This is the third in a three-part, in-depth report covering nearly a year of research into VexTrio. To learn more about the people and entities involved, see the first part here. To learn about VexTrio’s activities, see here. VexTrio domains and references from this research can be found in our GitHub repository.
In the first two parts of this research, we’ve shown that VexTrio is a large enterprise with roots going back over two decades and a long history of spamming and scamming. While the key figures are involved in dozens of micro-companies around the world, their businesses are concentrated in the online advertising industry. Their traffic distribution systems (TDSs) handle billions of transactions a day with little delay. How does it all work in the background? Check out Figure 1 for a glimpse of what you’ll see in this installment of our research.
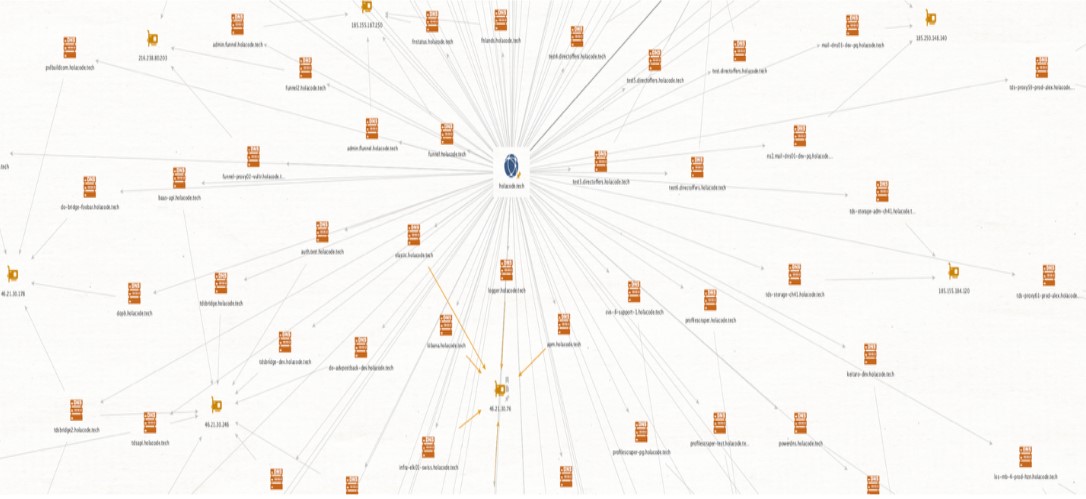
Figure 1. A bird’s eye view of VexTrio’s infrastructure
We used Domain Name System (DNS) records to uncover both VexTrio’s main commercial entities and the tech stack that supports their operations. They operate a resilient, fault-tolerant infrastructure to support their TDS plus a global infrastructure for their spamming and scamming activities. Perhaps to their downfall, they also use those same IP ranges to host websites for dozens of other businesses they are involved in.
In addition to the infrastructure they have developed, VexTrio relies on third-party tools such as Binom and Keitaro to optimize their campaigns and hide their activity. We will detail an example of how a push notification on one of our personal devices led through RollerAds to a VexTrio Binom server and on to a scareware scam. In that example, Binom is used both to funnel victims to specific content based on user characteristics passed by RollerAds as well as a campaign tracker to monitor traffic flows.
While trackers can be used as cloakers, VexTrio uses dedicated cloaking software to hide their links in specific mediums, specifically social media. They primarily use IM KLO, an underground cloaker known for its effectiveness at disguising malicious Facebook ads and bypassing security checks.
Finally, we expose an Achilles’ heel in the infrastructure that also illustrates the scale of VexTrio’s operations. They use a handful of domains to deliver core images for all their activities; if these come down, the resiliency will be lost. The popularity of these domains is remarkable: one of them ranks in the top 10,000 domains worldwide, both as measured by our own DNS resolvers and by Tranco, a widely referenced domain popularity service. For example, the VexTrio content delivery network (CDN) server imghst-de[.]com is far more popular than openvpn[.]com.
