DNS-level traffic inspection can provide stable, scalable augmentation for SWGs (Secure Web Gateways). For example, through the Infoblox product, a provider can prevent users from accessing obviously inappropriate content, by blocking traffic at the DNS level.
Infoblox offers differentiated functionality, such as Threat Insight, which can detect malware commands and control traffic hidden in DNS queries. It can also detect the presence of DNS tunneling, a common method that some students can potentially use to bypass SWG security policy limitations.
In addition to this, Infoblox provides Subscriber Policy Enforcement and Subscriber Parental Control. Infoblox solutions can scale exponentially, support HTTPS traffic, provide license flexibility and a minimal hardware footprint which makes us a complete solution to counter the challenges posed by ECH/ESNI.
Helpful Links
https://blogs.infoblox.com/security/infoblox-walled-garden-web-filtering/







