DNS provides extensive insight about what’s actually happening on your network—whether on-premises or in your hybrid, multi-cloud environment. When (and not if) you’re attacked, your ability to effectively lessen the impact depends on automated, real-time detection, visibility, threat context, triage, communications and quick defensive action. Yet for many companies, it takes an average of 197 days—over 6.5 months—just to identify a breach and another 69 days on average to contain it (Ponemon Institute, 13th annual Cost of Data Breach Study, 7/11/18). But with DNS, real-time network data is already available on your network, so the key begins with discovery, context and how to access it.
Complicating matters is the rapidly expanding threat surface and increase in bad actors seeking to infiltrate networks and extract sensitive information. Users are now accessing cloud applications anytime, anywhere through an escalation of devices. Remote and branch offices with direct Internet access are seldom fully protected by the headquarters security suite. And endpoints, like lightweight IoT devices, are susceptible without robust endpoint security.
While DNS threats and attacks are growing, Infoblox Reporting and Analytics, integrated with core network services, can make security threats visible in real-time for quick response and remediation. While an exhaustive threat review is out of scope, this blog focuses on detecting three major attacks—DNS NXDOMAIN / NOERROR, Malware and Tunneling and DNS RPZ violations—to help you better protect your infrastructure and data.
DNS NXDOMAIN / NOERROR
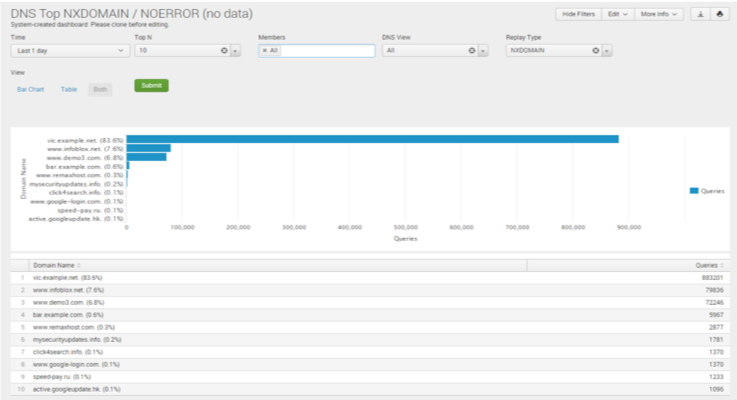
DNS attacks target network infrastructure to compromise availability. A barrage of DNS queries can quickly fill-up the DNS server cache with non-existing domains. When filled, the network grinds to a halt and legitimate queries don’t get answered quickly, if at all.
The Infoblox Reporting & Analytics NXDOMAIN / NOERROR report helps network teams quickly identify problems with domains or clients that have been mistyped, misspelled, misconfigured, renamed, changed, expired or removed by showing live queries actively seeking the target. For security teams, this report identifies when a client is doing something harmful on the network. For example, data exfiltration malware might use a domain name generation algorithm, searching among thousands of generated names to find one active attack vector. This generates a lot of NXDOMAIN activity, filling-up the cache and degrading server response to legitimate queries.
The NXDOMAIN / NOERROR report is a standard report available through the DNS Dashboard and requires Advanced DNS Protection (ADP). Filtering is robust, flexible and intuitive making it quick and easy to get the needed information. Flexible configurations can be set for monitored timeframes, data displays (e.g., from visualized bar charts to raw data tables), top domains identified, filtration by members, DNS views and more. The Splunk interface allows a view of the raw dataset, and custom dashboards or reports can be created without starting from scratch. All of this gives you quick visibility to see a troubled or malware-infected domain rather than getting caught long after the damage is done.
Top Malware and DNS Tunneling by Client
This report lists clients with the most outbound queries (via Response Policy Zone (RPZ) hits) and DNS tunneling activities in a given timeframe. For network and security teams, it identifies the top infected clients making outbound malicious queries. It also identifies IP addresses tied to DNS tunneling, helps prioritize DNS security efforts to prevent malware spread and damage and reveals bad actors trying to remove data from the network.
This report requires BloxOne™ Threat Defense and is accessed through the Security Dashboard. A variety of filters are available. BloxOne Threat Defense displays the top client IP culprits, the number of associated tunneling events, the number of malicious queries and the date/time last seen. The admin can drill down for historical data, sort by the top number of queries, the most recent, or most prolific to identify and arrest bad actors engaged in malware or data exfiltration activities.
DNS Top RPZ Hits
The DNS Top RPZ Hits report shows which clients have the most malicious activities using threat intel RPZ rules defined through BloxOne Threat Defense. Network admins need to know which clients are conducting harmful DNS network queries for monitoring and pre-emptive action. Security admins need to identify malicious real-time and historical clients and domains to cut response time for damage mitigation and resolution.
This report is also located through the Security Dashboard and utilizes BloxOne Threat Defense. Powerful search and flexible filtering can quickly parse the domains that are of major concern to initiate virus scans or further action by the security team. This report can also be saved to run automatically at regular intervals, and if rules are violated, it can be programed to trigger alerts, transfer processing files, run scripts, send emails, share data with the security ecosystem and more.
These DNS security reports are just a sampling of the over 100 customizable dashboards and reports available to increase network visibility, protect your data and infrastructure, automate and better manage network security and operations. For more information, see our recorded Reporting & Analytics Security Visibility webinar and download your copy of the Sample Report Guide. You can also contact your Infoblox sales rep or reseller to learn how Infoblox can further help you address your network visibility and reporting needs.





