Author: Victor Sandin
TLP: WHITE
Overview
On 15 February, Infoblox observed a malicious email campaign distributing a remote access trojan (RAT) known as RuRAT, via an encrypted Microsoft Excel spreadsheet (XLS) with malicious macros. In this campaign, threat actor(s) used an email subject referencing a fraudulent card invoice to lure users into opening the malicious attachment for details.
Customer Impact
RuRAT is a trojan that contains a legitimate remote desktop software developed by a company called Remote Utilities.1 The software allows the user to control another computer through a proprietary protocol. In 2018, threat actor(s) abused this software in another malspam campaign targeting industrial systems.2 Remote Utilities’ agent is capable of bypassing UAC controls, creating RDP sessions over the Internet, exfiltrating files, observing the host’s desktop and installing/uninstalling software.3
Campaign Analysis
In this campaign, the threat actor(s) used the subject line invoice_Videoflare Ltd and attached an encrypted XLS file (invoice_Videoflare_Ltd.xls). The emails contained a brief description of a card invoice to lure the victim into opening the “complete version” in the attached file. The email body also included the password to access the locked XLS file.
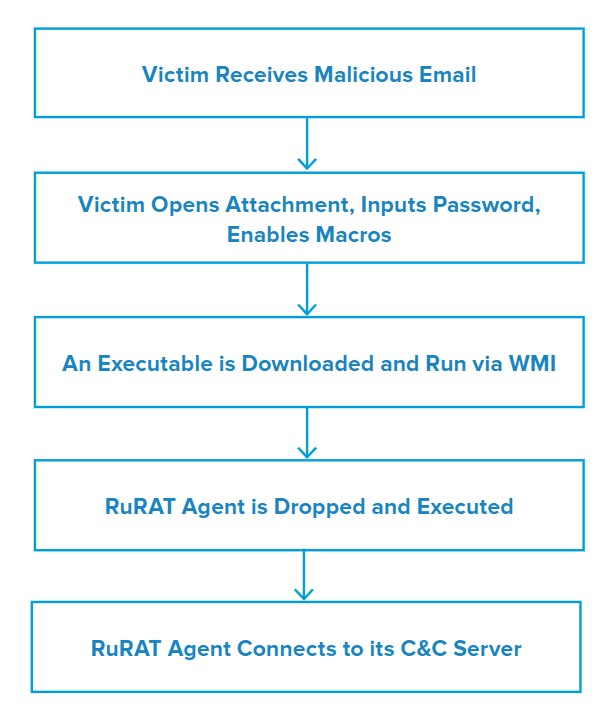
Attack Chain
When the user opens the XLS file, inputs the password included in the email and enables macros, Excel runs a VBA macro that downloads an executable from the threat actor’s server to the user directory. The macro then launches the executable that prompts RuRAT to be installed.
Vulnerabilities & Mitigation
Infoblox recommends the following to reduce the risk of this type of infection:
- Be cautious of emails from unfamiliar senders and verify important or legitimate attachments with sender via alternative means (e.g. by phone or in person) before opening them.
- Pay special attention to emails with financial or delivery themes which lure users into opening their attachment for full details.
- Configure Microsoft Office to disable macros by default and be cautious if the file’s only apparent contents are directions to enable macros.
- Implement rules to block encrypted files or unexpected file formats to reduce the likelihood of malicious content reaching the users.
- Increase security awareness within staff members by providing courses to train them on how to identify and handle phishing campaigns.
- Limit users’ privileges to only those needed for performing their tasks, especially forbid software installations rights.
Endnotes
- https://www.remoteutilities.com/
- https://securelist.com/attacks-on-industrial-enterprises-using-rms-and-teamviewer-new-data/99206/
- https://www.remoteutilities.com/product/features/remote-access.php





