AWS Interface Endpoints can be used to access services provided through AWS PrivateLink. The supported services can include some native AWS services, services hosted by other AWS customers, and supported AWS Marketplace Partner Services. PrivateLink allows your VMs and applications to connect to these services using a private IP address, keeping all traffic within AWS networks and off the public Internet.
When these interface endpoints are created, AWS creates a unique DNS hostname and record for the endpoint. Additionally, if you enable the private DNS option for an endpoint, AWS associates a private hosted zone with your VPC that contains record sets for the default name of the service, for example ec2.us-west-1.amazonaws.com which will resolve to the interface endpoint when using the default Route 53 resolver in that VPC. However, this only works for VMs or other clients deployed into the same VPC where the interface endpoint lives, and only if you are using the default DNS resolver.
In this post, we’ll look at two scenarios where you can benefit from using Infoblox NIOS and AWS Route 53 Resolver Inbound Endpoints to resolve these PrivateLink Interface Endpoint services.
Resolving Interface Endpoints from On-Premises Networks
For this example, we’ll use an interface endpoint in a VPC, providing access to the AWS EC2 service with a default name of ec2.us-west-1.amazonaws.com. We want on-premises clients to connect using this endpoint for access to EC2 services. Consider the diagram below, showing the path of a DNS request for this endpoint.
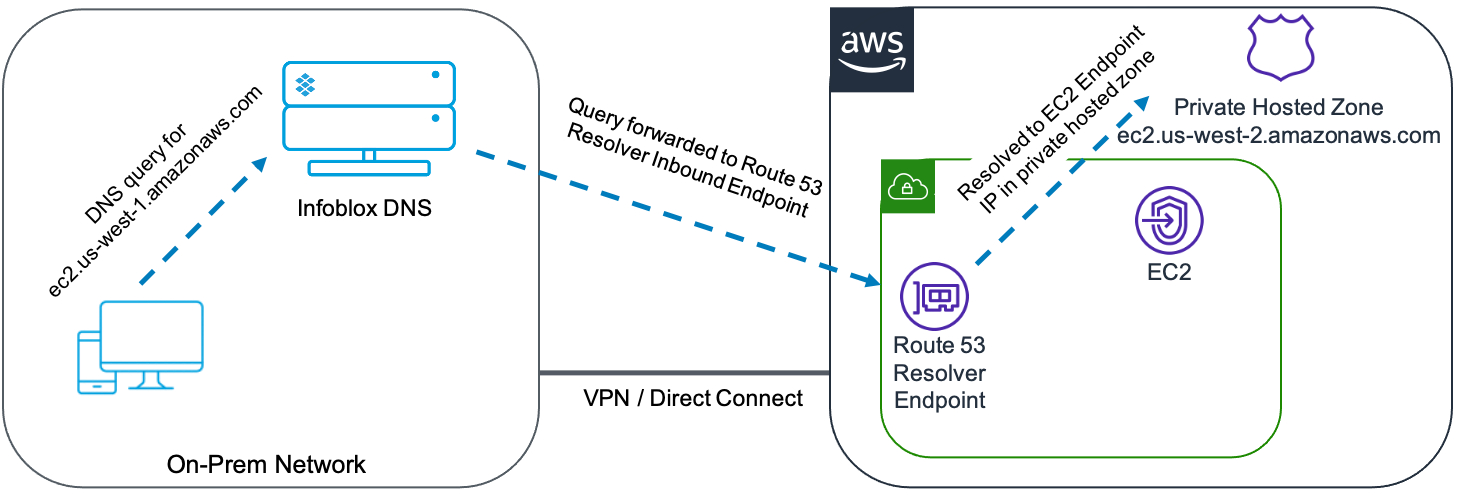
- Client queries Infoblox DNS for ec2.us-west-1.amazonaws.com.
- Infoblox DNS forwards query to Route 53 Resolver inbound endpoint in VPC via VPN or AWS Direct Connect.
- The inbound endpoint uses Route 53 Resolver to resolve query to private hosted zone associated with the VPC.
Infoblox NIOS as Primary Name Server in VPCs
For this example, we’ll again use an interface endpoint in a VPC, providing access to the AWS EC2 service with a default name of ec2.us-west-1.amazonaws.com. In this case, we want to use Infoblox vNIOS deployed in AWS as primary DNS for our VPCs, to allow for centralized DNS management and gain benefits provided by Infoblox DNS such as response policy zones, query logging, and many other security and management features. The diagram below depicts the path for DNS requests for this endpoint. Please note that the Infoblox DNS server does not need to be in the same VPC as the interface endpoints; it is pictured that way here for simplicity and as one possible solution.