The primary motivation to release this material is not to document the ins and outs of VexTrio, but to highlight the core functionality of malicious adtech. While VexTrio is a big player in the industry, they are not the only one. We track several other groups who are making a fortune off preying on innocent people worldwide. Malicious adtech is not only involved in a massive scam industry, but it is used to deliver malware such as information stealers that are connected to enterprise breaches. By outlining how VexTrio’s technology works, we hope to spur research by others into every member of the adtech industry. Let’s find out: Are they abused, negligent, or complicit?
We have included numerous links to supporting evidence throughout this paper. All these hyperlinks were active in early July 2025. Names, domains, and companies may appear in this report only because of technical or business link to VexTrio; their mention alone does not mean they knew of or took part in any wrongdoing. Specific illegal activity claims are explicit and backed by cited evidence.
The Infrastructure
To operate a reliable TDS, your infrastructure must be flexible and able to relocate at a moment’s notice; this is especially true if you might be caught using the TDS for malicious purposes. Because so much of VexTrio’s TDS is hidden behind Cloudflare and transparent proxies, the discovery of Los Pollos as the source for the infamous VexTrio URLs was a huge break that allowed us to unravel a large portion of the infrastructure.
While perusing passive DNS, we noticed an A record for www.lospollos[.]com with IP addresses (not Cloudflare!) of 46[.]21 [.] 30 [.] 248 and 185 [.] 155 [.] 186 [.] 48 from AS5398 in Switzerland advertised via Internet One/C41. We had previously identified AS5398 as almost exclusively dedicated to VexTrio but were confused by the handful of seemingly legitimate businesses in the range, including some online stores and even a ski resort. After digging into the corporate records with our collaborators at Qurium, we knew these innocent-looking establishments were connected to key VexTrio figures. With our new understanding of AS5398 and others we were watching, we used historical DNS records to connect domains and analyze their purpose.
Further digging into the border gateway protocol (BGP) announcements of AS203639 and AS5398 led us to multiple prefixes—and a truckload of passive DNS uncovering their infrastructure operations. Figure 2 shows some of the many related domains found through BGP and DNS analysis. Mixed in with the masses of scam website domains were holacode[.]tech and holaco[.]de, which we knew were associated with HolaCode, a software development arm of VexTrio. These records also revealed hostnames of the key DevOps infrastructure required to run a global malicious adtech network.
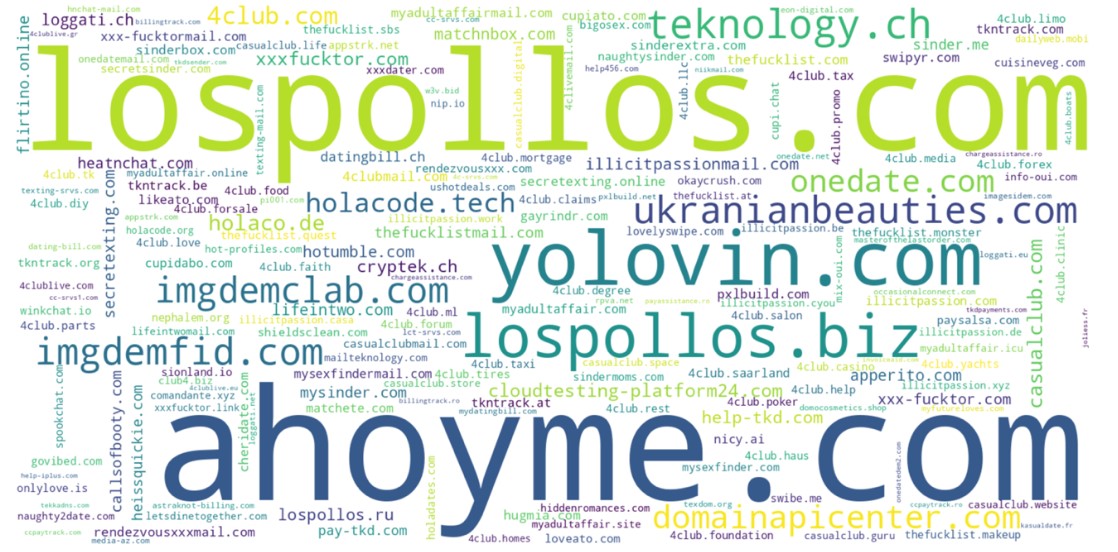
Figure 2. Domains resolving in dedicated VexTrio IP ranges over time scaled by volume of DNS queries
As we continued exploring passive DNS collections, the VexTrio TDS infrastructure became visible. We were able to identify their scam sites, CDN, DevOps dependencies, and even which hosting providers they use. Surprising to us, the global operation utilizes only a few hundred virtual machines (VMs) across one data center and a handful of hosting providers. VexTrio’s core infrastructure is largely hosted in Cloudflare, which hinders analysis of related domains. But pulling the thread on corporate structures, the scamming and spamming activities, and leveraging historical passive DNS records, we obtained a solid understanding of how this malicious adtech works—and gained insights into how to approach analyzing other malicious TDS networks.
