The MITRE ATT&CK framework is being widely adopted by the cybersecurity industry because it provides a common language to communicate different methods by which threat actors (adversaries) can launch real-world cyberattacks, and how they can bypass your defenses to accomplish their mission. In this blog, we going to describe the primary ways MITRE ATT&CK data is being used by the cybersecurity professionals to identify gaps and strengthen defenses.
Before we proceed, let’s step back and take a moment to understand what is the MITRE ATT&CK framework and how it can be used to deconstruct various types of cyberattacks.
What is MITRE ATT&CK?
MITRE ATT&CK is a globally accessible knowledge base of tactics and techniques used by adversaries to launch cyberattacks. MITRE is a government funded research organization that started the project of gathering and curating real-world attack scenarios back in 2013. ATT&CK stands for Adversarial Tactics, Techniques, and Common Knowledge, which is growing repository of attacks openly shared with government, education and commercial organizations.
Tactics and techniques are a new way of representing the taxonomy of cyberattacks. Instead of looking at the results of a cyberattack after it is successful as Indicators of Compromise (IoCs), security analysts can use tactics and techniques to see how an attack is propagated as it is in progress. Tactics represents the “why” of the attack, techniques represent “how” the adversary achieves the tactical objective, and CK is the documented use of tactics and techniques by adversaries.
Understanding MITRE ATT&CK Matrices
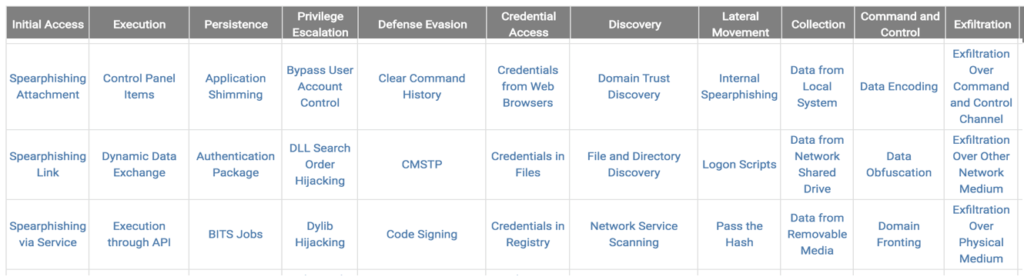
The MITRE ATT&CK matrix organizes all known attack tactics and techniques into an easy to understand format, with the 11 different tactics that represent the different stages of the attack across the top. Multiple techniques to accomplish each tactic is listed down each column. A successful cyberattack sequence is built from moving from the leftmost column (Initial Access) to the rightmost column (Exfiltration).
As shown in the Table snippet above taken from the Enterprise MITRE ATT&CK matrix, it lists 3 different techniques of launching a Spearphishing attack – via malicious file attachment, malicious link, and rogue service. The rest of the table is a comprehensive list of techniques for launching various cyberattacks in the enterprise. MITRE also has curated lists for attacks on mobile devices, industrial control systems, and pre-attack sequences that are steps taken by adversaries before an attack is launched.
Primary Applications of the MITRE ATT&CK Framework
Beyond offering a common language for describing cyberattacks, the ATT&CK framework is being used by cybersecurity professionals for testing adversarial behavior and strength of cyber defenses in the following ways.
- Breach and Attack Simulation: it can be used to simulate attack scenarios and validate your security controls against the behavior of well-known attacks.
- Red and Blue Teaming: it can be used by red teams to model real-world attacks using penetration testing. Blue teams can improve defensive measures to block such attacks.
- SOC Maturity Assessment: it can be used to determine how effective your security operations center (SOC) is at detecting, analyzing and responding to incidents.
- Threat Intelligence Enrichment: it can be used to enrich threat intelligence data by understanding adversary group profiles and their behaviors.
- Vendor Analysis: Vendor products widely vary in their effectiveness. ATT&CK provides ways to compare product capabilities to address common threats and objectively determine which vendor better meets your needs.
MITRE ATT&CK provides a powerful open-source tool that enables you to classify tactics and techniques of various well known cyberattacks. MITRE has documented a common taxonomy of attacks and makes it easy to communicate them across various cybersecurity vendors. As a result, cybersecurity practitioners can better design a comprehensive strategy for security controls to defend against likely threats and prioritize security incidents that need to be mitigated to reduce business risks.
For more details read the Infoblox whitepaper on this topic.