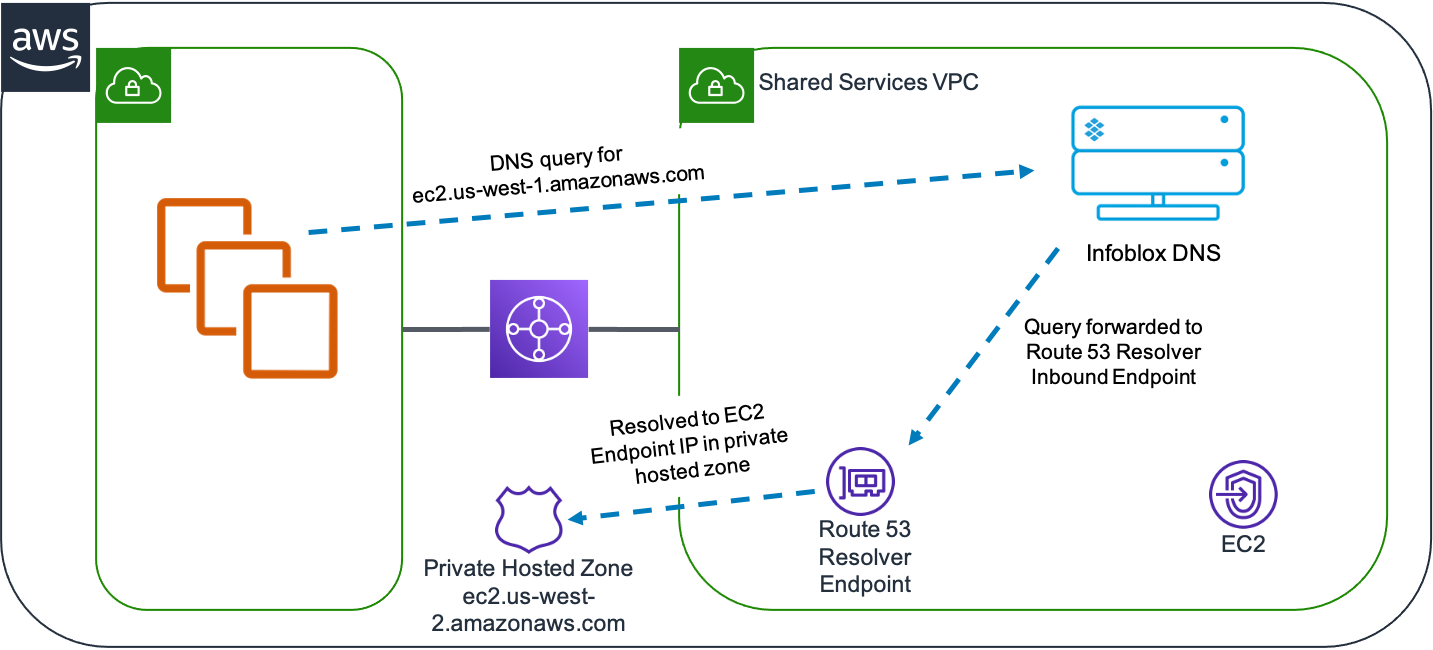
- Infoblox vNIOS instance set as primary name server for VPCs
- EC2 instance or other client queries Infoblox DNS for ec2.us-west-1.amazonaws.com via Transit Gateway or VPC peering.
- Infoblox DNS forwards query to Route 53 Resolver inbound endpoint.
- The inbound endpoint uses Route 53 Resolver to resolve query to private hosted zone associated with the VPC.
Implementation
Infoblox NIOS or vNIOS appliances should be deployed and configured either on-prem or in an AWS VPC using Infoblox best practices. Refer to Infoblox deployment guides at https://infoblox.com/resources for details on deployment and configuration. AWS Interface Endpoints and Route 53 Resolver Endpoints should be deployed using AWS best practices. For details on deploying required AWS resources, refer to AWS documentation at https://docs.aws.amazon.com/.
Once your Infoblox name server and AWS resources are configured according to one of the diagrams above, or a combination of the two if you will use Infoblox for DNS resolution on-premises and in your VPCs, the final configuration consists of setting up DNS conditional forwarding for the appropriate zone.