DevOps
To scale a TDS that can handle billions of transactions a day, automation is a must. DNS hostnames revealed the use of Hashi Corp software (Terraform, Consul and Vault), Kubernetes, Proxmox, Gitlab and Argo, as well as other popular automation tools. Combine this technology with a whole lot of nginx, HAProxy, mail cannons, and a CDN, spread it across a data center, Hetzner, AlexHost, and Cloudflare, and you have yourself a resilient TDS. See Figure 3 for a list of subdomains that tell this story.

Figure 3. Subdomains seen in the VexTrio-related domains reveal information about their technology stack
We also found that VexTrio uses PowerDNS, a popular and highly advanced open-source DNS software. This software supports authoritative and recursive DNS, as well as load balancing and geo-restricted resolution. Because of the nature of their business, in which domains that are used directly for scams and spam are continually reported to registrar abuse desks or blocked in protective DNS systems like our own, VexTrio needs DNS software that can handle their rapid zone changes: PowerDNS offers that.
Figure 4 shows how core VexTrio infrastructure tied to holacode[.]tech, including domain names and hosting, was configured as of July 2025.
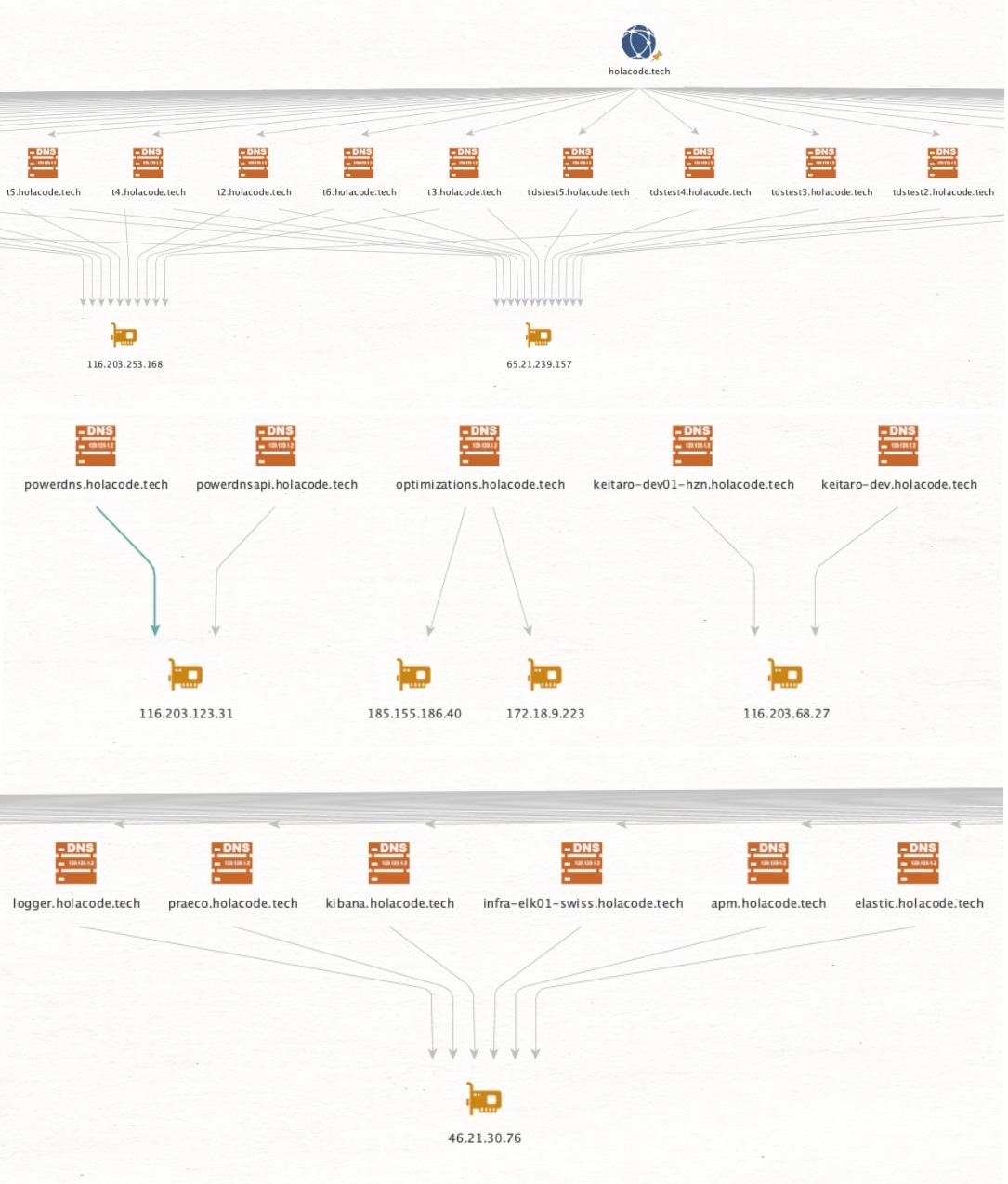
Figure 4. Identifiable DevOps infrastructure visible across the VexTrio network as of July 2025
Binom Tracking at a Glance
Tracking is a critical component of the adtech industry. It is used to ensure that all the players are counting fairly. Advertising, particularly shady advertising, is a “Zero Trust” environment. The reality is that although publishing affiliates, adtech platforms, and advertisers all need each other to succeed, they also know that there is a lot of cheating in the industry; trackers provide an external monitor on transactions. Adtech companies and advertisers use trackers to detect fake (bot) traffic from publishing affiliates and publishing affiliates use trackers to detect “shaving” by the adtech companies. Both publishers and advertisers also use trackers to analyze their campaigns to determine the return on investment. Finally, many trackers are used to provide lightweight cloaking because they can redirect users to decoy pages under criteria set by the owner.
