Author: Nathan Toporek
TLP: WHITE
Overview
On 22 January, Infoblox observed a large malspam campaign targeting Italian speakers and delivering Emotet malware. This campaign delivered emails containing malicious, password-protected ZIP archives with a Microsoft Word document that infects victims when opened.
Infoblox has written several reports on malspam campaigns targeting Italian-speaking users with various malware.1, 2, 3 We have also reported on previous Emotet campaigns that have used English-language political and holiday-themed email lures.4, 5, 6
Customer Impact
Emotet is a notorious banking trojan and infostealer that was first observed in 2014.7Emotet can steal banking data and passwords from a victim’s computer, as well as download and install additional malware such as Trickbot or Qakbot.8
Once it downloads additional malware, it can spread laterally across a network by sending malicious emails to contacts of the infected victim, carrying out brute force attacks, and using Trickbot to launch exploits such as EternalBlue.9
Campaign Analysis
In this campaign, threat actors sent emails written in Italian, with message bodies requesting the victim open the file attachment. The threat actors used hundreds of unique subject lines and message bodies; however, generally speaking, they all either referred to prior discussions or urged the victim to open the file.
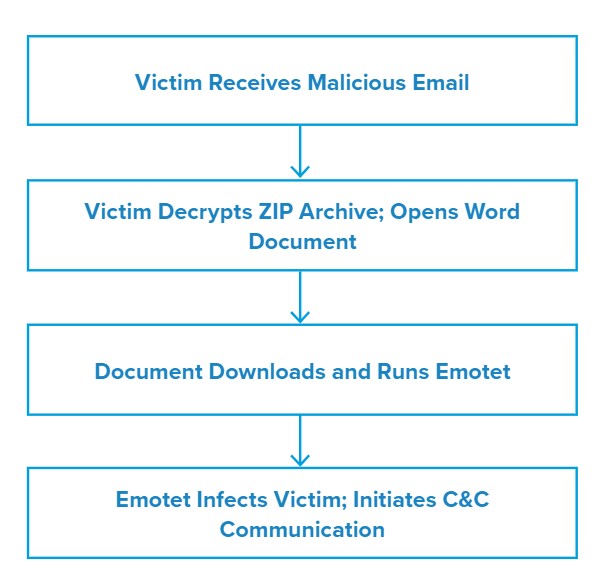
Attack Chain
In the emails, threat actors attached a password-protected ZIP archive containing a malicious Word document and specified the password in the message body. When the victim decrypts the archive and opens the Word document, they will be prompted to enable macros. When the victim complies, the Word document contacts various URLs to download and infect them with Emotet malware.
Vulnerabilities & Mitigation
This campaign relies on social engineering tactics to lure victims into downloading malicious attachments. As such, Infoblox recommends taking the following precautions to reduce the likelihood of such an attack succeeding:
- Be cautious of emails from unfamiliar senders and inspect unexpected attachments before opening them.
- Always be suspicious of vague emails, especially if there is a prompt to open an attachment or click on a link.
- Do not enable macros in a Microsoft Office attachment, especially if the file’s only apparent contents are directions to enable macros.
- Regularly train users about potential phishes and how to handle them appropriately.
Endnotes
- “Ursnif Banking Trojan Targets Germany and Italy – 20200129.” https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–56. Accessed 26 Jan. 2021.
- “Maze Ransomware Campaign – 20191105 – Infoblox.” https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–46. Accessed 26 Jan. 2021.
- “FTCODE Ransomware Target Victims In Italy – Infoblox.” https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–44. Accessed 26 Jan. 2021.
- “How Emotet Stole Christmas – 20200107 – Infoblox.” https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–53. Accessed 26 Jan. 2021.
- “Emotet Gets Political – 20201028 – Infoblox.” https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–90. Accessed 26 Jan. 2021.
- “Valyria Trojan Drops Emotet – 20210112 – Infoblox.” https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–101. Accessed 26 Jan. 2021.
- https://www.malwarebytes.com/emotet/
- https://www.proofpoint.com/us/threat-insight/post/threat-actor-profile-ta542-banker-malware-distribution-service
- https://securityboulevard.com/2019/10/a-closer-look-at-the-emotet-banking-trojan/