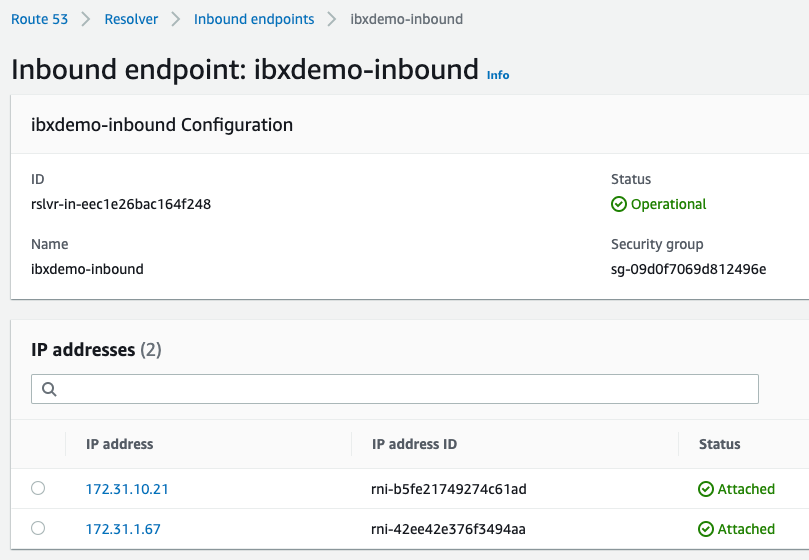
In the AWS Management Console, find the IP address(es) for your Route 53 Resolver inbound endpoint on the Route 53 > Resolver > Inbound endpoints detail page for your endpoint.
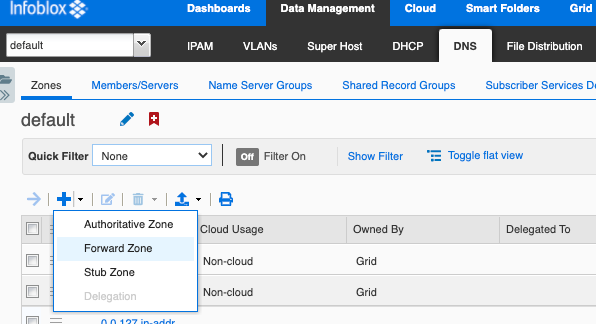
Next, log into your Infoblox Grid Manager and navigate to the Data Management > DNS > Zones tab. Expand the Add dropdown and select Forward Zone.
On step 1 of the Add Forward Zone Wizard, select Add a forward forward-mapping zone.
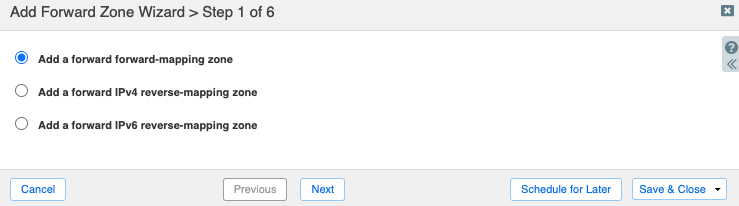
On step 2, enter the name of the zone for forwarding, in this case ec2.us-west-1.amazonaws.com. If you will be using interface endpoints for other AWS services in this region, you could instead use us-west-1.amazonaws.com to forward to Route 53 Resolver for all of these services.
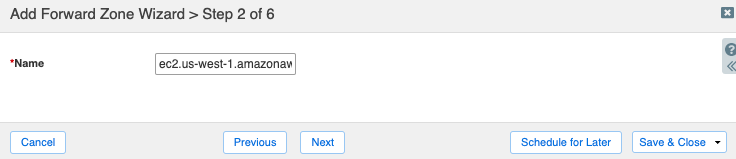
On step 3, select Use this set of name servers. Use the Add button to add your Route 53 Resolver endpoint as the name servers. Add as many of the available IPs for your Route 53 endpoint as desired to scale availability and capacity.
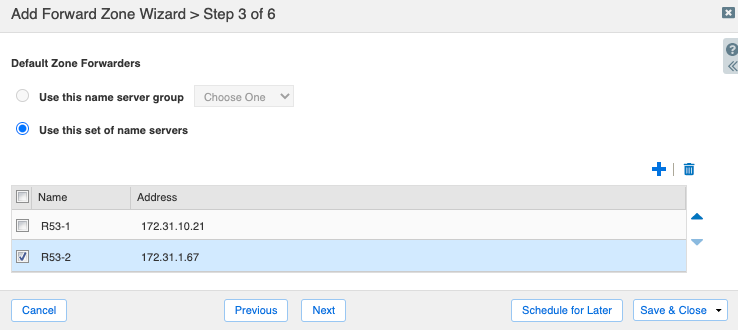
On step 4, select Use this set of name servers. Use the Add button to add Infoblox name servers that will serve this forward zone. Please note that for forwarding to work, the name servers must have recursion enabled.