Everyone who is trying to make money in advertising uses trackers. VexTrio is no exception to this. They not only run advertising networks, but they are also publishing and advertising affiliates to other adtech networks, such as RollerAds, Propeller Ads, Push House, and RichPush. In other words, a Los Pollos smartlink may pass traffic not only to a landing page, but also to another advertising network, such as Partners House, and vice versa. We’ll show a specific example of this later in this section.
VexTrio promotes several advertising trackers via LosPollos, including Binom, Keitaro, Voluum, and AdsBridge. Our analysis revealed that VexTrio uses self-hosted commercial tracking software from some of these companies to monitor their campaigns within partner networks. We have investigated VexTrio’s use of trackers extensively.
Binom is a self-hosted tracker that VexTrio uses extensively. Binom was created by a team of Russian affiliate-marketing professionals led by founder and CEO Roman Ignatiev. When a Binom server registers a visitor, it logs each click, impression, and conversion. These detailed records serve several purposes: they allow VexTrio to calculate precise payouts to traffic sources, fine-tune advertising campaigns, and defend against inflated bills from affiliate networks. Binom boasts very fast redirection, built-in cloaking, and bot detection. They also offer landing page protection to prevent competitors from stealing campaigns.
Binom writes user actions and events to its own database in milliseconds and has built-in deduplication logic that prevents double counting. By adopting Binom, VexTrio offloads tracker development to a best-in-class, fully featured platform that already includes an intuitive UI for real-time campaign stats. Furthermore, Binom can capture extra advertising data that isn’t available in a visitor’s HTTP request or web browser. As an example, our analysis showed that RollerAds passes important demographic information about the user to VexTrio, including the user’s age group. Binom normalizes this custom data when it writes to its database, letting VexTrio deliver more targeted content to users and helping them simplify later analysis. Finally, rule-based routing can send each visitor to the most relevant landing page, so it functions not just as a tracker but also as a cloaker and TDS.
