Protective DNS Challenges
Preemptively blocking connections to threat-related domains is a highly attractive opportunity for security teams of all sizes—one also promoted by standardization bodies like the National Institute of Standards and Technology (NIST), with the latest version of NIST Special Publication (SP) 800-81 Revision 31 serving as a key proof point.
The technology enabling this, Protective DNS (PDNS), is still relatively new—especially when compared to more established security solutions such as network firewalls, antivirus software and identity management systems. Today, many security teams have limited exposure to PDNS and lack the experience needed to fully operationalize its benefits—particularly its ability to deliver early, large-scale threat prevention.
Let’s explore why adopting PDNS remains challenging—and how security teams can accelerate its deployment for quick wins.
Roadblocks to Protective DNS
There are several reasons why security teams struggle to get into PDNS. Here, an overview:
- Lack of DNS Expertise: Most security teams are trained in traditional technologies like vulnerability management, endpoint protection, firewalls and SIEM—but have rarely had the opportunity to dive deeply into DNS. They often rely on network teams to manage this part of the IT stack. Concepts such as DNS record types, resolution processes and protection mechanisms are typically discussed during initial infrastructure setup but are often overlooked afterward. Adversaries are aware of this knowledge gap and register millions of domains each year—often with a lifespan of just one day—to evade detection.
- Reliance on Tactical Tools: Many security teams are locked into existing tools that focus on detecting malicious content or payloads as they arrive at their doorstep. Their expertise tends to develop heuristically around known attack patterns at the point of impact. Pre-attack knowledge and trends—such as how threat actors set up infrastructure—remain a less favored topic. Consider this: the MITRE ATT&CK framework includes 12 post-delivery attack tactics (from initial access through impact) and hundreds of sub-techniques, but only two pre-attack tactics and fewer than 20 related sub-techniques.
- Long Implementation Cycles: PDNS initiatives are often stalled by the time-consuming process of redesigning network traffic flows, which can delay or derail projects. Networking teams frequently have to request changes months in advance and are often given minimal time windows to implement them.
- Fear of False Positives: New enforcement layers always carry the risk of service disruptions caused by false positives. At scale, solutions like PDNS may amplify these concerns, especially in organizations with low risk tolerance.
The combination of all these roadblocks makes PDNS less attractive to decision-makers. Most importantly, it creates a catch-22: with fewer resources allocated, the ROI remains unclear—pushing PDNS projects lower on the priority list during resource planning.
Protective DNS Isn’t Binary; It’s a Journey
To overcome these blockers, a systematic, step-by-step approach can help. Why use a spectrum? Because PDNS isn’t binary. Like many other technologies, PDNS requires time and organizational maturity to implement effectively. Additionally, today’s security market is saturated with various solutions, each claiming some level of PDNS functionality—yet often lacking the depth and effectiveness needed to support real-world use cases. As a result, it becomes increasingly difficult for security decision-makers to determine which tools to adopt and how to do so effectively.
An alternative approach is to frame PDNS as a maturity journey—enabling initiative-takers and project managers to help organizations identify the right solution based on their size, goals and current capabilities.
Here’s a simplified overview of how to effectively roll out PDNS:
Step 1: Run a Time-Limited, One-Time Assessment by an External Expert
This approach helps organizations quickly uncover previously unknown risks within their network. More importantly, visibility into these risks initiates high-level conversations among decision-makers and highlights the potential benefits that PDNS can offer. In simple terms: tell me what I don’t know.
Step 2: Initiate Continuous Monitoring to Feed SecOps
Once the risks are understood, the organization can greenlight the exposure of PDNS to security and network operations teams. During this phase, PDNS should be enabled in detection mode, providing continuous threat detection events to monitoring and analytics functions such as SIEM. Key results include new insights into which assets are at risk, when and why. Security teams can use this data to track threats and correlate findings with existing tools.
This step offers different users distinct insights. SOC analysts gain access to valuable new threat signals, enhancing decision-making through deeper visibility into DNS-layer activity. Detection engineers can use this phase to identify gaps in existing detections and improve coverage.
Most importantly, by continuously uncovering and trending previously unknown risks, organizations build confidence in the data and develop a clearer understanding of their threat landscape.
Step 3: Activate Preemptive Security for Confirmed Malicious Domains
After security teams gain confidence in the risk signals, specific blocking policies can be enabled using response policy zones. This powerful DNS security mechanism allows network and security administrators to modify DNS query responses based on custom policies—enabling real-time blocking, redirection or logging of potentially malicious or unwanted domain lookups.