Save and Close the wizard. Restart the DNS service for Infoblox members when prompted.
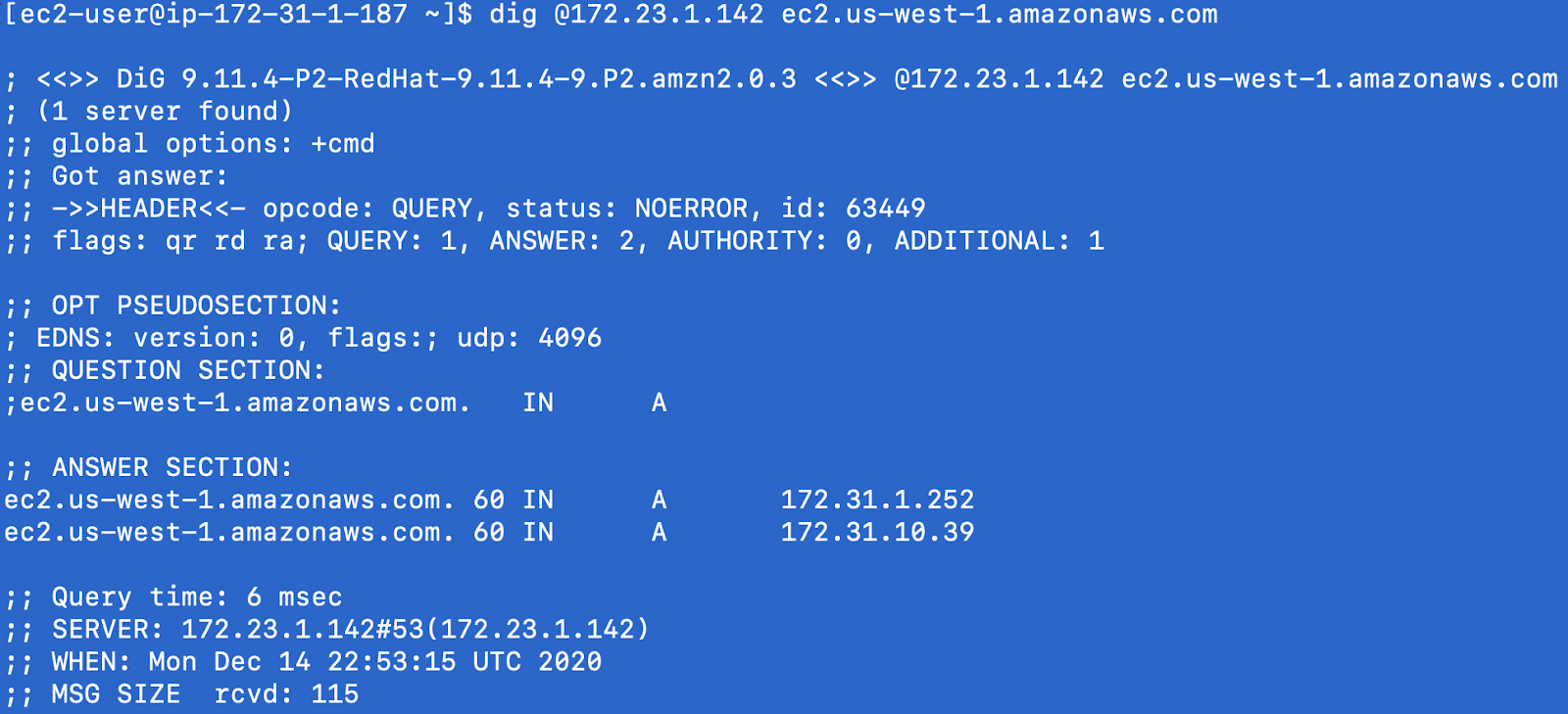
To test the configuration, use Dig or other tools to resolve for ec2.us-west-1.amazonaws.com. Notice the private IP addresses returned in this screenshot.
Conclusion
Using DNS forward zones and Route 53 Resolver Inbound Endpoints, you can resolve AWS PrivateLink Interface Endpoints from anywhere, gaining all the advantages of Infoblox solutions and AWS private networking. Combine the use cases shown in this post for resolution across your hybrid and multi-cloud environments.