In fall of 2024, we self-infected a mobile device by visiting compromised websites, and then captured the push notification traffic that resulted over several months. As an example, and illustrated by Figure 5, clicking on one notification that we received led us to the RollerAd TDS (pr3tty-fly4[.]com), which captured various information about us, including the age group and browser name. Then, RollerAds passed our data to a Binom server (hktrk[.]com), dedicated to Hey Kraken!, via the URI parameters (Hey Kraken! is a VexTrio-owned mobile app marketing agency). Finally, Hey Kraken! used the technical and behavioral details about us to serve antivirus scam.
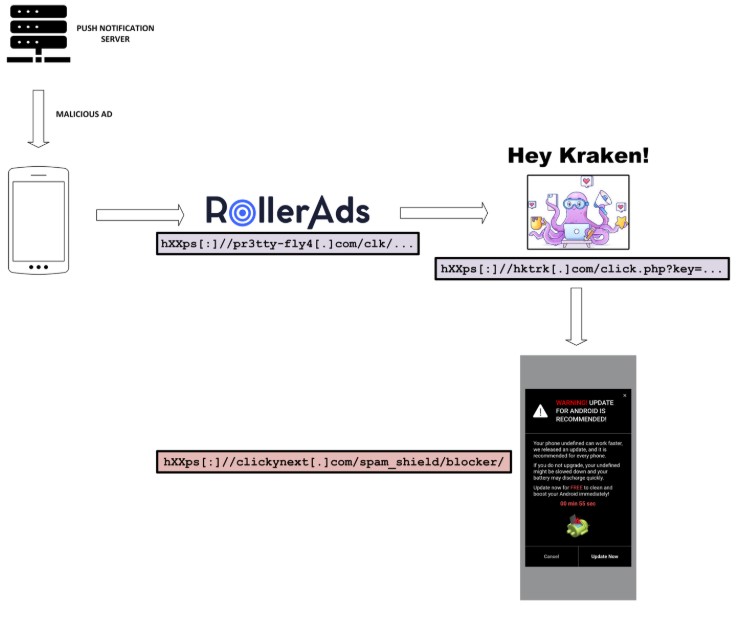
Figure 5. A push notification from an infected phone redirected user to the Binom tracker for Hey Kraken!, a VexTrio company, and on to a scareware page
VexTrio dedicates two IP addresses to its Binom tracking servers; both in OVHcloud. As of July 2025, there were 78 unique domains configured on these servers and several million A record queries recorded in passive DNS, likely a small fraction of the true total web traffic. Figure 6 shows a tree map that groups the tracker domains by their registrars and associated top-level domain (TLD). The size of the domain square is scaled by its age (i.e.,creation date). The domain registration details correspond to the period when VexTrio owned the domain. Most VexTrio Binom domains were registered after 2020. One of Vextrio’s oldest Binom domains, lpmbtrk[.]com, was created in June 2017.
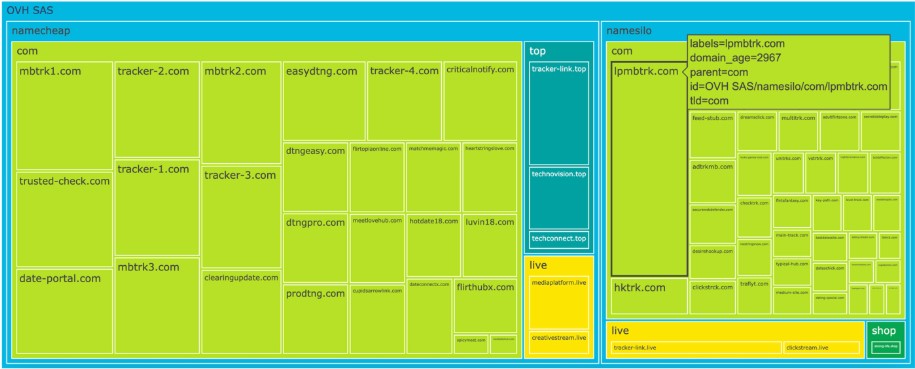
Figure 6. VexTrio’s Binom tracker domains and their respective first-seen dates and query volume according to passive DNS
VexTrio leverages Binom not only for advertising analytics but also to steer victims toward malicious landing pages. The VexTrio developers have configured Binom tracker rules so that they can route users to tailored scams based on their profiles, which include data points such as age group, browser type and version, device operating system, and geolocation. Similar to the IP addresses for Binom tracking, we’ve identified two dedicated servers for VexTrio’s Binom landing pages. Figure 7 shows 55 unique landing page domains across IPs managed by Hetzner and Petersburg Internet Network Ltd. We have seen approximately 6 million DNS queries to the domains. The size of their names in the graphic corresponds to their relative DNS query counts. The names also align with the scams’ themes, which are either related to dating or antivirus scams. Some of these domain names also correspond to the fraudulent apps we covered in part one of this research.