This phase allows organizations to begin experiencing tangible benefits, such as a reduction in the number of security alerts and elimination of time-consuming incidents. Network teams may also observe improvements in traffic quality and performance.
Step 4: Expand Blocking and Optimize Controls
As the organization gains experience in preemptively blocking threats, PDNS policies can be expanded. This phase may also enable consolidation or replacement of outdated security controls—such as hard-to-manage access control lists or redundant endpoint policies—leading to a more efficient security architecture.
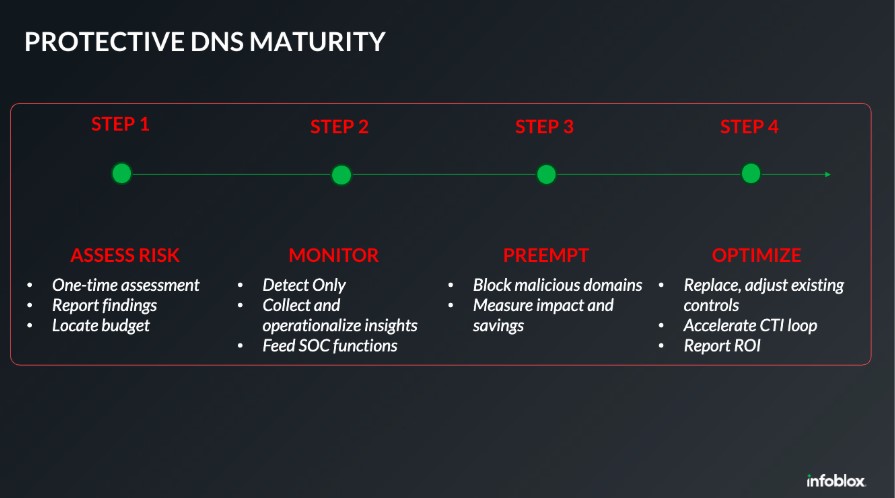
Figure1. Protect DNS maturity with steps and tasks
Example Detections Accelerating the Adoption of PDNS
Continuous monitoring using detection-only mode (step 2) plays a critical role in the successful adoption of PDNS, as new threats can be detected without requiring major changes to the infrastructure. A strong example of such threats is the detection of DNS-based command-and-control (C2) traffic.
Due to the widespread use of DNS tunneling tools—legit and malicious—many security teams struggle to effectively monitor and control DNS traffic for C2 traffic. While next-generation firewalls or secure access service edge (SASE) type technologies have some capabilities to detect DNS tunneling, several complexities remain. Content delivery networks, usage of new lookalike domains and the expansion of legitimate DNS C2 tools complicate the detection and blocking of all C2 activities.
To address this challenge, PDNS solutions that leverage predictive threat intelligence—actively tracking threat actors and their infrastructure—are essential. Powered by this intelligence, PDNS provides security teams with a precise scalpel for detecting C2 activity, rather than relying on broad, reactive measures based on previously known attacks.
As DNS tunnels are detected, many security decision-makers and practitioners immediately see the value. A key reason is that understanding and mitigating DNS tunneling is vital for protecting enterprises and meeting compliance standards like the Payment Card Industry Data Security Standard (PCI DSS), Health Insurance Portability and Accountability Act (HIPAA) and General Data Protection Regulation (GDPR).
Infoblox Threat Defense™ makes detection of C2 and many other threats easier by offering a detection-only mode only that does not require any changes to existing network architectures, eliminating time consuming network redesigns or possible service interruptions.
The new insight also helps demonstrate the potential impact of enforcement, making the transition to active blocking more acceptable. Most importantly, detection-only mode provides a foundation to clearly articulate the ROI of PDNS by showing measurable security value without disrupting operations.
Learn More about Infoblox Threat Defense
PDNS is not a binary, on-off solution. Given its relatively recent emergence in the security technology landscape, it requires a step-by-step adoption approach. By following a phased roll-out model, organizations can efficiently realize the full benefits of PDNS by leveraging existing resources and gradually integrating it without major investments.
To learn more about Infoblox’s PDNS solution, Threat Defense, and how to leverage detection-only mode, visit the Infoblox website or contact one of our specialists. New to PDNS? Request a DNS workshop here.
Footnotes
- NIST Special Publication (SP) 800-81 Revision 3: Secure Domain Name System (DNS) Deployment Guide, Rose, Scott, Liu, Cricket, Gibson, Ross, National Institute of Standards and Technology (NIST), April 2025