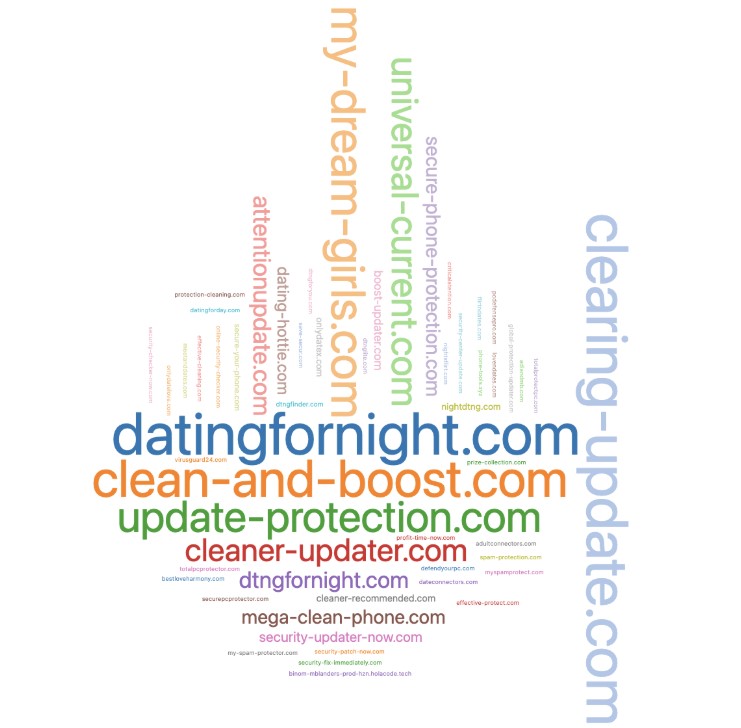
Figure 7. Domain names used in VexTrio Binom landing pages. The names align with their antivirus and dating scam verticals.
Cloaking Capabilities
While VexTrio uses trackers to cloak some of their activity, they also use dedicated cloakers, particularly in social media campaigns. The primary cloaker that VexTrio uses is called IMKLO; one of the main developers of this software is Dmitri Jesipow, who is also the CEO and founder of the IM GROUP (see Figure 8). This organization developed and sells several programs, including IM Klo, IM Comments Cleaner, MaskFb, and Keyof. These software and services are designed to help disguise malicious ads from security groups. They help them evade detection from security systems that find malicious advertisements. They also reveal why a campaign was rejected on platforms such as Facebook, letting affiliates tweak their creatives and potentially slip past Facebook’s fraud review filters. Other tools remove negative comments against their Facebook and Instagram posts, or help filter out inbound bot traffic and security scanners.
![Figure 8. Dimitri Jesipow’s vk[.]com account page. He is the main contact for IM Klo, IM Comments Cleaner, and MaskFb.](https://blogs.infoblox.com/wp-content/uploads/inside-the-robot-deconstructing-vextrios-affiliate-advertising-platform-fig-8.jpg)
Figure 8. Dimitri Jesipow’s vk[.]com account page. He is the main contact for IM Klo, IM Comments Cleaner, and MaskFb.
Kill Switches in the Network
VexTrio’s internet infrastructure is expansive and highly heterogeneous, showing a wide variety of naming conventions across its domains, technologies, and selection of network service providers. This acts as a natural barrier against the security community’s threat analysis and attribution efforts. However, just like any other large network, VexTrio also needs some measure of centralized management to coordinate and control their operations. We’ve determined that some of their CDN domains are vital to the vertical campaigns, and if they are unavailable, most of the space would become inoperable.
VexTrio therefore allocates extra budget to these key resources. For example, one of their CDN domains imghst-de[.]com uses Cloudflare’s CDN and is protected by their proxy services; see Figure 9. We suspect that the domain’s account is enrolled in a CloudflarePro plan due to the large volume of DNS queries it receives. The pro tier offers extra security features not available in the free version, including web application firewall (WAF), advanced bot traffic filters, and security analytics. Additionally, it gives the account additional performance features such as image optimization and more advanced caching rules. This can improve how Cloudflare’s edge nodes optimize (e.g., compress) PNG images and deliver them through the CDN.
![Figure 9. Cloudflare check tool indicates imghst-de[.]com is behind Cloudflare’s CDN](https://blogs.infoblox.com/wp-content/uploads/inside-the-robot-deconstructing-vextrios-affiliate-advertising-platform-fig-9.jpg)
Figure 9. Cloudflare check tool indicates imghst-de[.]com is behind Cloudflare’s CDN
We’ve also identified an unnamed VexTrio affiliate that has been operating a very large dating scam campaign for over five years (uses smartlink parameters u=f8cpd0x and o=mfekrzb). The lifeline of these campaigns is eight CDN domains that serve operationally critical resources to victims. The CDNs return JavaScript responsible for dynamically loading text based on the victim’s browser preference language (e.g., trls.js), push notification subscription functions (e.g., push-subscriber-v2.js), hijacking the browser back button (e.g., backoffer.js), and other file resources for the victim’s client to properly load the scams. Its digital footprint is similar to VexTrio’s, and it is likely they both have access to the same codebase. Figure 10 shows the CDN domains and their CNAME records that point to Akamai’s edge hostnames. Like Cloudflare’s pro tier, Akamai CDN is built on a globally distributed network of edge servers, deployed across thousands of points-of-presence (PoPs), enabling rapid, large-scale content delivery. These Akamai edge servers ensure fast delivery of scams to victims.
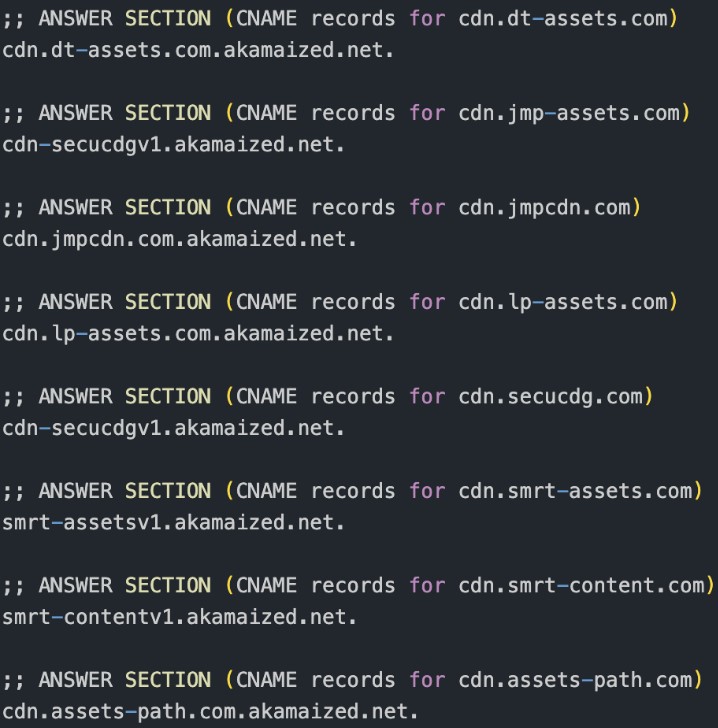
Figure 10. VexTrio CDN server domains showing Akamai edge hostname CNAME DNS records
Although the CDNs have been used for years, they register little to no detection by antivirus engines or threat intelligence platforms such as VirusTotal. As Figure 11 illustrates, VexTrio’s CDN imghst-de[.]com has accrued only a single VirusTotal flag—even though it ranks among the top 10,000 sites for web traffic, both by Infoblox calculations and the Tranco list. Because it has been active for more than five years and is “popular,” it has ended up in several security industry allowlists.
![Figure 11. VirusTotal shows only one red flag for VexTrio’s CDN imghst-de[.]com](https://blogs.infoblox.com/wp-content/uploads/inside-the-robot-deconstructing-vextrios-affiliate-advertising-platform-fig-11.jpg)
Figure 11. VirusTotal shows only one red flag for VexTrio’s CDN imghst-de[.]com
Using Infoblox’s DNS popularity index, we ranked CDN endpoint domains according to their popularity. Drawing on DNS traffic collected between June 13, 2025, and July 13, 2025, we identified the popularity level they achieved during that 30-day window. The results were striking, to say the least. VexTrio’s CDN domain imghst-de[.]com is as popular as the Google search engine for Turkmenistan and more popular than OpenVPN, one of the world’s most widely used open-source VPN protocols. This implies that VexTrio’s network can reach millions of users within a matter of days, giving threat actors a powerful channel for distributing malicious content. Our data aligns with the Tranco ranking of popular internet domains. Figure 12 compares the Tranco positions of imghst-de[.]com and jmp-assets[.]com with familiar household sites. imghst-de[.]com even outranks nick[.]com, Nickelodeon’s portal for kids’ videos and games, and the CDN draws significantly more traffic than technologies like foxcloud[.]net (cloud hosting) and hotelwifi[.]com (hospitality tech). Table 1 provides a list of CDN domains that VexTrio and an affiliate use.
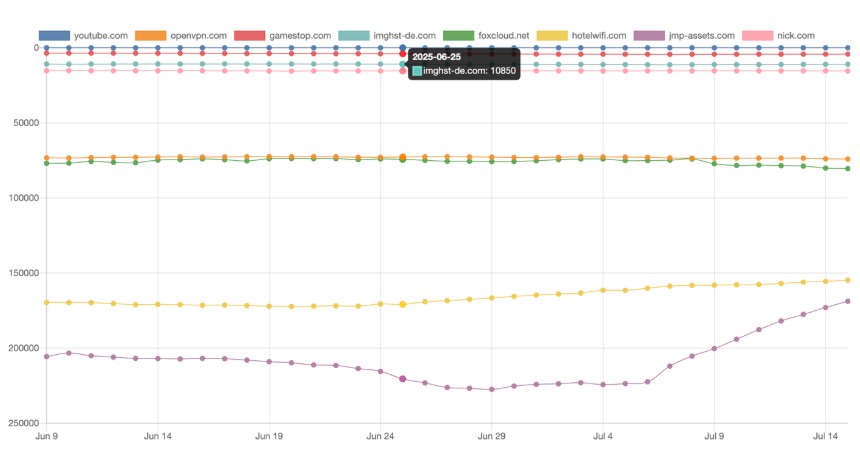
Figure 12. Popularity of the CDN domains according to Tranco’s website popularity index
| Domain | Registrar | Name Server |
|---|---|---|
| imghst-de[.]com | NameCheap | Cloudflare |
| dt-assets[.]com | Amazon | Amazon |
| jmp-assets[.]com | Amazon | Amazon |
| jmpcdn[.]com | Amazon | Amazon |
| lp-assets[.]com | Amazon | Amazon |
| secucdg[.]com | Amazon | Amazon |
| smrt-assets[.]com | Amazon | Amazon |
| smrt-content[.]com | Amazon | Amazon |
| assets-path[.]com | Amazon | Amazon |
Table 1. CDN domains used by VexTrio and a major affiliate
We started this story with an old quote from an online user called Lex Tutor,
“Everyone knows that eliminating spam is impossible to achieve, until an ignorant person who doesn’t know this comes along and starts sending some (Italian) spammer to jail. <beg>”
Thank you, Lex, whoever you are, for putting all that detail in writing so long ago. It was one of the many pieces to the puzzle we found online. We’ll finish with our own quote:
Everyone knows that eliminating malvertising is impossible to achieve, until an ignorant person who doesn’t know this comes along and starts outing the criminals behind it, encouraging others to join in the fight. <beg>